Overview
Mist Access Assurance provides a capability to integrate with eduroam NROs (National Roaming Operators) using Mist Edge acting as a RADIUS proxy. Mist Edge would act as a gateway to eduroam RADIUS servers with a static public IP or NAT IP assigned such that it can be registered as a RADIUS client in the eduroam admin portal.
Mist Edge Proxy is used in particular with eduroam SP and IdP authentication flows, it does not affect home users authentication.
The following call flows outline three types of users in eduroam networks and how each type would authenticate via Mist Access Assurance and Mist Edge proxy: home users on campus, external visitors on campus (SP), and home roaming users (IdP).
Home users
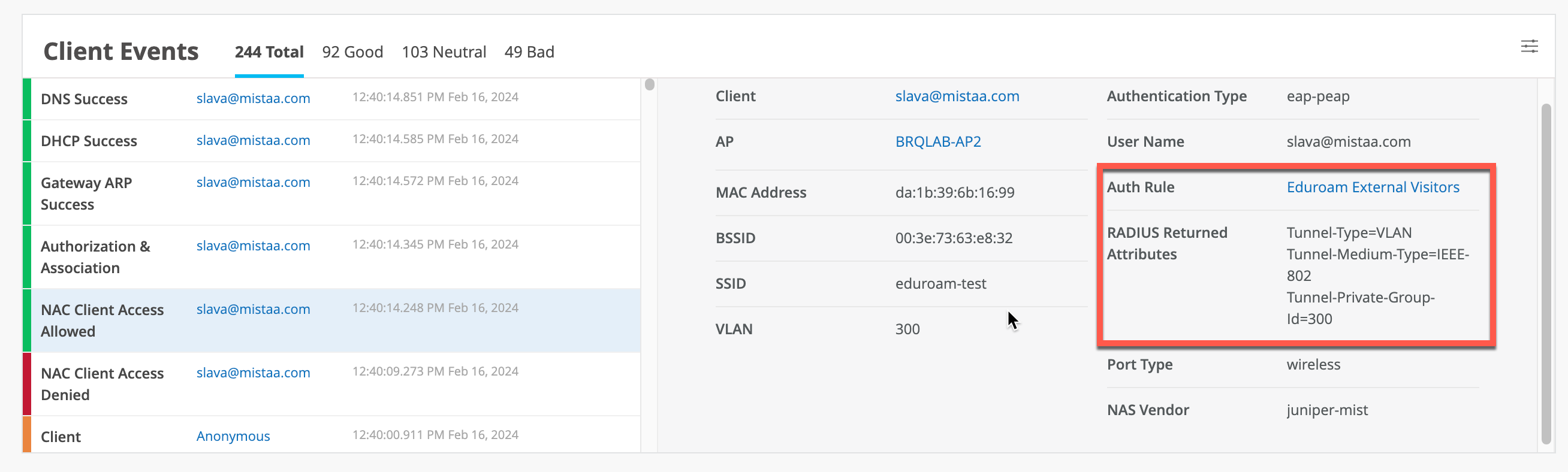
Home users are clients that are connecting to eduroam SSID on the university campus that belong to the university. Lets take an example of university1.edu, users that are part of the university are considered “home” users, identified by the “home” realm @university1.edu. This scenario does not require Mist Edge proxy and users authenticate directly with Mist Access Assurance.
