Marvis
New columns on the MQL switch list
We have added the following two columns to the switch list invoked by Marvis query:
- Role: Displays the switch role.
- Managed: Indicates whether the switch is managed by Mist or not.
To view these columns, run a Marvis query to list the switches by using the Ask a Question feature on the Marvis > Marvis Actions page, as shown below.

Simplified Operations
OAuth 2.0 based webhooks
We have introduced OAuth 2.0 support for webhook authentication.
If you enable OAuth 2.0, the Mist cloud will act as the OAuth 2.0 client and will authenticate against an authorization server to get a token. The token will then be added to the Webhook Authorization Headers.
Mist supports the following two ways (Grant Types) of requesting access tokens from the customer system:
- Password-based: If you select this method, you need to provide the username and password of the resource owner.
- Client Credentials-based: If you select this method, you need to specify the Client ID and Client Secret provided by the OAuth IDP.
You can configure webhooks at the organization level (from the Organization > Settings page) or site level (from the Organization > Site Configuration page).

Wireless Assurance
Channel assignment logic update for 6 GHz bands
Radio Resource Management (RRM) now assigns 6GHz radio bands with preferred scanning channels (PSCs) and non-PSC. Previously, RRM would assign the 6 GHz bands PSC only, unless the customer manually enables all channels. The channel assignment logic in 6 GHz bands for different channel widths is as follows:
- For 20 MHz and 40 MHz width, all allowed channels (PSC and non-PSC) are used as the primary channel.
- For 80 MHz and 160 MHz width, PSC channels are used as primary channels.
Through lab testing and extensive deployment verification, we have determined clients generally discover non-PSCs effectively via out of band mechanisms such as reduced neighbor reports or 11k neighbor reports. For this reason, we are happy to amend our guidance around the use of 6 GHz non-PSCs. This should come as welcome news to Europe and areas with 500 MHz of 6 GHz spectrum.
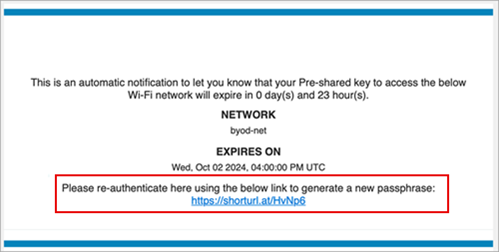
Override the default URL for PSK generation
Mist sends a reauthentication URL to users when the pre-shared key (PSK) to access their wireless network is about to expire. This URL helps users re-authenticate themselves and generate a new passphrase. You can now override this default URL with a custom URL, typically an SSO URL. You can enter the custom URL in the ‘Key Expiration Renew URL’ field on the PSK Parameters Tab on Add/Edit PSK Portal page (Organization > Client Onboarding > Add/Edit PSK Portal). If you configure a custom URL, Mist will include it in the notification email to let the end user know where to renew their PSK. The Key Expiration Renew URL field is displayed only if you select the Send Reminders option.

Here is a sample notification email:
Access point label enhancements
We have improved the access point (AP) label creation workflow by adding an option to multi-select APs to be included in the label. This option is available on the AP label creation page at the organization level (Organization > Labels > Add Label) and site level (Site > Labels > Add Label). To select APs to be included in the label, click the + icon. The AP selection list at the site and organization levels includes a search filter which allows you to filter APs by MAC address or AP name. At the organization level, the AP selection list additionally includes an option to search for APs by specific sites or across the entire organization.
The multi-select option is also available on the New WLAN (Site > WLANs > Add WLAN) and AP details (Access Points > Access Point Name) pages where you select specific APs.

