Technology Primer: Micro and Macro Segmentation using Group Based Policy through Mist Wired Assurance
You can achieve micro and macro segmentation, for example to secure data and assets, in a VXLAN (Virtual extensible Local Area Network) architecture using Group Based Policy (GBP). GBP leverages underlying VXLAN technology to provide location-agnostic endpoint access control. GBP allows you to implement consistent security policies across the enterprise network domains. You can simplify your network configuration by using GBP, avoiding the need to configure large numbers of firewall filters on all your switches. GBP blocks lateral threats by ensuring consistent application of security group policies throughout the network, regardless of the location of endpoints or users. VXLAN-GBP works by leveraging reserved fields in the VXLAN header for use as a Scalable Group Tag (SGT). You can use the SGTs (Scalable Group Tag) to match conditions in firewall filter rules. Using an SGT is more robust than using port or MAC (Media Access Control) addresses to achieve comparable results. SGTs can be assigned statically (by configuring the switch on a per port or per MAC basis), or they can be configured on the RADIUS (Remote Authentication Dial in User Service) server and pushed to the switch through 802.1X when the user is authenticated.
The segmentation enabled by VXLAN-GBP is especially useful in campus VXLAN environments because it gives you a practical way to create network access policies that are independent of the underlying network topology. It simplifies the design and implementation phases of developing network-application and endpoint-device security policies.
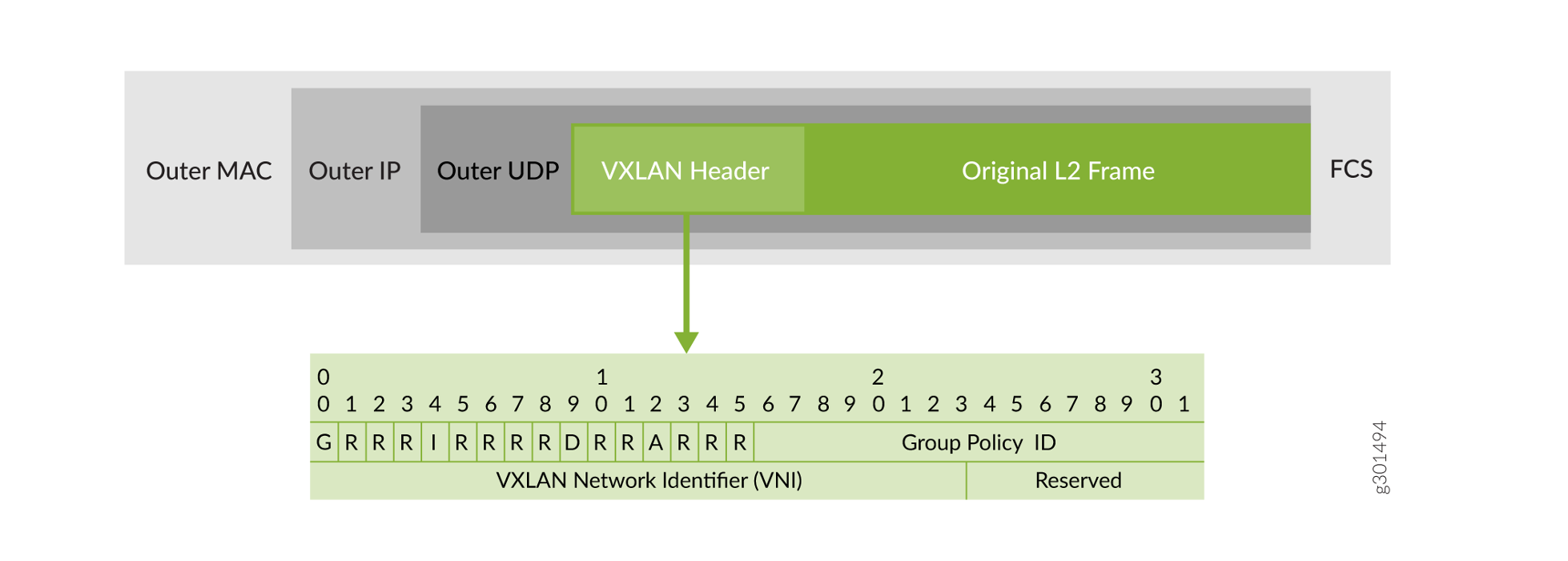
You can find more detailed information on the VXLAN-GBP standard in the IEEE RFC, I-D.draft-smith-vxlan-group-policy. For the purposes of this example, suffice to say, VXLAN-GBP leverages reserved fields in the VXLAN header as Scalable Group Tag, as shown in the illustration.