Home users on campus would authenticate against Mist Access Assurance service, and in this scenario Mist Edge is not involved. This scenario typically constitutes the majority of all authentications happening daily:
External visitors
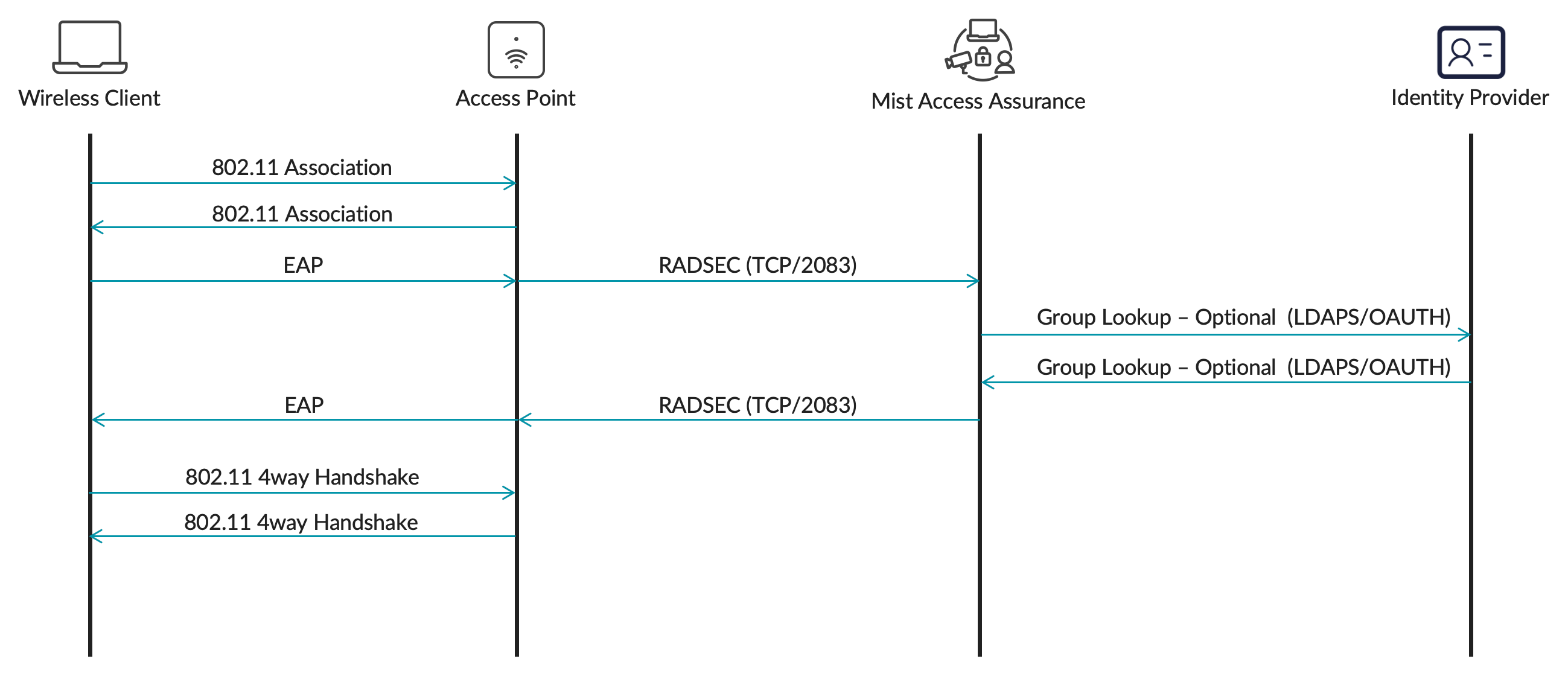
External visitors are users who are visiting university campus from another institution. Continuing with our example, if a user from university2.edu is visiting a campus of university1.edu, it is considered an external visitor, identified by a realm that is not same as “home” realm, in this case @university2.edu. This scenario requires Mist Edge Proxy IDP to forward authentication request to the external institution via eduroam RADIUS servers.
External visitors on campus (a.k.a eduroam SP flow) would authenticate via a Mist Edge proxy, where Mist Edge proxies authentication requests towards the eduroam national RADIUS servers:
Home roaming users
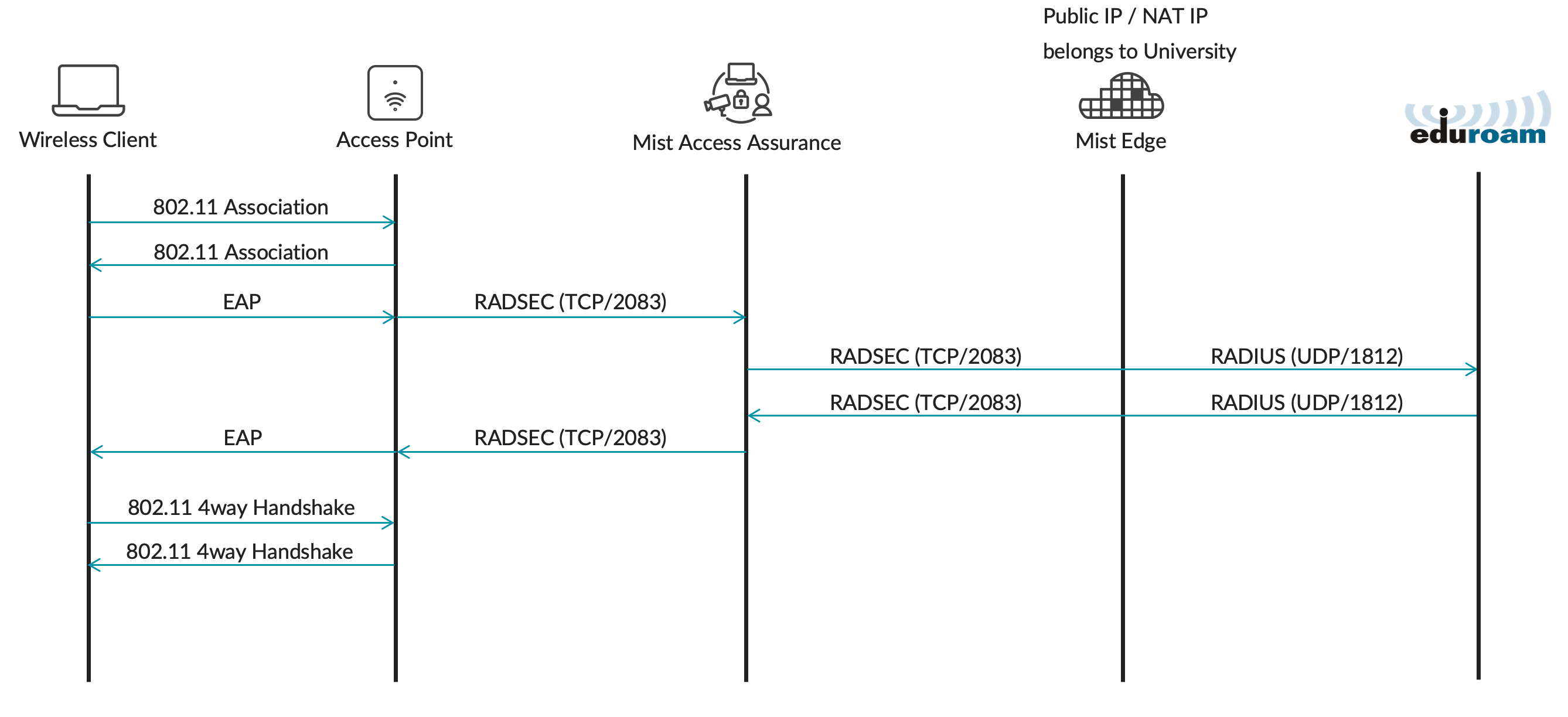
Home roaming users are those who are travelling to a different institution and would like to authenticate to eduroam SSID using home university credentials. If we follow our example above, users from university1.edu visiting to university2.edu would be considered home roaming users. In these scenarios authentication requests are coming from the external institution via eduroam RADIUS servers towards home institution Mist Edge proxy, which is then authenticated at the Mist Access Assurance.
