Documentation Update
Mist Documentation has a New Home
We have moved the Mist documentation to Juniper’s documentation portal. This change will ensure a seamless experience for users by providing a one-stop-shop for Juniper and Mist product documentation.
With this change, all the documentation links on the help menu (?) of the Juniper Mist portal now point to their new locations. This includes Mist Product Updates (release notes), which will move to Product Updates (Juniper).
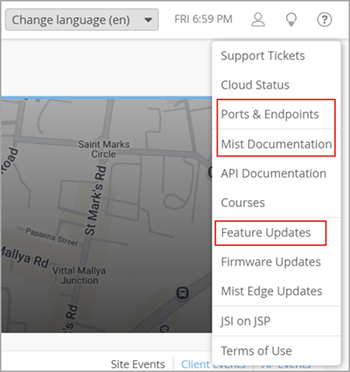
Note that Firmware Updates and Security Alerts remain in their original locations.
Simplified Operations
SSO and MSP support for limited roles
Mist now supports setting up single sign-on (SSO) for users with the following limited roles:
- Switch Port Operator: Can view and manage switch port configurations based on the permission provided by a Super User.
- Super Observer: Monitor-only access to all sites and extended access to the organization pages.
A super user can configure SSO login for users with limited roles from the Single Sign-on tile on the Organization > Settings page.
Support for creating the above restricted roles is now available at the MSP level as well. In addition, the MSP portal supports setting up SSO for these roles.
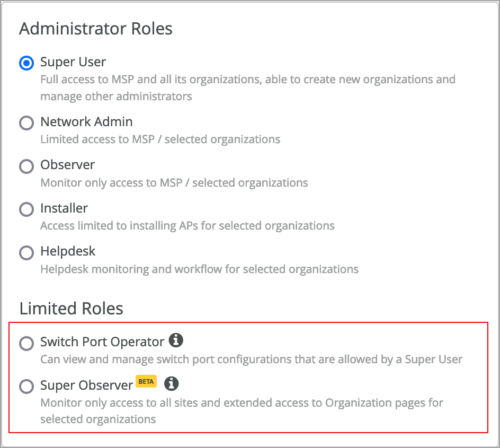
Limited roles, already available in Mist, are used to limit an administrator’s access in the Mist portal to pages pertaining to the tasks they perform. See also: Portal User Roles.
Webhook enhancements
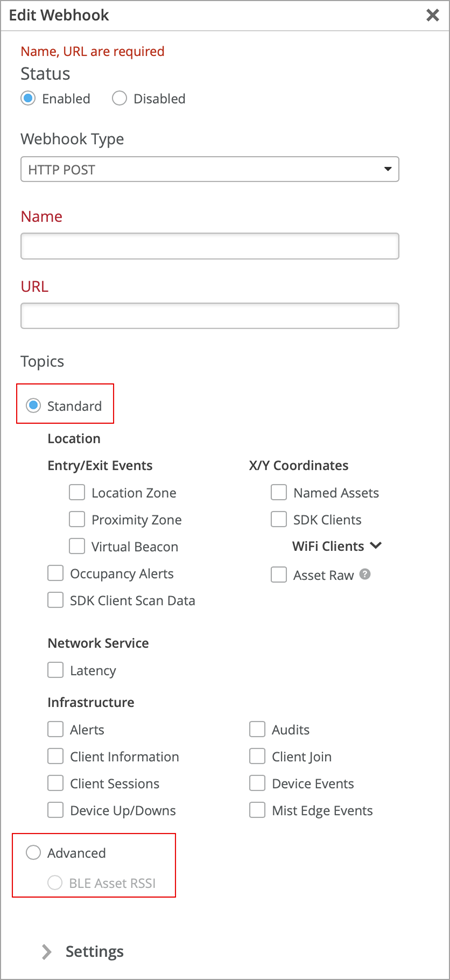
For improved user experience, we have rearranged the content on the site-level webhook configuration page (Organization > Site Configuration > Webhooks). We have grouped the webhook topics on the Add Webhook page into Standard and Advanced sections. The Standard section lists Location, Network Services, and Infrastructure topics. The Advanced section lists the BLE Asset RSSI topic, which will soon replace the Asset Raw topic. You can select only one section at a time. You can use the BLE Asset RSSI topic if you want to include only the BLE devices in the webhook, unlike the Asset Raw topic which would include both Wi-Fi and BLE devices.
In addition, we have categorized the location webhook topics into multiple subsections (see the image below).