Mist Edge
IPv6 support for Mist Edges
Mist Edges now support configuration of IPv6 addresses. On the Mist Edge configuration page, you can configure IPv6 addresses in the following sections:
- OOBM IP Address: This section provides an additional tab to configure IPv6 addresses. The IPv6 support is available for IP Address, Subnet Mask, Default Gateway, and DNS. We have also added the options to disable IPv4 or IPv6 dynamic addressing.
- Tunnel IP: This section provides an additional tab to configure IPv6 addresses. The IPv6 support is available for IP Address, Subnet Mask, and Default Gateway.
On the Mist Edge Clusters Page, you can configure IPv6 addresses in the existing fields for:
- Radius Authentication Servers
- Radius Accounting Servers
- COA/DM Server
- Tunnel Termination Services
- AP Subnets
- Upstream Resource Monitoring
The IPv6 support is also available for Mist Tunnels on the site configuration page (Organization > Site Configuration).
You can also view the IPv6 addresses on the Insights, Alerts, Marvis Query pages for:
- OOBM interface
- Mist Tunnels
- Radius server
- APs
The following image shows the Mist Edge configuration page with options to configure IPv6 addresses:

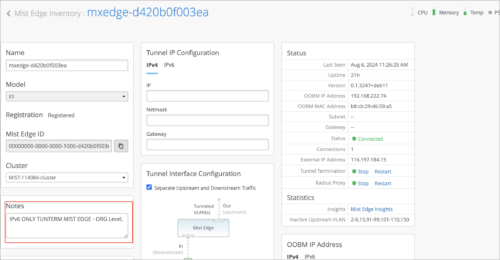
Mist Edge notes
Mist Edges now provide an option to enter device-specific notes. You can use the notes to capture any additional information about the device.
Wired Assurance
IPv6 support for campus fabric
The Mist campus fabric architecture supports configuration of IPv6 addresses for the following switch configuration elements:
- Networks
- Other IP Configuration
- VRF
- DHCP relay or server
- Static Route. The IPv6 support is available for destination and next hop addresses.
- IP and Additional IP Configuration. The IPv6 support is available for IP address and subnet mask.
- L3 interface and L3 subinterface in Port Configuration. The IPv6 support is available for IP address and subnet mask.
Configuration elements like Networks have dedicated fields for IPv6 address configuration, as shown below.

Configuration elements like VRF support IPv6 addresses and IPv4 addresses in the existing IP address field. If you want to configure both IPv4 and IPv6 for such elements, you can save them one after the other.

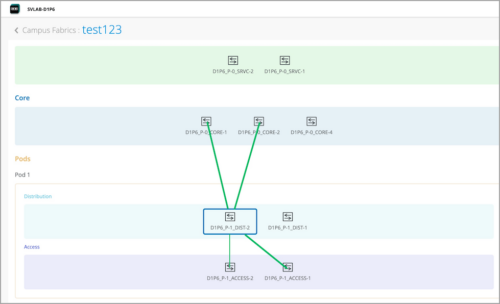
Minimum number of connections between switches in a campus fabric
We have reduced the minimum requirement for the number of connections between member switches in a campus fabric. With this change, you need only one connection between a pod and the core switch. Previously, each distribution switch in a pod had to be connected to all the core switches used. In a core-distribution topology (CRB or ERB), you need only one connection per core and distribution pair. Similarly, in an IPClos topology, you need only one connection between each core and distribution pair and between each distribution and access pair.
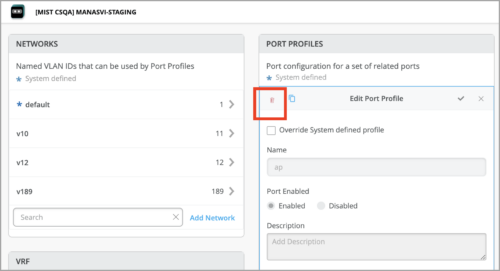
Delete system-defined port profiles
You can now delete the following system-defined port profiles for switches: ap, iot, and uplink.
The delete function is available at the switch template level. You cannot delete the following system-defined port profiles: default and disabled. If you delete the ap, iot, or uplink profile that is used in an existing configuration, that profile will be replaced by the default profile.
To delete a system-defined port profile, open it from the Port Profiles tile in the Switch Template and then click the delete icon.
Locate standalone switches and VC members
Juniper Mist provides an option to physically locate a standalone switch or a Virtual Chassis (VC) member switch. To locate a switch, click the Locate option on the switch dashboard. As a result, the LED on the selected switch blinks for a specified duration. In a Virtual Chassis, you can locate the primary, backup, or linecard members. Only one member can be located at a time. The following image shows the Locate option on a Virtual Chassis dashboard.