In case of home roaming users (a.k.a. eduroam IdP flow) RADIUS Access-Requests from eduroam national RADIUS servers would be received by the Mist Edge Proxy and then forwarded to the Mist Access Assurance service for authentication.
Firewall requirements:
Mist Edge uses Out Of Band Management interface (OOBM) for all its proxy functionalities. It is possible to either assign a public IP address to the OOBM interface, or place it behind NAT firewall.
The following ports and destinations must be allowed:
Inbound (towards Mist Edge OOBM interface):
RADIUS Auth & Acct (1812 / 1813 UDP) – you could limit source IPs to eduroam national RADIUS servers
RadSec (2083 TCP) – you could limit source IPs based on the following document.
Outbound (from Mist Edge OOBM interface):
RADIUS Auth & Acct (1812 / 1813 UDP)
RadSec (2083 TCP) towards radsec.nac.mist.com
HTTPS (443 TCP) towards ep-terminator.<mist_cloud_env>.mist.com (more on correct endpoint for your cloud environment in this document).
Notes:
- Mist Access Assurance only supports EAP-TLS, TEAP or EAP-TTLS methods for home users and home roaming users.
- For external visitors any EAP method is supported, including PEAP-MSCHAPv2. EAP method support is determined by an external institution RADIUS servers.
- Dedicated Mist Edge(s) are recommended for the IDP Proxy functionality.
- For proxy service redundancy multiple Mist Edges can be used as part of the same Mist Edge cluster.