Marvis
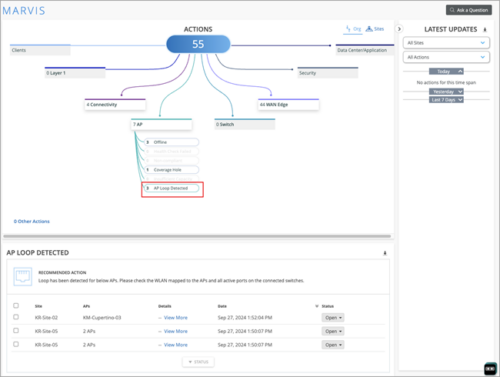
New Marvis Action: AP Loop Detected
We have added a new Marvis Action named ‘AP Loop Detected’ to the AP actions category. This action lets you view any AP Loop issues and the recommendations to resolve them. In addition, the details view shows reason for the loop. An AP loop can be caused by issues such as duplicate WLAN forwarding for the same VLAN.
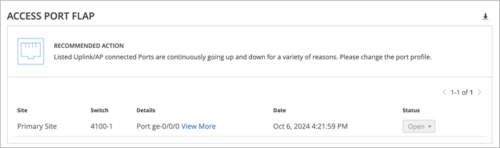
New Marvis Action: Access Port Flap
We have added a new Marvis Action, Access Port Flap, which displays the details about port flaps detected on wired access ports. This action is listed in the Other Actions section. You can also see the recommended actions to resolve the issue. In addition, you can download this information in a .csv format.
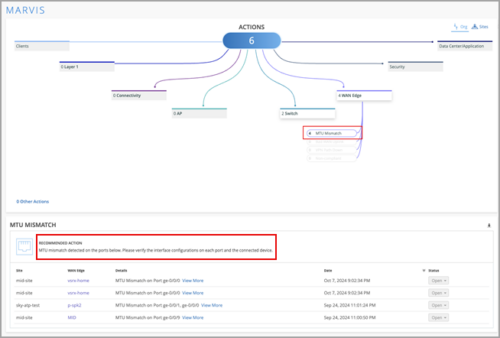
Update to Marvis actions under switch and WAN Edge
On the Marvis Actions page, we have made some updates to the actions listed under the Switch and WAN Edge categories. Under the Switch category, we have replaced the action Negotiation Mismatch with the following two actions: MTU Mismatch and Negotiation Incomplete.
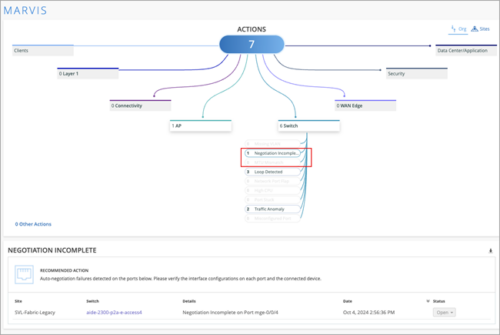
Under the WAN Edge category, we have updated the recommendation message for the MTU Mismatch action. The recommendation now lists the MTU errors instead of the earlier listed negotiation errors.
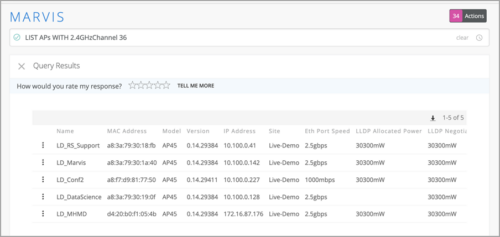
Marvis query language updates
We have expanded the access point (AP)-specific queries in Marvis Query Language (MQL) by adding more AP-specific query elements to it. This enhancement enables you to LIST, COUNT, and RANK APs based on the following newly added parameters: Eth Port Speed, LLDP Allocated Power, LLDP Negotiated Power, External IP Address, 2.4GHz TxPower, 2.4GHz Channel, 5GHz TxPower, 5GHz Channel, 6GHz TxPower, and 6GHz Channel. The following image shows a sample query using the query element 2.4 GHz Channel:
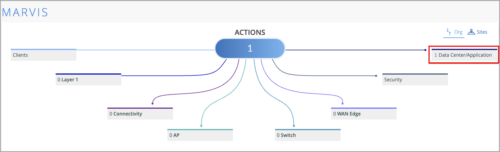
Apstra Cloud Services is now available to all users with access to Marvis Actions
Right to access Marvis for Datacenter in the Apstra Cloud Services application from the Mist Marvis view is now available to every user role within Mist – for the observer access granted on Apstra Cloud Services. To launch Apstra Cloud Services app from Mist, click the ‘Datacenter/Application’ category on the Mist Marvis Actions page. Note that you must link the organization in Juniper Mist with the organization in Juniper Apstra Cloud Services to be able to launch Apstra Cloud Services.