Reauthentication interval for switch port profile
In a switch port profile that uses dot1x authentication, you can configure a timer that controls how often a client reauthenticates itself with the RADIUS server. The recommended value is 6 to 12 hours (21600 to 43200 seconds). The default value is 65000 seconds.

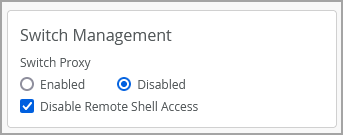
Disable remote shell access to switches and gateway devices
Mist provides an option to turn off remote shell access to the switches and gateway devices in an organization. This setting is available at the organization level. To turn off remote shell access, navigate to the Switch Management tile on the Organization > Settings page and then select Disable Remote Shell Access.
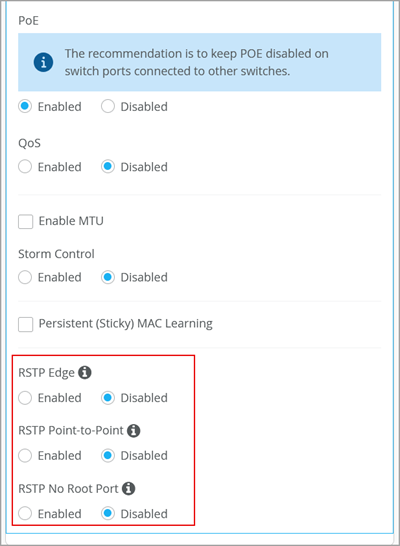
RSTP Edge ports
From a switch port profile, you can enable Rapid Spanning Tree Protocol (RSTP) edge on ports where clients that do not participate in RSTP are connected. An example of such clients could be a PC or a VoIP phone which is not supposed to send BPDUs. These ports are blocked by RSTP if they receive a BPDU from the end client. You should not enable RSTP Edge on the Uplink port. The RSTP edge replaces the base Spanning Tree Protocol (STP) edge in Mist. Mist supports the following RSTP link types at the organization and site template levels:
- RSTP Point-to-Point: This configuration changes the interface mode to point-to-point. Point-to-point links are dedicated links between two network nodes, or switches, that connect one port to another.
- RSTP No Root Port: This configuration prevents the interface from becoming a root port.
Transceiver information on the port list
The port list on the switch dashboard displays the following additional columns to show information about the transceivers connected to the ports.
- Transceiver: Shows the transceiver manufacturer.
- Serial Number: Shows the serial number of the transceiver.
- Transceiver Model: Shows the transceiver model.

Download switch logs via remote shell
For troubleshooting purposes, you can download configuration logs from a switch via remote shell. To do this, use the download button provided at the upper right of the remote shell screen.