Configuration
Mist Dashboard
Step 1 – Claim or register a Mist Edge, and create Mist Edge cluster
Follow this document to register a new Mist Edge and create a Mist Edge cluster.
Step 2 – Create Mist Edge Proxy Identity Provider
Navigate to Organization > Access > Identity Providers, click Add IDP:
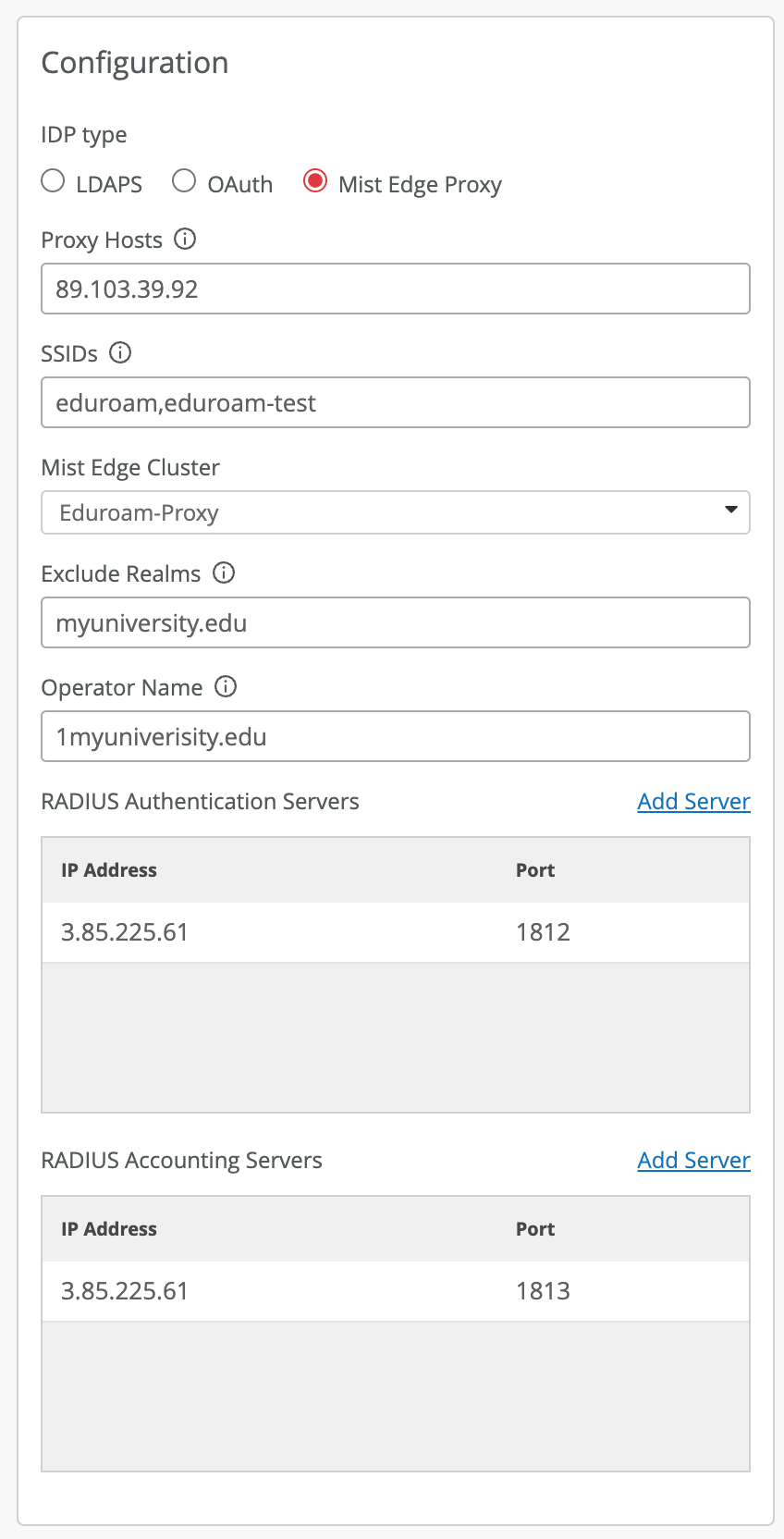
Proxy Hosts: these are the public IP or NAT IP addresses of your Mist Edge or multiple Mist Edges acting as eduroam proxies.
