In addition to the 2.4 GHz and 5 GHz radios, our Mist APs also contain a third radio dedicated to scanning. This radio is used for detecting Rogue, Neighbor, and Honeypot APs on both 2.4 GHz and 5 GHz radio bands. This means that regardless of which radios you have enabled on your AP (2.4 GHz or 5 GHz), it will still be able to detect unauthorized APs at any frequency using the scanning radio.
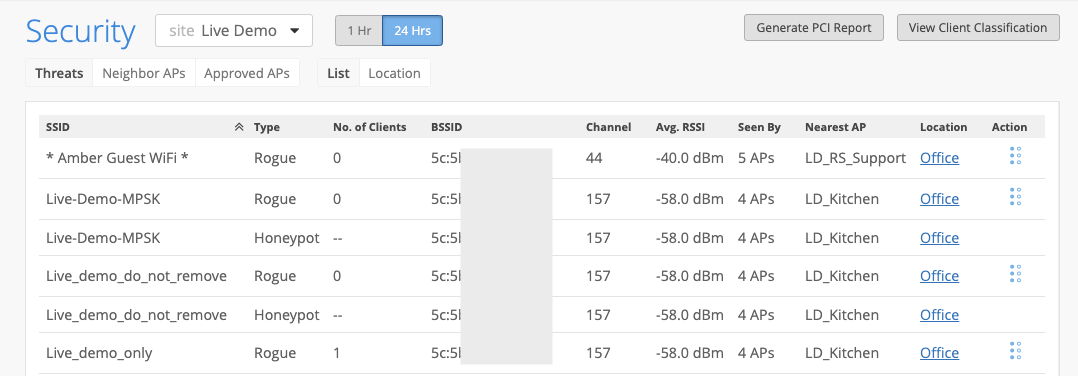
Honeypot APs are unauthorized APs advertising your SSID. A bad guy might be trying to spoof your login screen to capture your password. This is an obvious security risk that should be detected and monitored. Detection of Honeypot APs can prevent such threats to your network and is enabled by default under Site Settings.
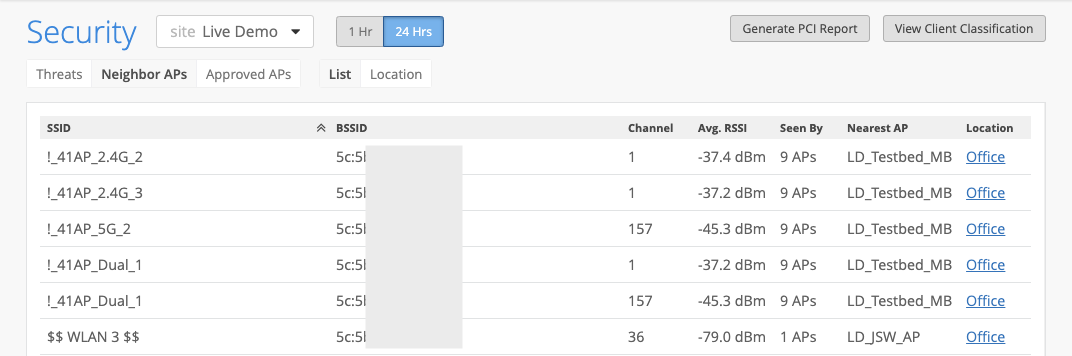
Mist AP’s also scan for unknown APs who are classified as a Neighbor AP. You can set an RSSI threshold as a criteria for detecting these Neighbor APs in proximity of your network.
Rogue APs are defined as any AP not claimed onto your Organization, but detected as connected on the same wired network. Rogue APs share the same Local area network, but are unknown to your Organization.
The Rogue AP detection is disabled by default. Please go to Site Configuration-> Security to enable it. Here you can enter an RSSI threshold value at which APs will be detected as neighbor/rogue. The default RSSI is -80dBm – you may set the RSSI Threshold for Rogue AP detection between -40dBm to -100dBm. Also, set a Time threshold for Neighbor AP detection to prevent getting flooded with “neighbor” APs which only appear momentarily. The AP would need to share the same wired VLAN as the rogue in order to hear it on the wire and perform the rogue correlation.
To prevent sanctioned APs from being identified as Rogue or Honeypot, allowlist the specific SSID and BSSIDs of known access points in the Security Configuration box.
Rogue and Honeypot APs are under the Threats tab and Neighbor APs has its own tab. You can switch between the tabs to view the desired APs.