Access Assurance
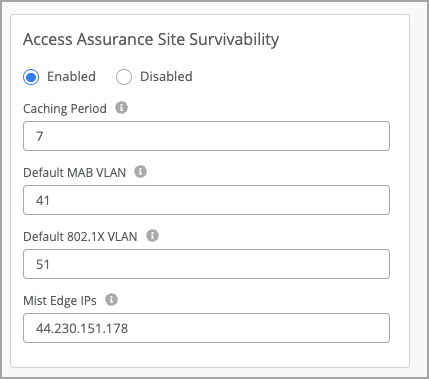
Access Assurance Site Survivability
You can now configure Access Assurance Site Survivability to ensure that Access Assurance services are available even when the cloud connectivity in the site is down.
Site survivability keeps the Access Assurance services up even when the cloud connectivity is down, by maintaining a cache of clients that were successfully authenticated over a specified number of days in the past. In this setup, Access Assurance services run on a Mist Edge device inside the customer site. The Mist Edge acts as a backup when the WAN links are down. You can configure the Access Assurance Site Survivability from the site configuration page (Organization > Site Configuration).
Manage Access Assurance Endpoints
We have created a NAC Endpoints page under Access Assurance to help you manage client endpoints at scale. This page, located at Organization > Access > Endpoints, serves as a database of endpoint devices.
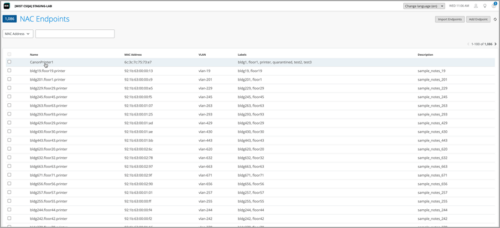
On the NAC Endpoints page, you can configure individual MAC addresses on the endpoints and assign them with various attributes, such as name, labels, VLANs, and roles. You can either import the endpoints in a .csv file or via API, or add individual records manually.
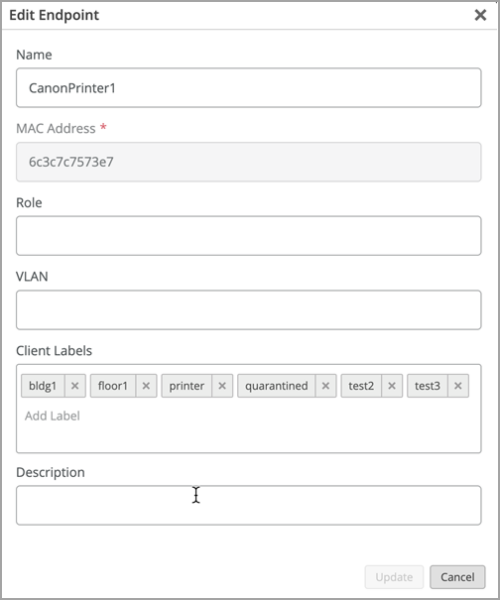
The labels used can be leveraged in Auth policies as match criteria. For example, you can assign any clients labeled as printers into an IoT network.

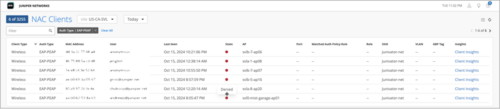
Visibility into Access Assurance clients
Mist provides visibility into the client devices authenticated to your network through Access Assurance. The NAC Clients page includes information about the present and past connections with filtering capabilities that allow you to search for any user or MAC address in the entire organization or in a given site. You can find the clients data on the Access Assurance Clients page (Clients > NAC Clients).
Wireless Assurance
Auto-provisioning enhancements
We have made the following enhancements to the auto-provisioning rules on the Organization > Settings page:
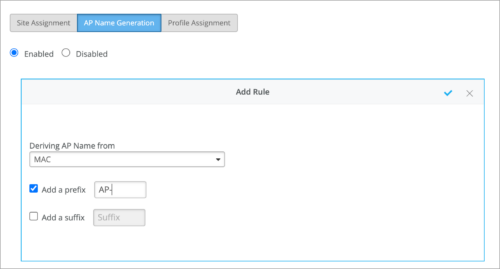
- Option to add multiple rules under each auto-provisioning type (Site Assignment, AP Name Generation, and Profile Assignment). You can use the Add Rule button to create multiple rules.