Figure 1: VXLAN Header Fields
This topic discusses advanced GBP (supported in Junos Release 22.4R1 and later). Basic GBP (supported in Junos OS release 21.1R1 and later) configuration through cli commands imported into Mist Wired Assurance can be found here: https://www.juniper.net/documentation/us/en/software/junos/evpn-vxlan/topics/example/micro-segmentation-using-group-based-policy.html#concept_hjw_bhb_mvb
The table below provides the details of the switches that support VXLAN-GBP based on the Junos releases from when the support is provided.
Table 1: VXLAN-GBP Supported Switches
|
Junos Release |
VXLAN-GBP Supported Switches |
|---|---|
|
Starting with Junos OS Release 21.1R1 |
Basic VXLAN-GBP: EX4400-24P, EX4400-24T, EX4400-48F, EX4400-48P, and EX4400-48T |
|
Starting with Junos OS Release 21.4R1 |
Basic VXLAN-GBP: • QFX5120-32C, QFX5120-48T, QFX5120-48Y, and QFX5120-48YM
• EX4650 and EX4650-48Y-VC
|
|
Starting with Junos OS Release 22.4R1 |
Advanced VXLAN-GBP: • EX4100 Series
• EX4400 Series
• EX4650 Series
• QFX5120-32C and QFX5120-48Y
|
NOTE: We recommend using advanced GBP (available in releases 22.4R1 and later) even though basic GBP is supported. You can port any CLI statements configured with basic GBP into an advanced GBP configuration using Mist Wired Assurance cli commands.
Table 2 shows the differences in the two implementations.
Advanced GBP (Junos OS Release 22.4R1 and later)
Starting with Junos OS Release 22.4R1, the GBP feature has some enhancements. With Advanced GBP, you can do policy enforcement on the ingress endpoint and perform GBP-tagging on these enhanced match conditions.
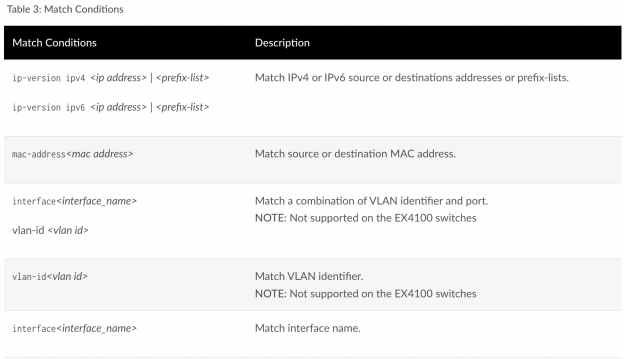
Table 3 shows the supported GBP-tagging match conditions.
Assigning GBP/SGTs
In this example we configure SGTs through Mist Wired Assurance using various classification mechanisms such as MAC, VLAN (Virtual LAN), and IP based classifiers. Per the earlier comments, VXLAN-GBP leverages reserved fields in the VXLAN header as Scalable Group Tags. Therefore, SGT and GBP are analogous terms.
SGTs can also be configured on a RADIUS server, and then use 802.1X access control on the EX4400 to receive them. RADIUS servers are commonly used in campus environments for access control and, for example, to govern the assignment of VLANs. RADIUS servers are commonly used in campus environments for access control and, for example, to govern the assignment of VLANs.
You can find additional information on how to integrate GBP tagging with a Radius Server at the following link: https://www.juniper.net/documentation/us/en/software/junos/evpn-vxlan/topics/example/micro-segmentation-using-group-based-policy.html#concept_vzp_rhb_mvb
GBP-based filters are used as classifiers for GBP tagging. These filters classify incoming streams and assign a GBP tag.
You can see how this works in the following Mist Wired Assurance Switch Policy Labels and Switch Policy configurations. GBP firewall policies are framed based on source and destination GBP tags. A source tag is the 16-bit field in the VXLAN header in the incoming packet and is derived from the address (IP/MAC/port and so on) lookup, while the destination tag is derived at the egress tunnel or ingress endpoint, according to the configured tag assignment.