SSIDs: List of comma-separated SSIDs that would use this proxy IdP
Mist Edge Cluster: select a cluster from a dropdown menu which you created in Step 1. All Mist Edges public IP addresses listed in Proxy Hosts must be part of the same Mist Edge Cluster.
Exclude Realms: avoid proxying home users towards eduroam, in case no other IdP is configured for home users. This is required only in case EAP-TLS is used for home users without any external IDP added as authorization source. Optional setting.
Operator Name: add Operator-Name RADIUS attribute when proxying Access-Requests towards eduroam federation, required by some eduroam NROs. Note that Operator name must always start with 1. Usually it is in format 1 + <instituion fqdn>, for example 1university1.edu
RADIUS Authentication and Accounting servers: list of IP addresses / shared secrets of all national eduroam RADIUS servers.
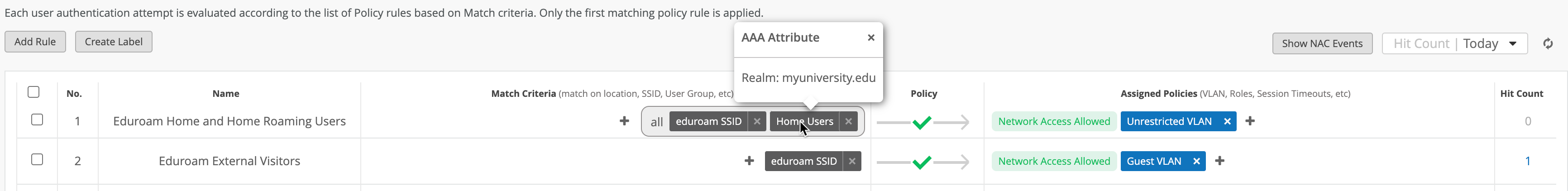
Step 3 – Configure Auth Policy Rules for eduroam SSID
The following outlines the most basic scenario of handling both home and external users on eduroam network, where external users are placed into a Guest VLAN, while home and home roaming users are placed into a primary university VLAN:
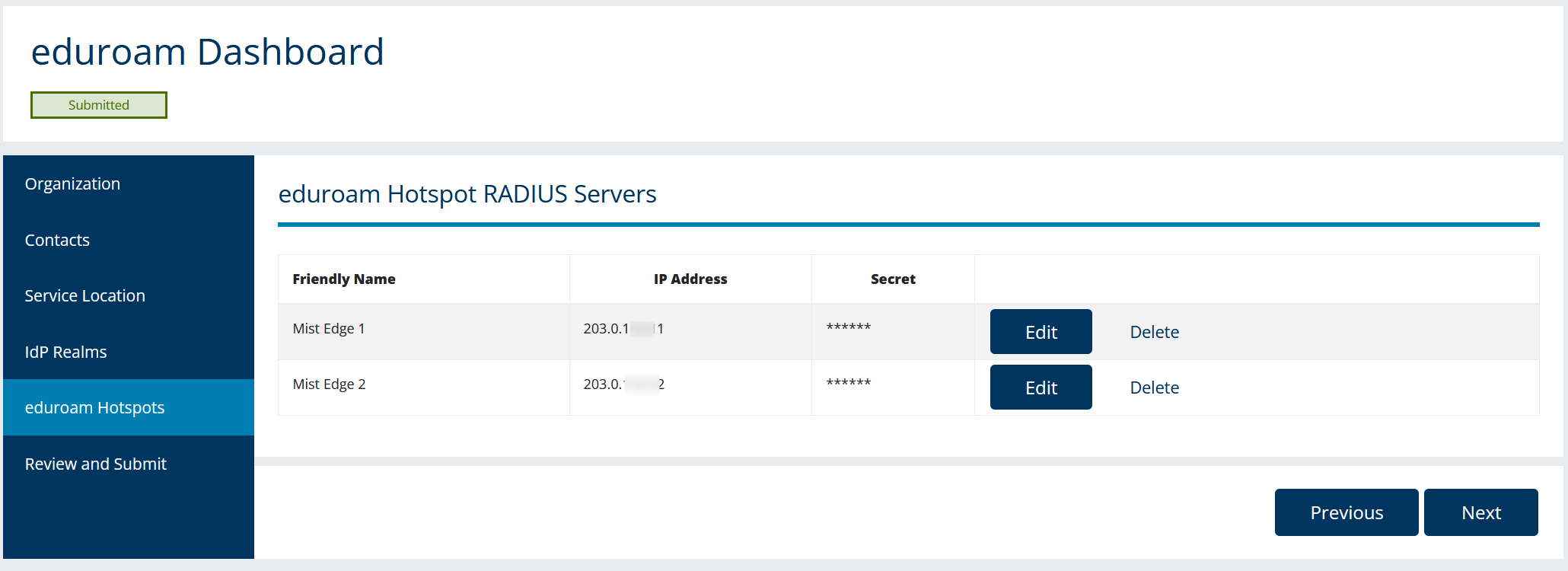
eduroam Admin Console
Do not forget to add Mist Edges to the eduroam admin console. Depending on the eduroam NRO the admin console might look different, but overall integration points will remain the same.