- Option to include device model as a filter in the Site Assignment rules for access points (AP).
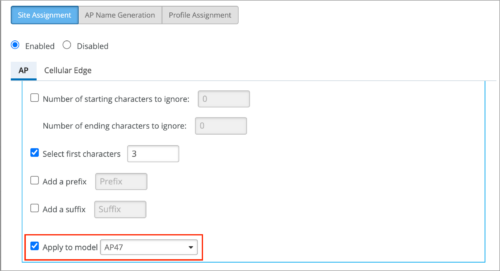
- Option to generate AP name from the device MAC address. Previously, you could generate AP name only from the LLDP port description.
Updates to RF channel and power configuration
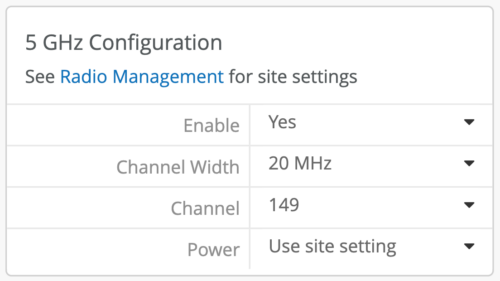
We have made a small, but useful update to the AP level static channel and transmit power configuration. If there are times when you need or wish to statically set the AP’s channel, previously that would put the AP’s transmit power to maximum if you left the power setting as “Use site setting”. Now the power level will be controlled via RRM and whatever you have set in the RF template or device profile when you set a static channel and leave the power setting as “Use site setting” or “Use profile setting.”
Wired Assurance
Support for vJunos-switch
You can onboard and manage a vJunos-switch on the Mist cloud. The vJunos-switch is a virtual version of a Juniper switch that runs the Junos OS. You can install a vJunos-switch as a virtual machine (VM) on an x86 server. You can configure and manage the vJunos-switch in the same way as you manage a physical switch. The vJunos-switch is built using EX9214 as a reference Juniper switch and supports a single Routing Engine and single Flexible PIC Concentrator (FPC).
Note: The vJunos-switch is a single virtual machine (VM) that you can use only in labs and not in the production environment.

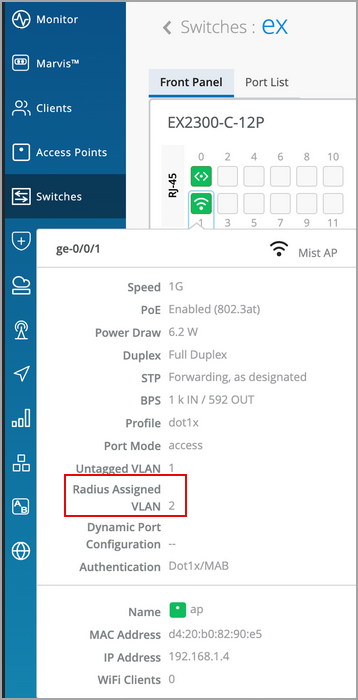
View RADIUS Assigned VLAN on dot1x ports
A switch port with dot1x-enabled is assigned a new VLAN by RADIUS post authentication. You can view this VLAN, called RADIUS-assigned VLAN, by hovering over the port in the Front Panel section on the switch details page.
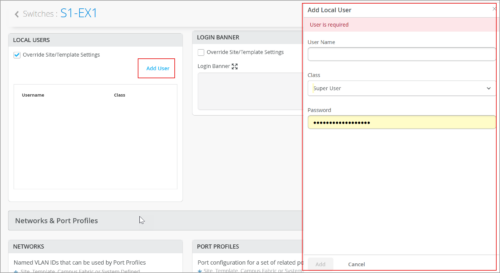
Create user accounts
Mist allows you to create user accounts locally on a switch for device management purposes. All users must have a predefined user account to be able to log in to the switch. For each user account, you need to define a username, login class (Operator, Read-only, Super User, or Unauthorized), and a password. You can create user accounts at the template level, site level, and switch level. You need a Super User role to create user accounts.