Figure 2: Mist Wired Assurance GBP Tag Management and Switch Policy enforcement:
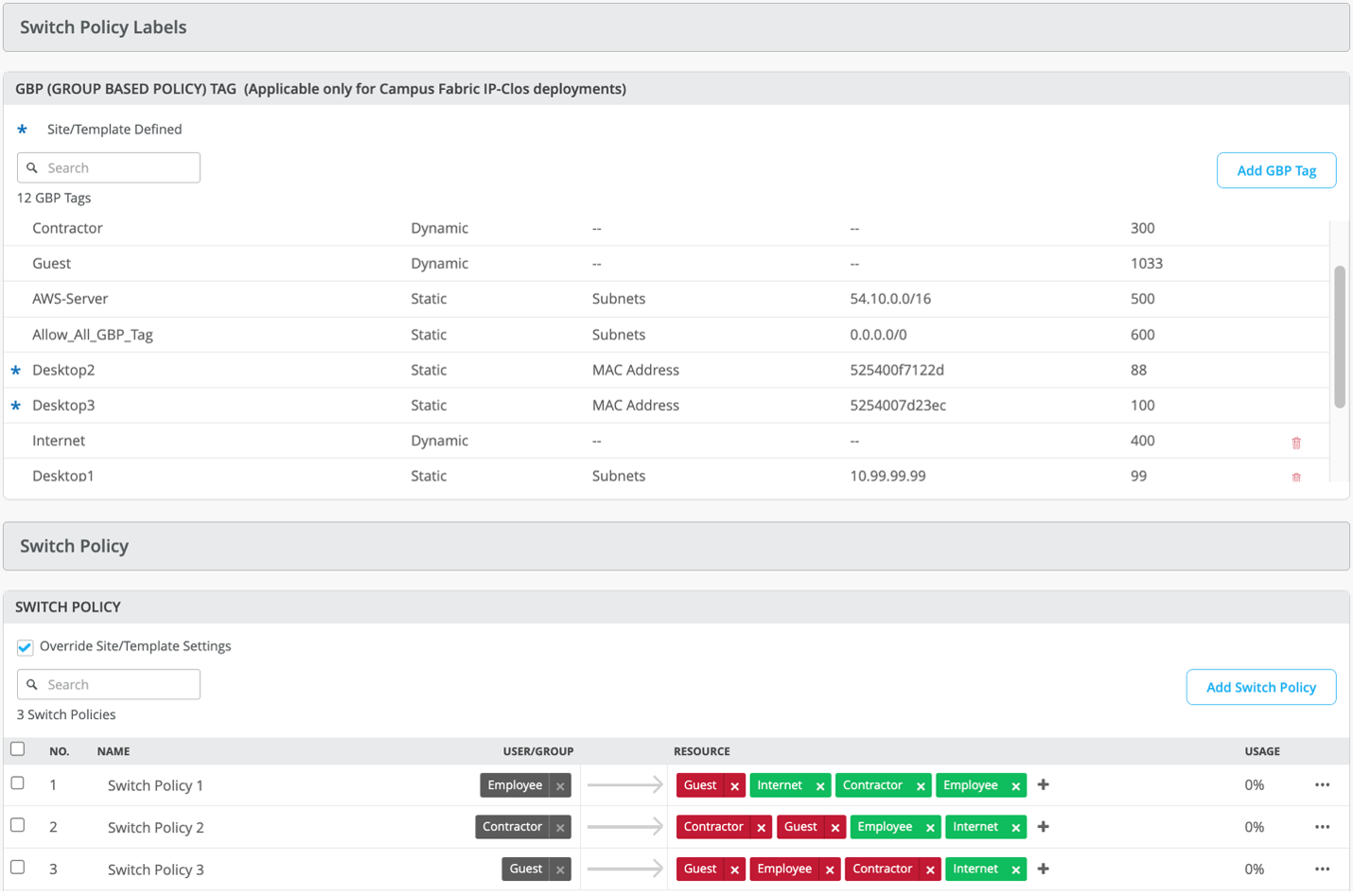
The same tag assignment used to map the source MAC address to the source tag is also used to map the destination MAC address to the destination tag. This is true for port-based assignments as well.

Note that by default policy enforcement is done on the egress endpoint. If you want to do policy enforcement on the ingress leaf, see the section below. In addition, you must enable VXLAN-GBP globally on the ingress node, so it can perform the look-up on the matches and add SGT in the VXLAN header, and on the egress node.