The following is an example of Internet2 eduroam admin console.
SP configuration (External Visitors):
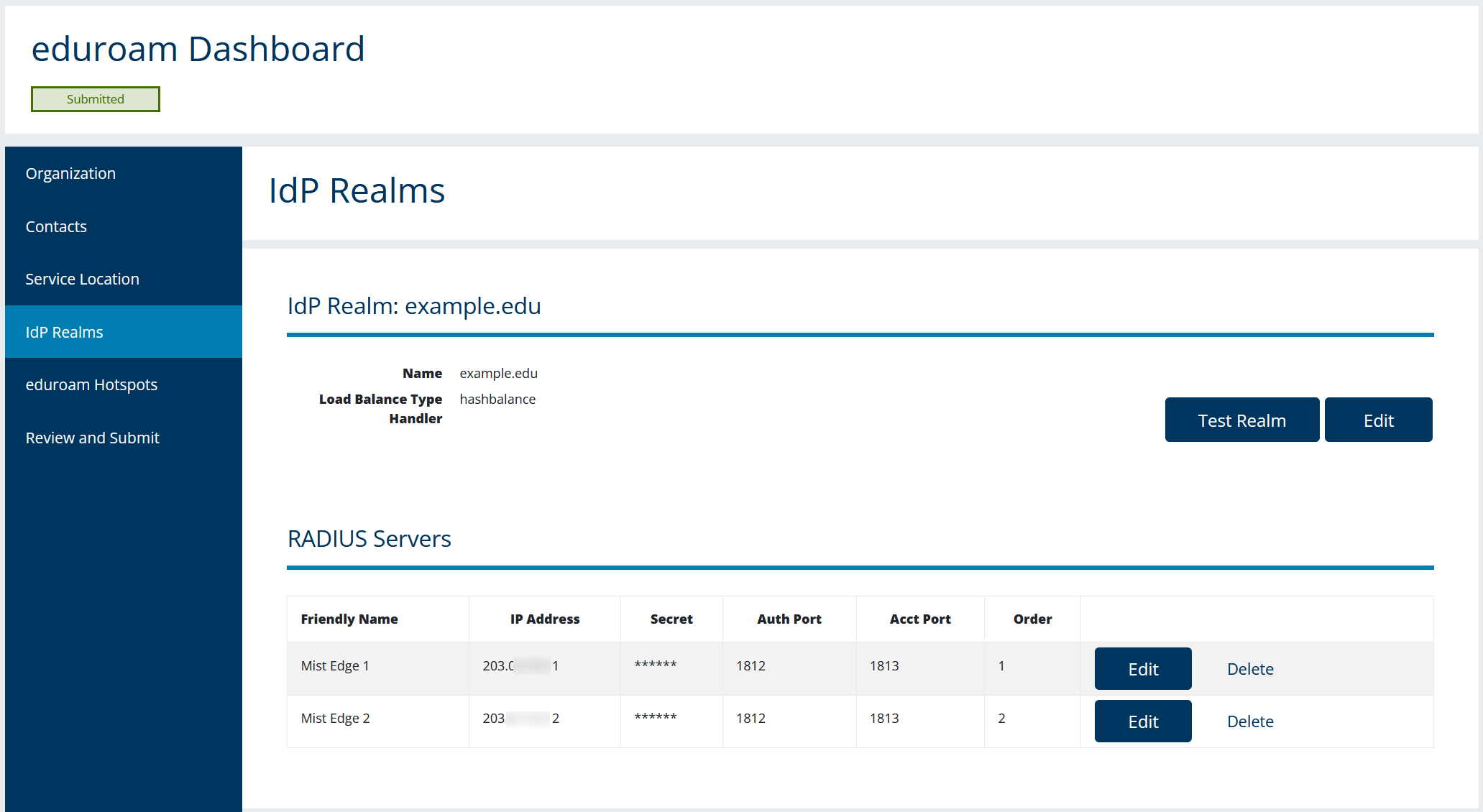
IdP configuration (home roaming users):
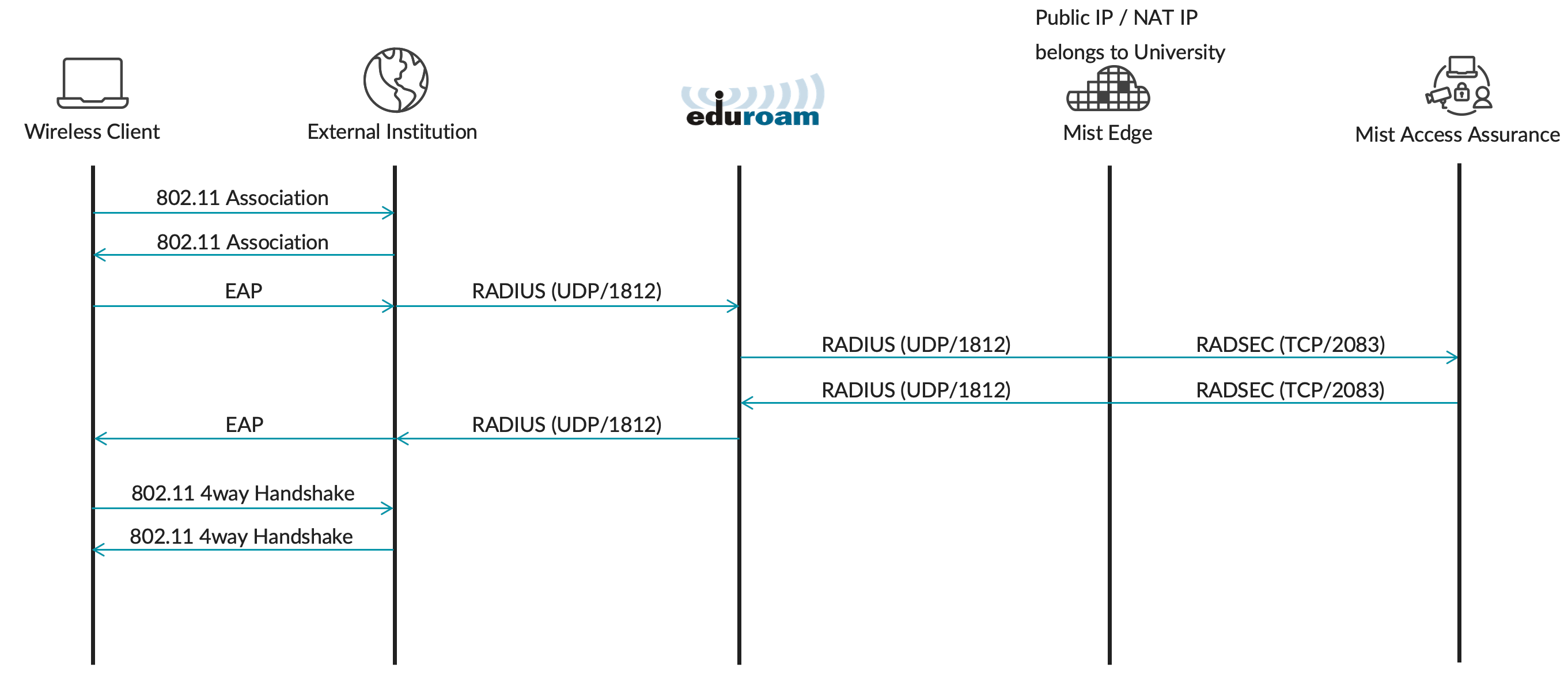
Verification
For both home and external visitors all related events can be found in either Client Insights page or under NAC Events in the Auth Policies page. Note that for external users only NAC Client Access Allowed or Denied event will be generated without any other NAC events, due to the fact that authentication is handled by an external RADIUS server (eduroam):