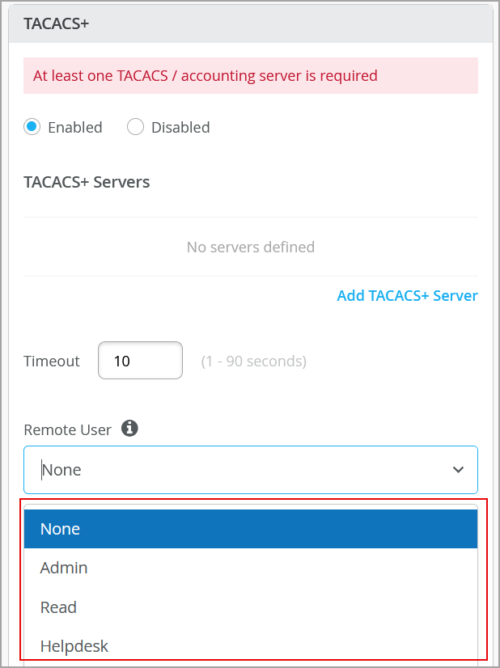
User roles for TACACS+ authenticated users
You can now specify a user role for TACACS+ authenticated users within switch configuration.
The following user roles are available: None, Admin, Read, Helpdesk. When the TACACs+ authenticated users do not have a user account configured on the local device, Junos assigns them a user account named ‘remote’ by default.
Export wired clients
The list of wired clients (Clients > Wired Clients) now has an option to export the list of clients into a .csv file.

New TX/RX charts for switches
We have added the following new charts to the switch insights:
- TX/RX Packets: Provides the number of TX and RX packets in the multicast, broadcast, and unicast categories.

- Data Rate: Provides the data speed at which the TX and RX packets were consumed.

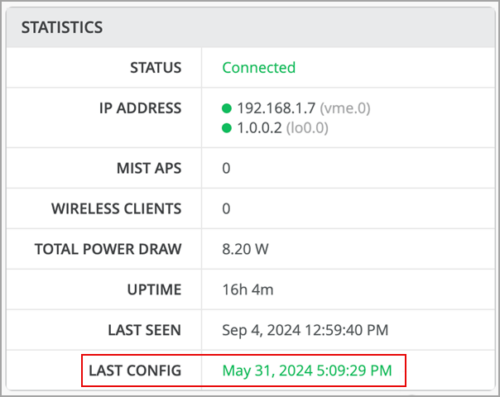
Switch configuration status update
We have improved the switch configuration status display logic to make the status more real-time. As per the new logic, the Last Config field on the Statistics tile on the switch details page shows the configuration change timestamp immediately after a user makes a configuration change to the switch. Previously, the Last Config data was updated based on the switch events, which take a bit longer to get updated. Also, the Last Config field shows the switch status to be in Monitoring mode when the switch is not managed by Mist. You can see the Last Config data on the switch details page and the switch list page.
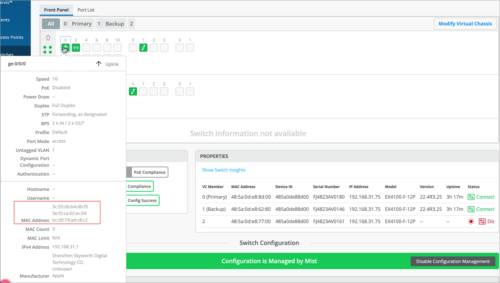
Switch ports display all the associated clients
Switch ports on the device details page now display the MAC addresses of all the associated clients that are not managed by Mist. For example, if the switch is connected to a hub switch which is housing multiple wired clients that are not managed by Mist, the switch port displays the MAC addresses of all the wired clients it learned.
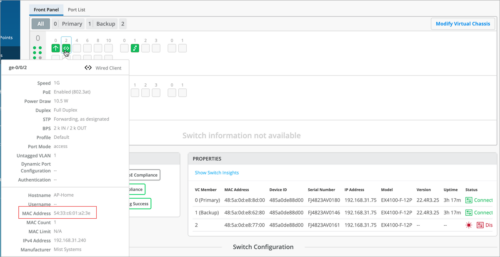
However, if the switch port is connected to Mist-managed clients (for example, another switch and a Mist AP), the switch port shows the MAC address of one client only- either the AP or the switch.