Policy Enforcement Overview on the Ingress Endpoint
Starting with Junos Release 22.4R1, you can also perform the policy enforcement on the ingress endpoint. Ingress enforcement optimizes the network bandwidth. To support policy enforcing on the ingress, we have a mechanism to propagate the MAC and IP-MAC based tags across the network using Type 2 and Type 5 routes. See EVPN Type 2 and Type 5 routes for more information. With this, the destination GBP-based policy is enforced in nodes closer to the ingress for MAC and IP-based GBP matches. Tag propagation is always in context of MAC and IP-based GBP. For VLANs, Port, and Port+VLAN matches this is not applicable.
You must enable the following statement to perform the policy enforcement at the ingress node. When ingress enforcement is enabled or disabled, the Packet Forwarding Engine (PFE) restarts.
|
set forwarding-options evpn-vxlan gbp ingress-enforcement |
Before creating any GBP Policies, it can be helpful to organize your scheme by creating a table for all your endpoints (users and devices) and the assigned SGT value. The table below can be used to further simplify the logic and clarify your rules.
|
Endpoint |
Assigned SGT Values |
|---|---|
|
Employee |
200 |
|
Contractor |
300 |
|
Guest |
1033 |
|
Internet |
400 |
|
Desktop1 |
99 |
|
Desktop2 |
88 |
|
Desktop3 |
100 |
|
|
Employee |
Internet |
Contractor |
Guest |
Desktop1 |
Desktop2 |
Desktop3 |
|---|---|---|---|---|---|---|---|
|
Employee |
Y |
Y |
Y |
N |
|
|
|
|
Contractor |
Y |
Y |
N |
N |
|
|
|
|
Guest |
N |
Y |
N |
N |
|
|
|
|
Internet |
|
|
|
|
|
|
|
|
Desktop1 |
|
|
|
|
|
N |
Y |
|
Desktop2 |
|
|
|
|
N |
|
N |
|
Desktop3 |
|
|
|
|
Y |
N |
|
Topology
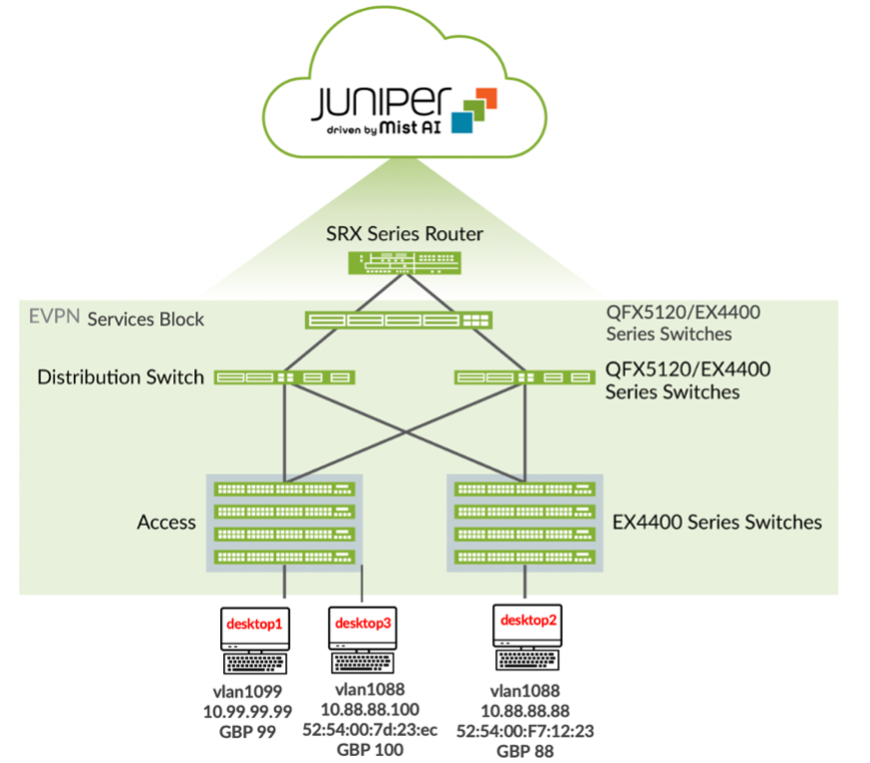
For the sake of simplicity, all the configuration in this example is done on both Juniper EX4400 series switches running Junos OS Release 22.4.1R1. The switch is connected to a RADIUS server for AAA (Authentication Authorization Accounting). Both switches function as ingress in this example. Recall that for SGTs you must define the firewall on the egress switch, whereas you would typically do it on the ingress VXLAN gateway for the access layer.