WAN Assurance
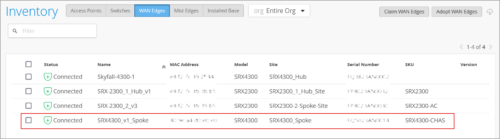
Support for SRX4300 devices
You can onboard, configure, and manage the SRX4300 firewall as a WAN Edge on the Juniper Mist portal. To onboard this device to Mist, use the Adopt WAN Edges workflow on the Inventory page (Organization > Inventory > WAN Edges). Once onboarded, the SRX Series device will be listed on the WAN Edges Inventory page and on the WAN Edges page (WAN Edges > WAN Edges).
Note that SRX4300, SRX1600, and SRX2300 devices must run Junos OS version 23.4R2-S2.1 for Mist support. Additional firmware-suggested releases will be found in the Mist portal.
In the image below, you can find the SRX4300 device listed on the WAN Edges inventory page.
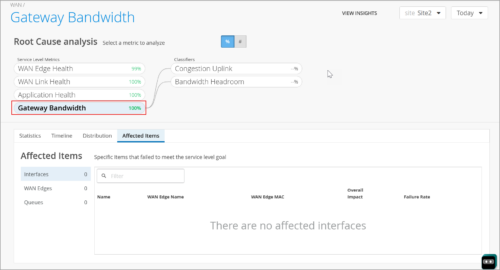
Gateway Bandwidth SLE (SRX)
Gateway Bandwidth SLE tracks the user minutes during which the gateway device bandwidth met or failed to meet a derived threshold. When the Gateway Bandwidth threshold is not met, Juniper Mist sorts the issues into the following classifiers:
- Congestion Uplink: Shows the time (in percentage) during which the Gateway Bandwidth SLE was not met because of congestion on the uplink.
- Bandwidth Headroom: Shows the time (in percentage) during which the Gateway Bandwidth SLE was not met because the bandwidth headroom threshold was breached. Bandwidth Headroom is a learnt estimate of available WAN bandwidth. This is a baseline that represents the highest point of bandwidth usage over the last 14 days. The Bandwidth Headroom classifier is triggered when the current usage exceeds the baseline. The SLE shows the highest utilized queue on the Distribution tab.
Enhancements to Application Path Insights
We have added several enhancements to Application Path Insights to improve the user experience and provide additional path failover details. The key enhancement is a path state bar that shows path state information over a timeline. On the bar, path state events are indicated by segments highlighted in different colors (for example, path up events are shown in green and path down events in red). You can hover over the highlighted portions on the path to view a summary of path state events. If you click the bar, you get an events view which provides additional insight into the path state. The Application Path Insights enhancements also include a summary view of the recent path state events on the left of the screen. Also, the Policies drop-down list now includes active policies (which have seen traffic) and inactive policies (which have not seen traffic) for the selected time range.

Health check for custom applications (SSR)
You can now choose to view the health SLE data only for your custom applications. For example, if you have designated your Point of Sale (POS) devices as custom applications, you might want to view Application Health for only those devices. To do so, go to Monitor > Service Levels, and click the WAN tab. Above the SLE blocks, turn on Show Custom Apps to view the bad user minute data only for your custom applications. Turn off this feature to view data for all applications.

Enhancements to the Session testing tool (SSR)
To help troubleshoot WAN Edge devices, we have enhanced the Session testing tool with options to view the session details and to delete the sessions if required.
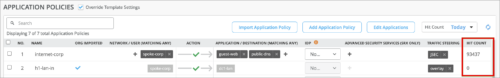
Application Policy hit count
In the Application Policy section on the WAN Edge device page, you can now view the hit count, which indicates the number of Application Policy events for each policy rule. This feature is available for SRX Series devices in this release. For SSR devices, you will see this feature in a future release.
Bounce port testing tool for SSR
Mist now provides an option to run a soft bounce port test on SSR ports. A bounce port test provisionally takes the port down and then brings it back up, causing a port state change within the device. Bounce port does not cause the external physical link to change. The connected devices will not see a link state change.

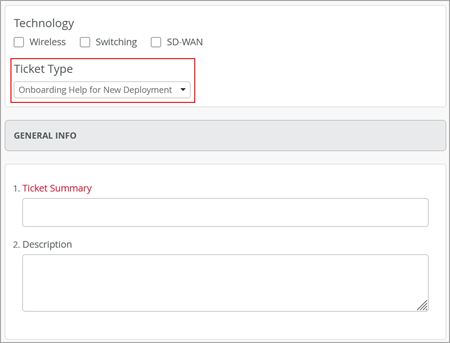
Support
Support ticket for assistance with new deployments
We have introduced a new support ticket type, named ‘Onboarding Help for New Deployment’. Juniper Mist customers can use this ticket to seek assistance with initial setup, configuration, and basic troubleshooting to ensure a smooth deployment. You can create this ticket under the following technology categories: Wireless, Switching, and SD-WAN. The scope of this ticket type does not include network design-related assistance. Tickets of this type need to be scheduled at least 48 hours in advance.