WAN Assurance
Enhancements to Secure Edge Connector
We have added the following enhancements to Secure Edge Connector:
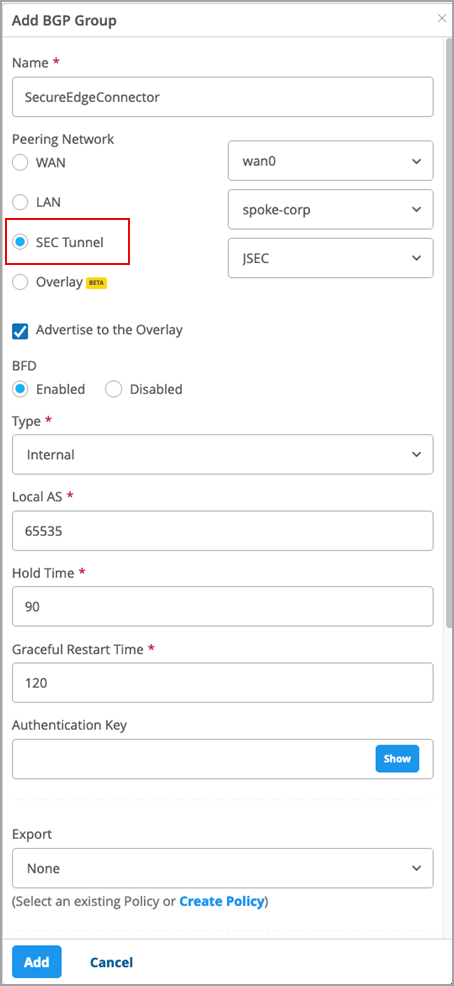
- BGP support: On the BGP Group configuration page for WAN Edges, you can select the Secure Edge Connector (SEC) tunnel as the peering network.
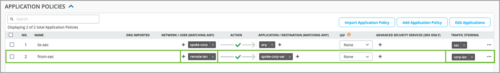
- Inbound Application Policy Support: You can include a remote network in a Secure Edge Connector and then use that network in an application policy to allow inbound access from the Secure Edge Connector. With this feature, you can securely connect to cloud-hosted services which need to initiate inbound traffic to a site. To include a network in the Secure Edge Connector, go to the Add Provider screen from the WAN Edge details page, select the provider type as Custom, select a network (or create one) in the Remote Networks field, and save the configuration.

You can then use this Network in an application policy to allow access from the Secure Edge Connector, as shown below:
Onboarding over LACP interfaces
For WAN Edge, Mist can automatically perform onboarding through an aggregated interface on the connected chassis cluster, but the interface must first be enabled, or the connection will fail.
In the Organization > WAN Edge Template configuration in Mist, when adding either a LAN or WAN interface, select the Enable Force Up option if the peer interface is using Link Aggregation Control Protocol (LACP). Doing so will force the first Ethernet interface in the cluster on the peer to the UP state, thus allowing the zero-touch provisioning (ZTP) process to retrieve the configuration files needed to complete onboarding. This feature is already available for SRX Series devices.
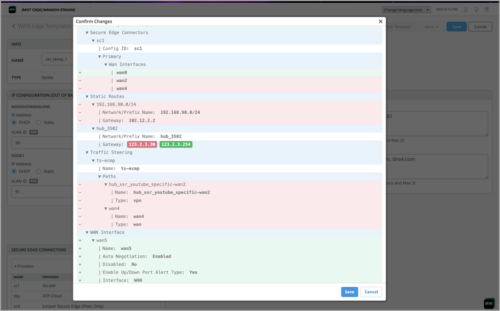
Configuration differences view for WAN Edge templates
When you modify a WAN Edge template and click Save, a confirmation window shows the difference between the new (modified) and the old configuration. This window provides a quick view of all the configuration changes you made before you submit them. On this view, the configurations added appear with a plus sign (+), while the configurations removed appear with a minus sign (–).
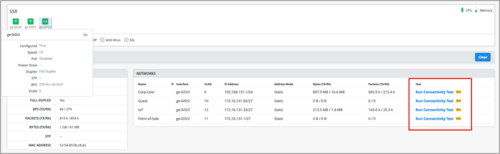
Application reachability verification tool
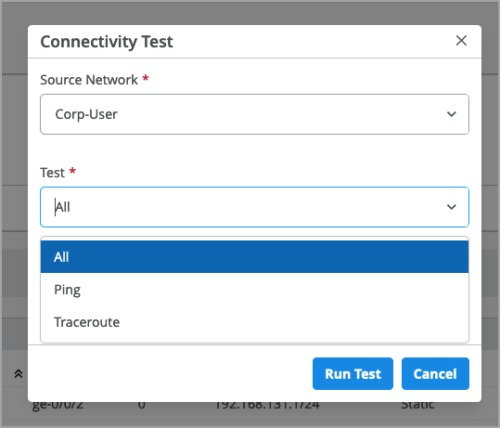
As a Mist WAN user, you can ping a destination address within an application sourced from a configured network that you have allowed in an application policy. This feature enables you to independently verify that end-to-end routing to the application is working. This feature is helpful when you debug application reachability in the context of an application policy you created. To run this test, select a LAN port from the device details page and then click Run Connectivity Test from the Networks section.