Figure 4: Campus Fabric IP Clos Architecture with GBP tagging on the EX4400 switches
Requirements
Enhanced GBP is supported in Junos OS 22.4R1 on the following switches: EX4100, EX4400, EX4650, QFX5120-32C, and QFX5120-48Y.
High Level Mist Wired Assurance GBP Overview
GBP Scenarios configured through Mist Wired Assurance
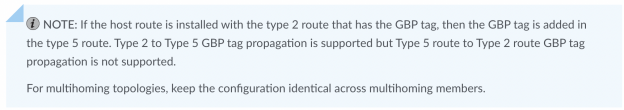
NOTE: Mist allows Users to have multiple classifiers associated with the same GBP tag. For example, Desktop 2 and Desktop 3 have MAC and IP addresses associated with GBP tags 88 and 100 respectively.
Name the Tag with a Distinct Name, in this case: Desktop2-IP. Then associate GBP=88 with the Static IP Address: 10.88.88.88 (assumes a /32 host entry)
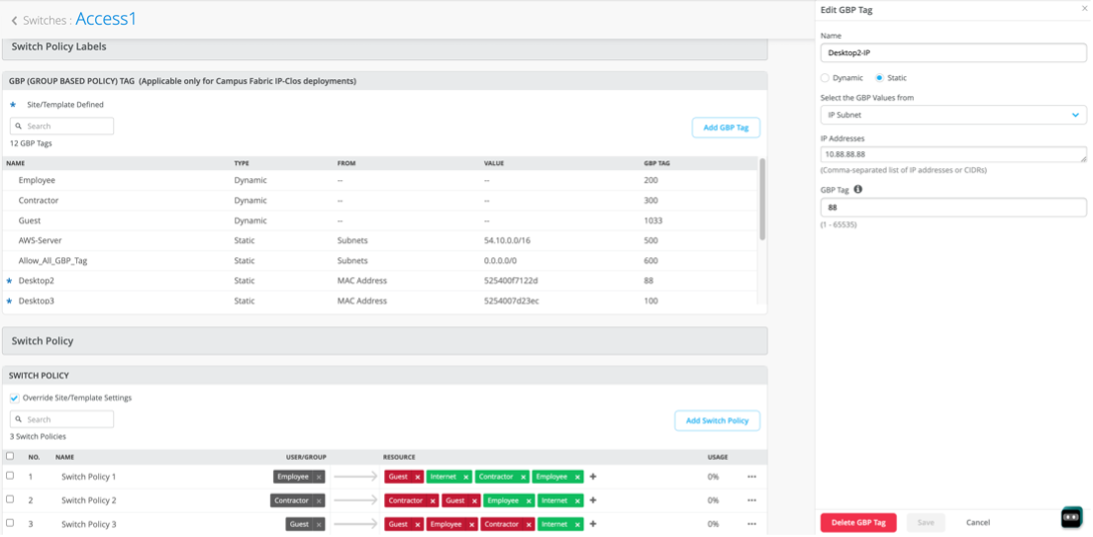
Name the Tag with a Distinct Name, in this case: Desktop3-IP. Then associate GBP=100 with the Static IP Address: 10.88.88.100 (assumes a /32 host entry)
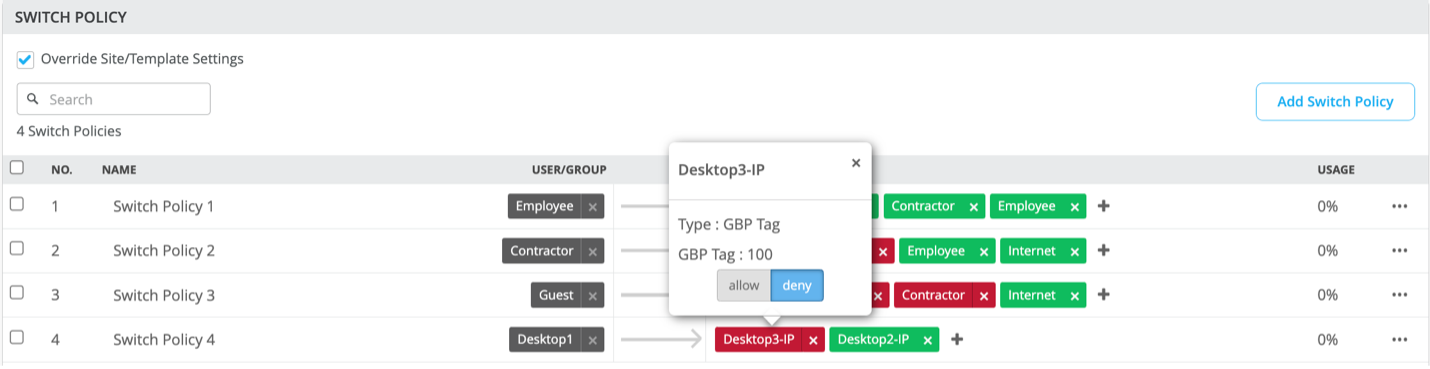
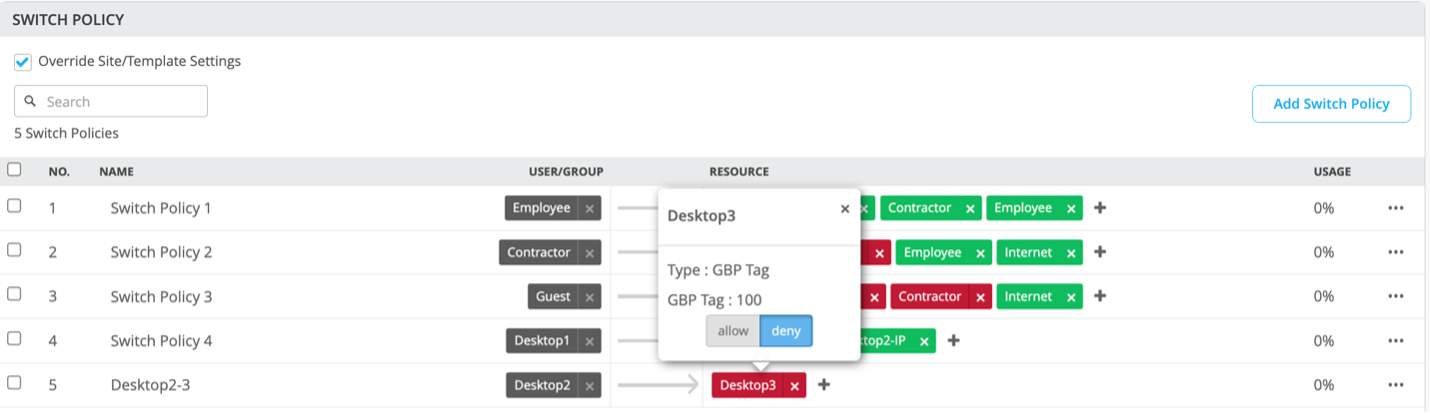
NOTE: The Desktop2-3 policy chose the MAC address classifiers emulating a Private VLAN use case. Here, the Campus Fabric enforces, at ingress, micro-segmentation at the VLAN level.
Appendix
Ingress Enforcement was chosen which requires additional cli commands to be invoked at the Switch Template:
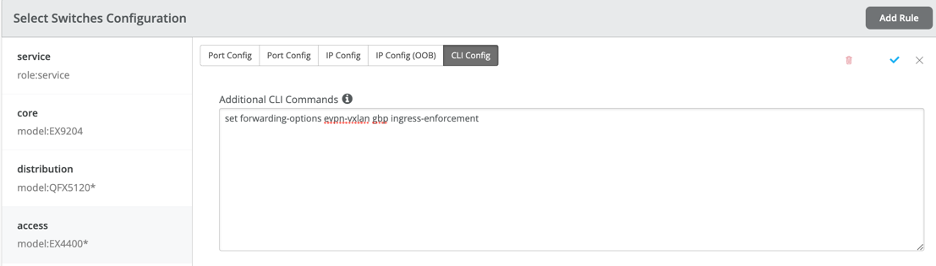
The following Firewall Filters and GBP Tagging classifiers are pushed to Access (for the sake of brevity, the new Desktop2 and Desktop3 filters are shown below):