Secure AI native edge features
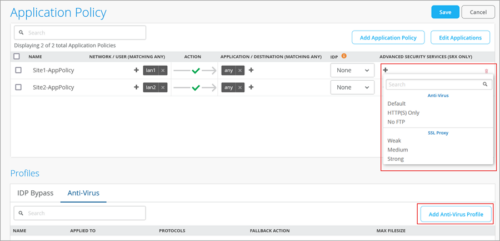
You can configure the following secure AI native edge features in an application policy under Advanced Security Services for SRX Series firewalls:
- Secure Sockets Layer (SSL) Forward Proxy: SSL forward proxy acts as an intermediary, performing SSL encryption and decryption between the client and the server. SSL forward proxy is a transparent proxy; that is, it performs SSL encryption and decryption between the client and the server, but neither the server nor the client can detect its presence. The following SSL Proxy profiles are available based on the cipher category: Weak, Medium, and Strong.
- Anti-virus: You can create an anti-virus configuration and associate it with an application policy. You can either select from a set of predefined configurations (Default, HTTP(S) Only, and No FTP), or create a custom anti-virus configuration.
Note: These features require additional device side licenses.
Routing Assurance
Juniper Mist Routing Assurance integration
You can integrate your Juniper Mist Routing Assurance account with your Mist organization.
Juniper Mist Routing Assurance is an AIOps-based routing observability platform that provides actionable insights to network administrators, which enable them to respond proactively to anomalies in the enterprise routing infrastructure.
To integrate Routing Assurance with Mist, go to the Routing Assurance Integration tile on the Organization > Settings page of the Mist portal and provide information such as the Routing Assurance Organization ID and the API token details. A Mist organization can only map to one Routing Assurance organization.
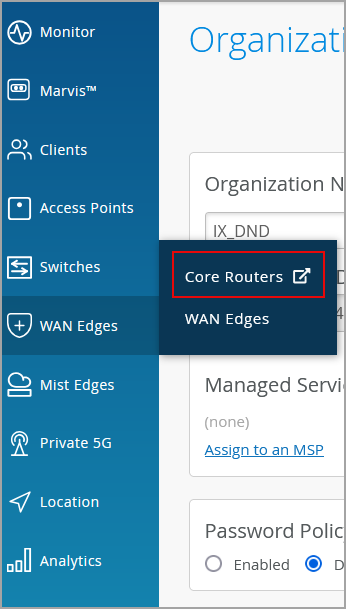
When integrated with Mist, the Routing Assurance services will be accessible from the WAN Edge menu on the Mist portal. A menu option, named Core Routers, will appear on the WAN Edges menu. Clicking the Core Routers option, which is visible only to organization-level admins, opens the Routing Assurance portal in a new tab.
Mist Edge
Upstream resource monitoring enhancements
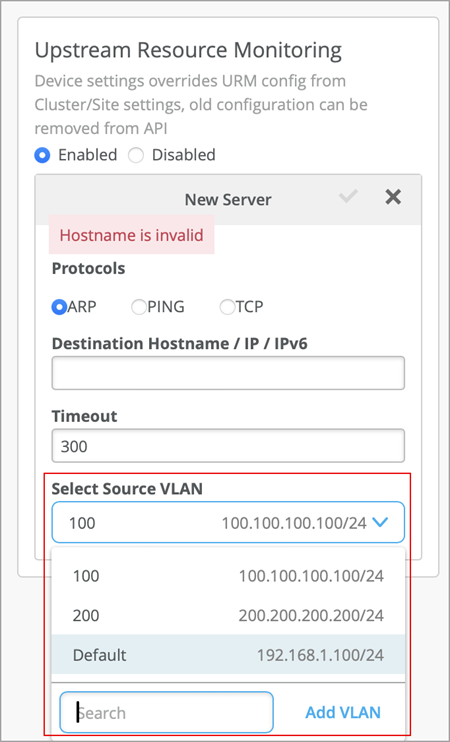
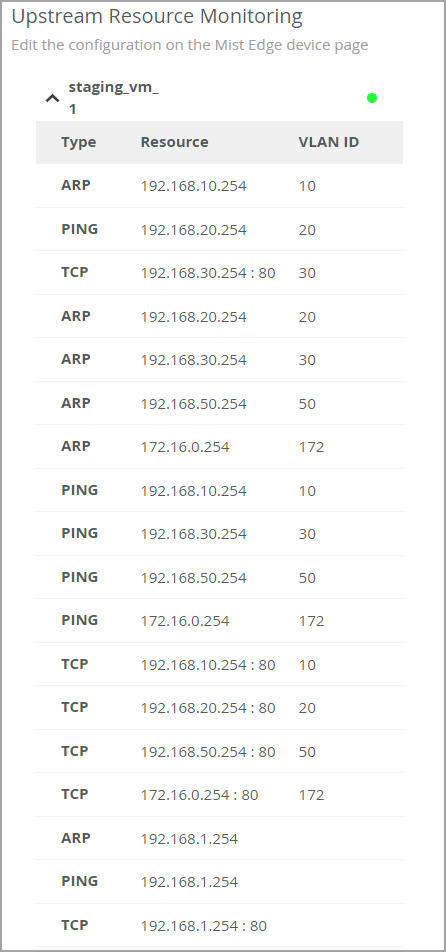
We have moved the upstream resource monitoring configuration to the Mist Edge device level from the Mist Edge Cluster and site levels. The configuration now includes an option to specify a VLAN interface to source ARP, ICMP, TCP packets.
You must specify a VLAN interface if the upstream resources are not directly reachable via the tunnel interface and the route specified. You need not specify a VLAN interface if the upstream resources are directly reachable. When you do not specify a VLAN, Upstream Resource Monitoring uses the default VLAN which is the tunnel interface. You can configure Upstream Resource Monitoring from the Mist Edge configuration page.
As part of this enhancement, we have also added a table (to the Mist Edge configuration page) for all the VLAN interfaces configured by users for DHCP relay or upstream resource management.
In addition, the Upstream Resource Monitoring tile displays a resource status that shows whether the resources are reachable (indicated in green) or not reachable (indicated in red).
Support and Privacy
Additional email recipients in support tickets
You can now include additional email addresses to be copied on any support ticket update. You can add multiple email addresses in a comma separated format to the ‘CC (optional)’ field. This field is available for the following ticket types: Subscriptions, Configuration Help, Problem, and Questions. Emails can be added during initial case creation, or added later after the case is created.
Adding email IDs to new tickets:
Adding email IDs to existing tickets:
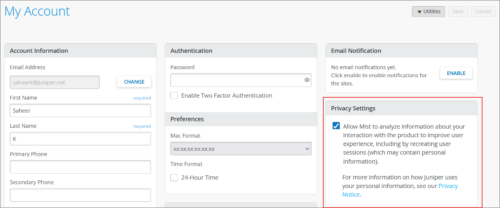
Mist privacy settings update
You can now choose to provide user-level consent to Mist to analyze the pattern of your interaction with the Mist portal with a view to improving user experience. Previously, this consent was provided at the organization level. With this change, the organization landing page displays a request for your consent each time you log in, until you accept or decline it. You can also see this request on the account registration page and on the My Accounts page (see below).
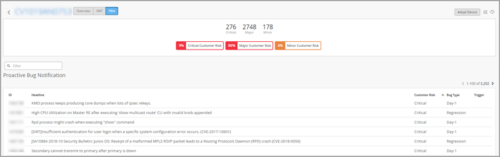
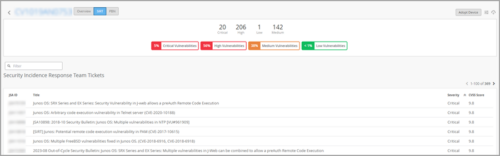
View SIRT and PBN Reports
Security Incident Response Team (SIRT) advisories (security vulnerabilities) and Proactive Bug Notifications (PBNs) for Juniper Networks devices are now available through the device details page, accessed from the Installed Base view of the Inventory (Organization > Admin > Inventory > Installed Base). To populate the Installed Base view with the device list, you must have integrated your Juniper Networks account with your Mist organization via the Account Integration tile on the Organization > Admin > Settings page.
For connected (Assured or Onboarded) devices, the advisories and notifications are specific to the type of Juniper Networks device filtered by the Junos OS version installed. For devices that are not connected, the advisories and notifications are specific to the type of Juniper Networks device only.
Sample SIRT Report:
Sample PBN Report: