Overview
Mist Access Assurance allows you to integrate natively into JAMF Pro Endpoint Management platform for the purposes of checking managed endpoint compliance state. JAMF managed devices (macbooks, iOS or iPadOs mobile devices) are evaluated by JAMF for compliancy using Smart Computer Groups for macbooks and Smart Device Groups for iPads and iOS devices (presence of an antivirus, firewall status, software version, and so on). Mist Access Assurance obtains the compliance state of the device and leverages that state in Auth Policy rules to perform posture assessment.
JAMF Device Data Retrieval
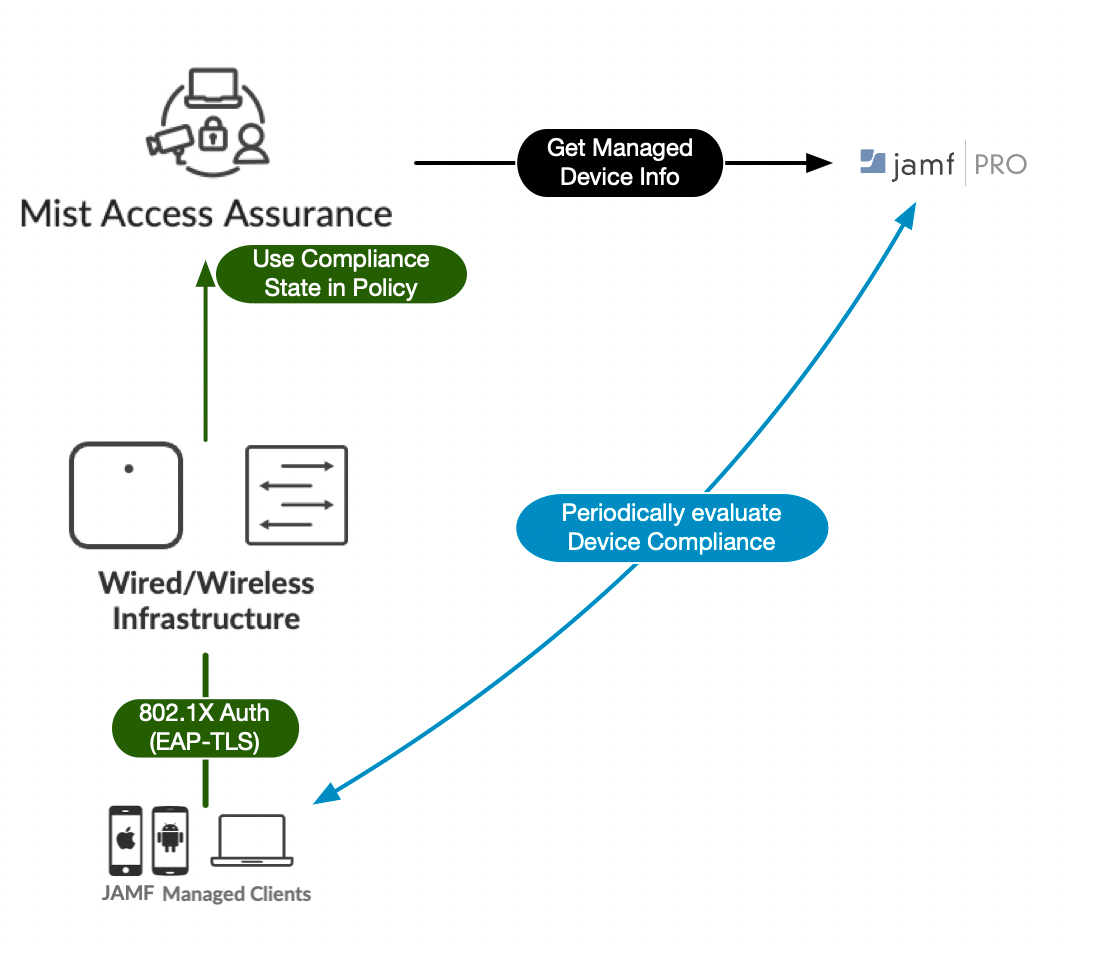
The following diagram outlines high-level authentication and authorization flow when JAMF integration is enabled:
Mist Access Assurance retrieves JAMF managed device data in the following manner:
-
Access Assurance uses API based polling mechanism towards JAMF every 2 hours for every managed client that has previously authenticated. Compliance state information is cached for fast retrieval.
-
Information retrieval is performed out-of-band, i.e. after the authentication process to avoid any additional delays. After initial device onboarding, information is updated every 2 hours.
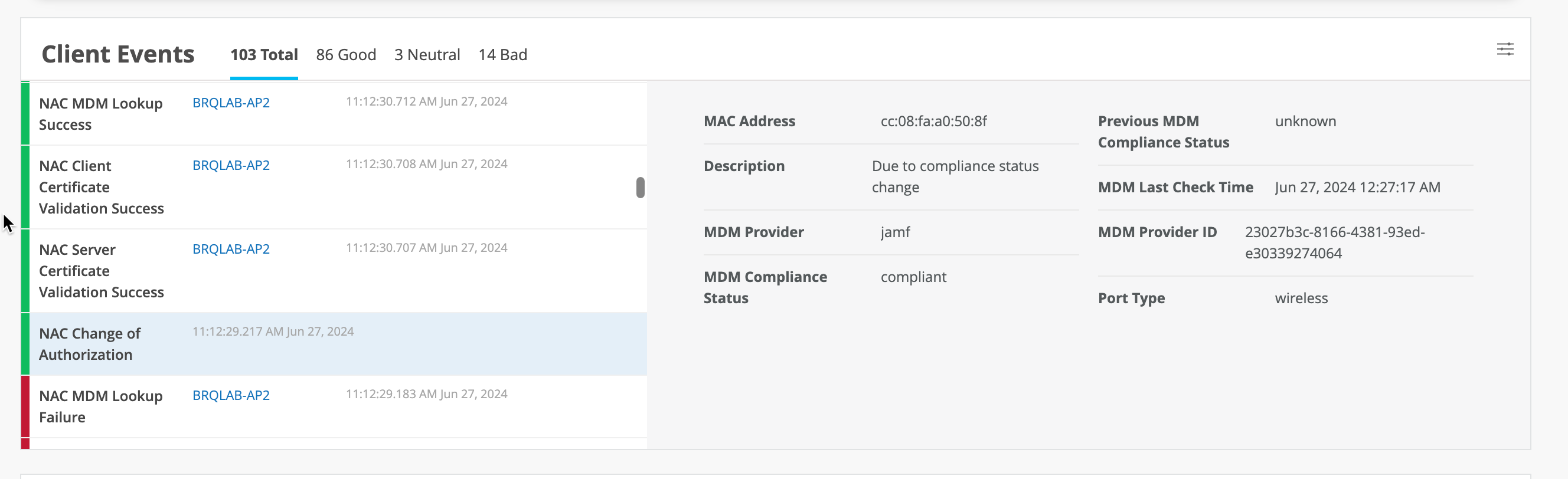
- In case device compliance status changes, then Mist Access Assurance would automatically trigger a Change Of Authorization to re-run the policy and apply respective action.
- Mist APs require firmware version of 0.14. or above
The following info during client authentication can be used to correctly match a client with a device record in Microsoft Intune:
- Non-randomized MAC address. This method can be used with EAP-TTLS or EAP-TLS authentication, client device MAC is matched with a device MAC present in JAMF. For WiFi profile make sure mac randomization or rotation is disabled. Note that most Apple device do not have native ethernet NIC, so this method is only useful with wirelessly connected Apple devices.
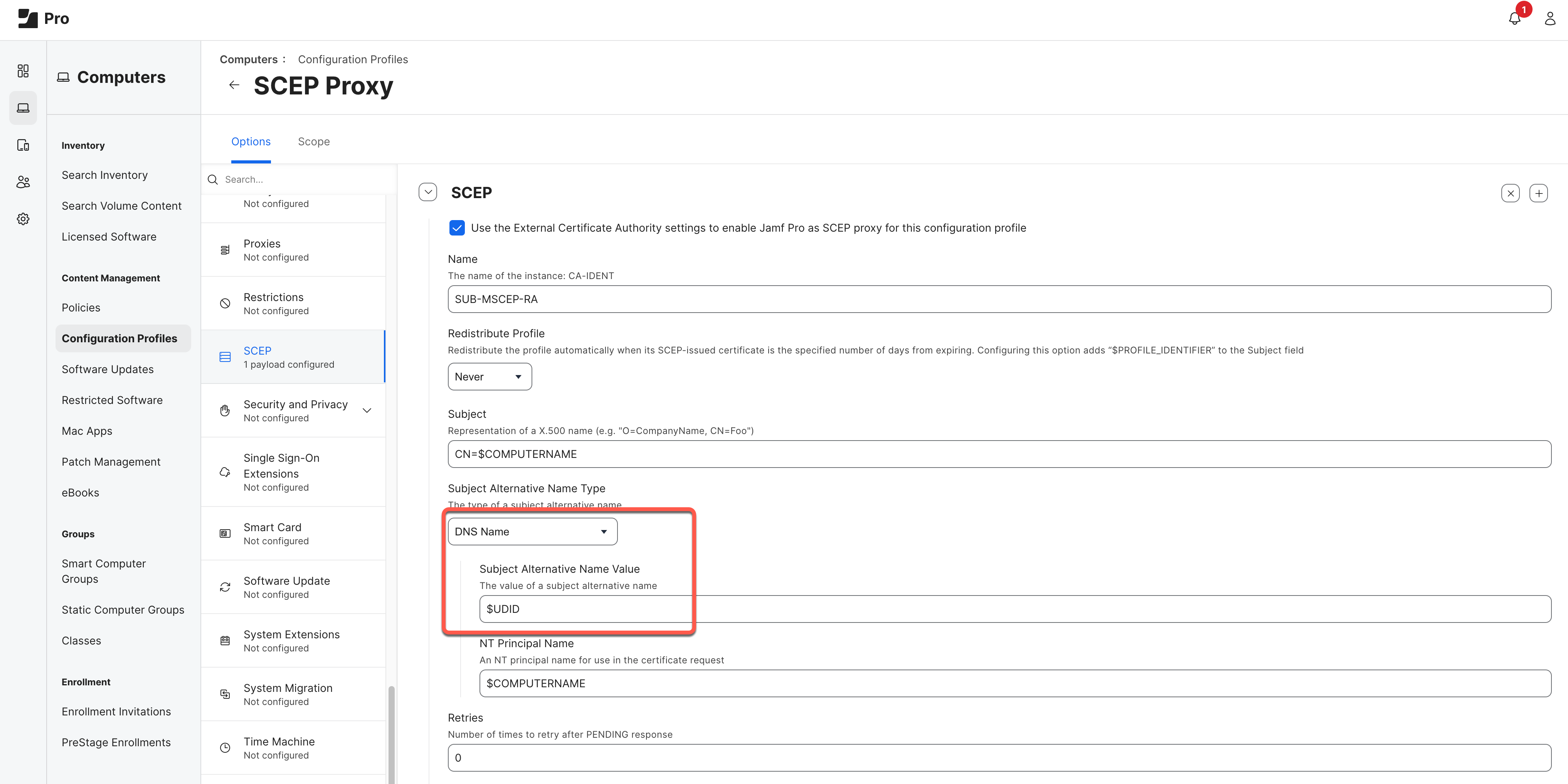
- JAMF Device UDID encoded in SAN:DNS certificate attribute, for example:
Configuration
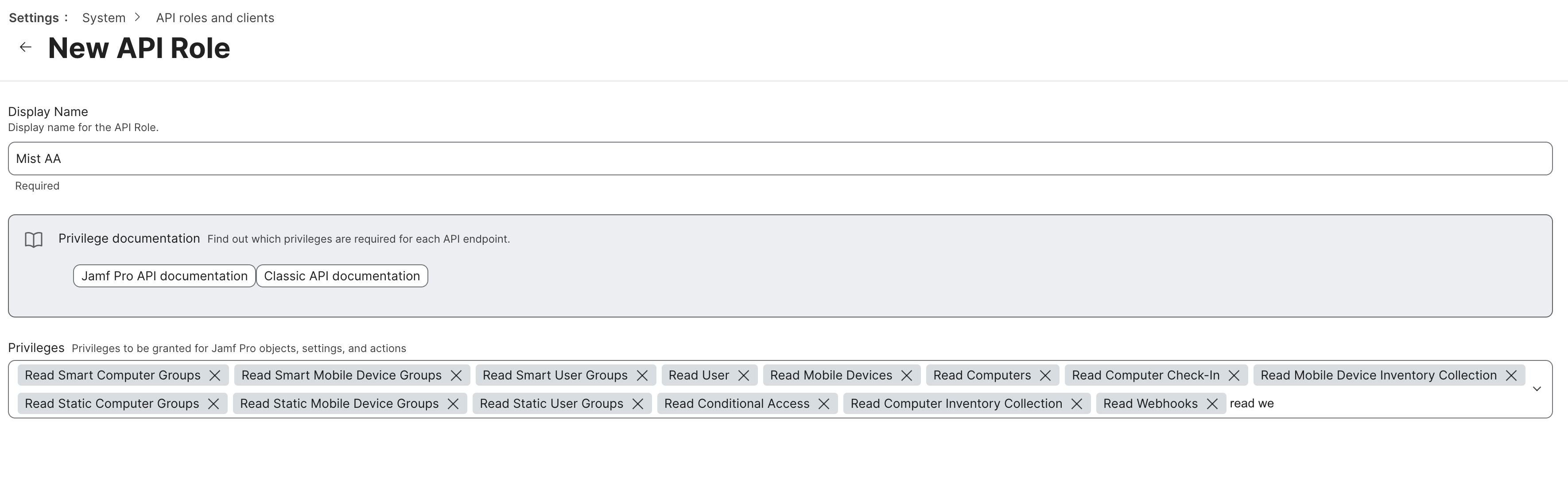
Create Client ID and Secret on the JAMF Pro
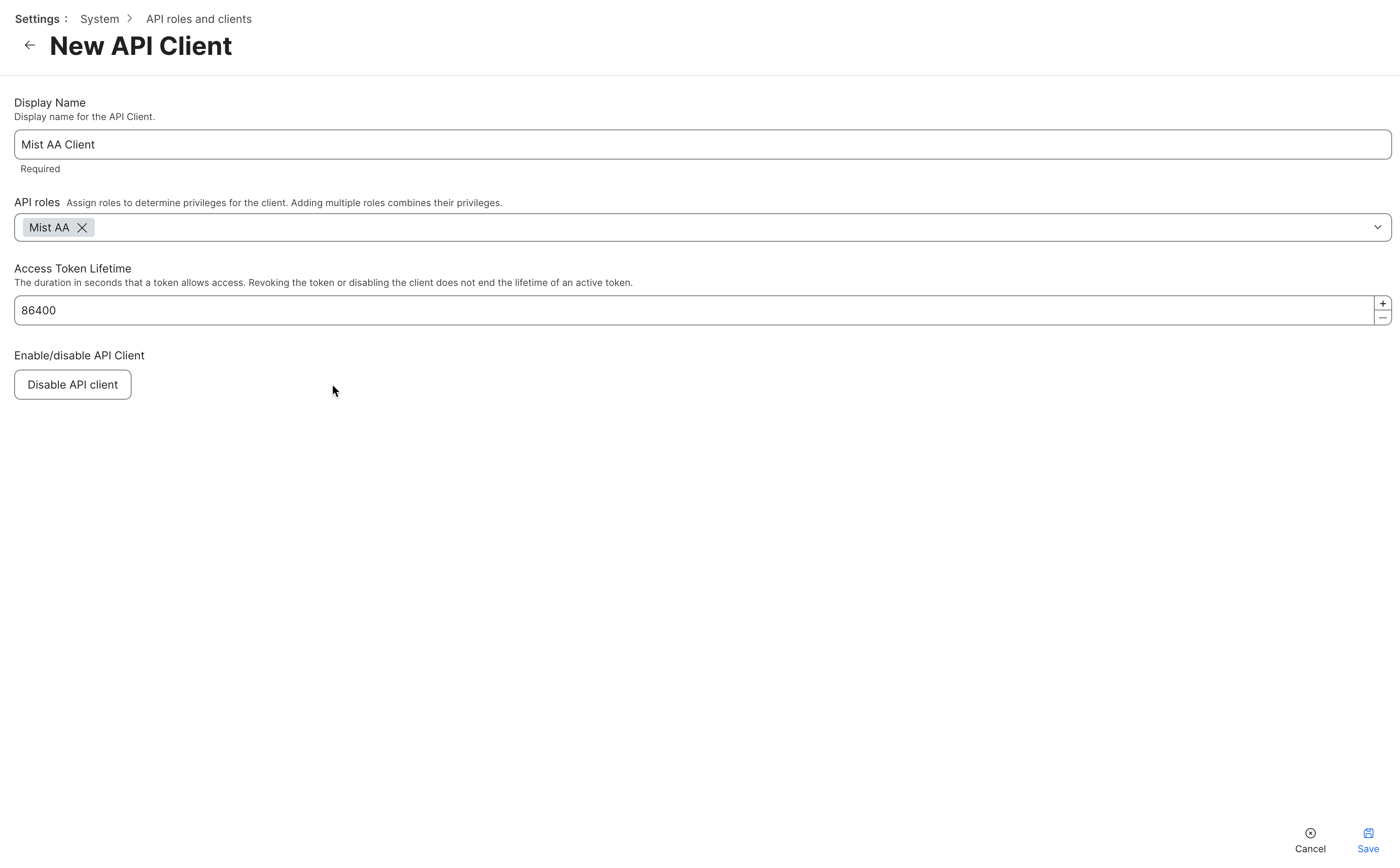
In the JAMF Pro dashboard navigate to Settings > API roles and clients. First, create a role for Mist Access Assurance connector. Assign the following read-only permissions:
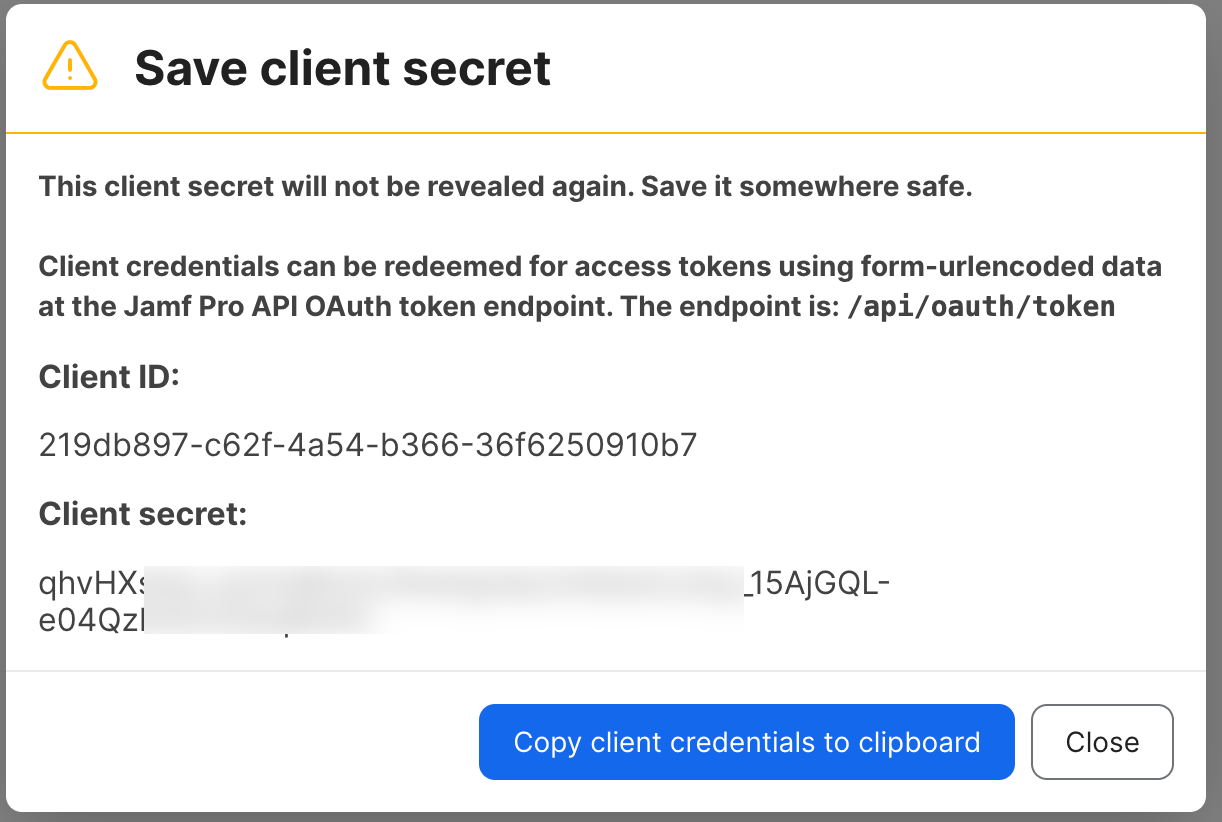
 Then navigate to API Clients tab and add new client, select the API role created in the previous step and set access token refresh time to longer period like 24 hrs. Then client Enable API Client.
Then navigate to API Clients tab and add new client, select the API role created in the previous step and set access token refresh time to longer period like 24 hrs. Then client Enable API Client.Link JAMF Pro Account
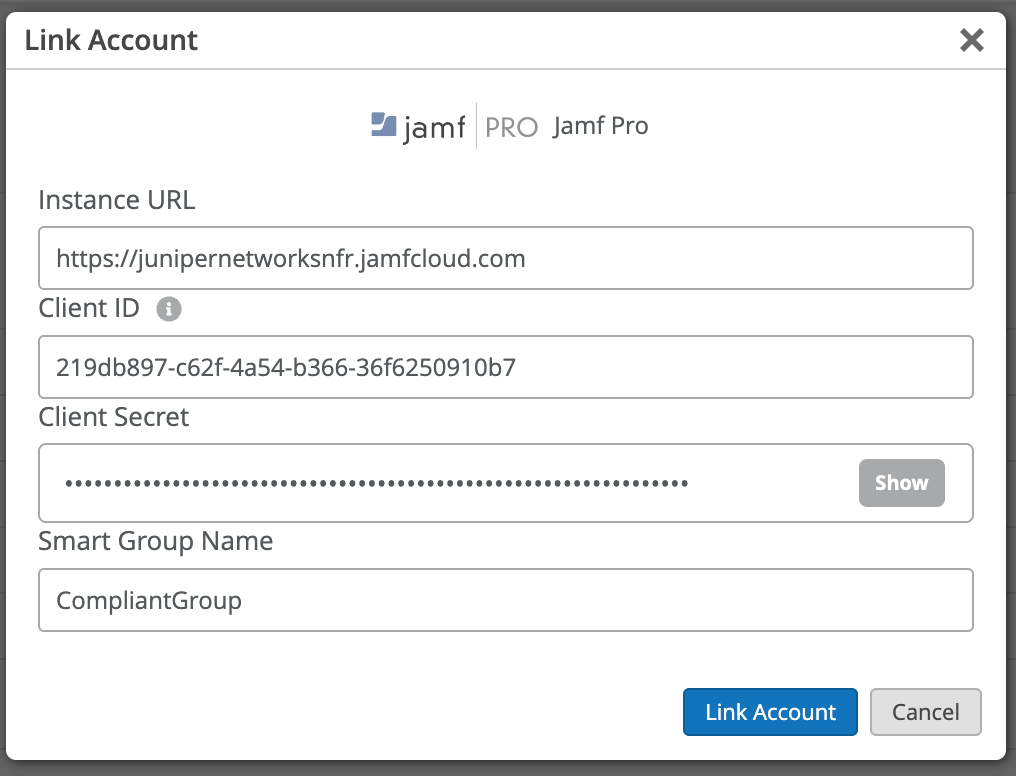
Now, in the Mist dashboard navigate to Organization > Access > Identity Providers tab, then click on Link Account and select JAMF Pro:
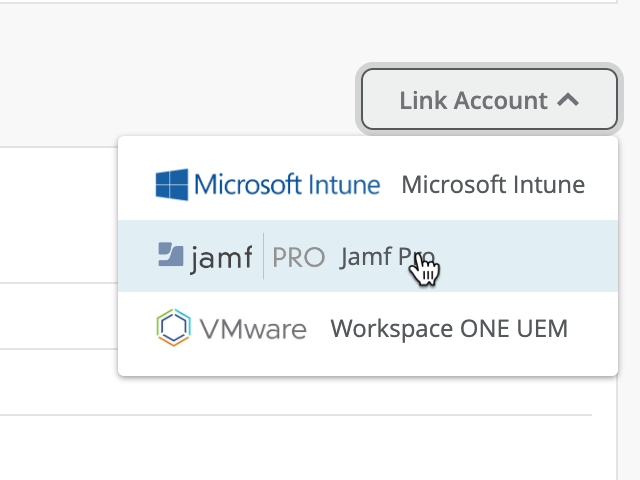
In the pop up provide Client ID, Client Secret, your JAMF Pro instance URL (e.g. https://<yourjamfurl>.com) and the Smart Group Name that we will match against. Smart Groups (both computer and mobile device smart groups) offer dynamic rule based matching, which allows you to set policies like running software, OS versions etc of your managed devices. In case a client is found in JAMF and is part of selected SmartGroup then it is considered as MDM compliant.
Note: please remove any trailing / in the Instance URL field.
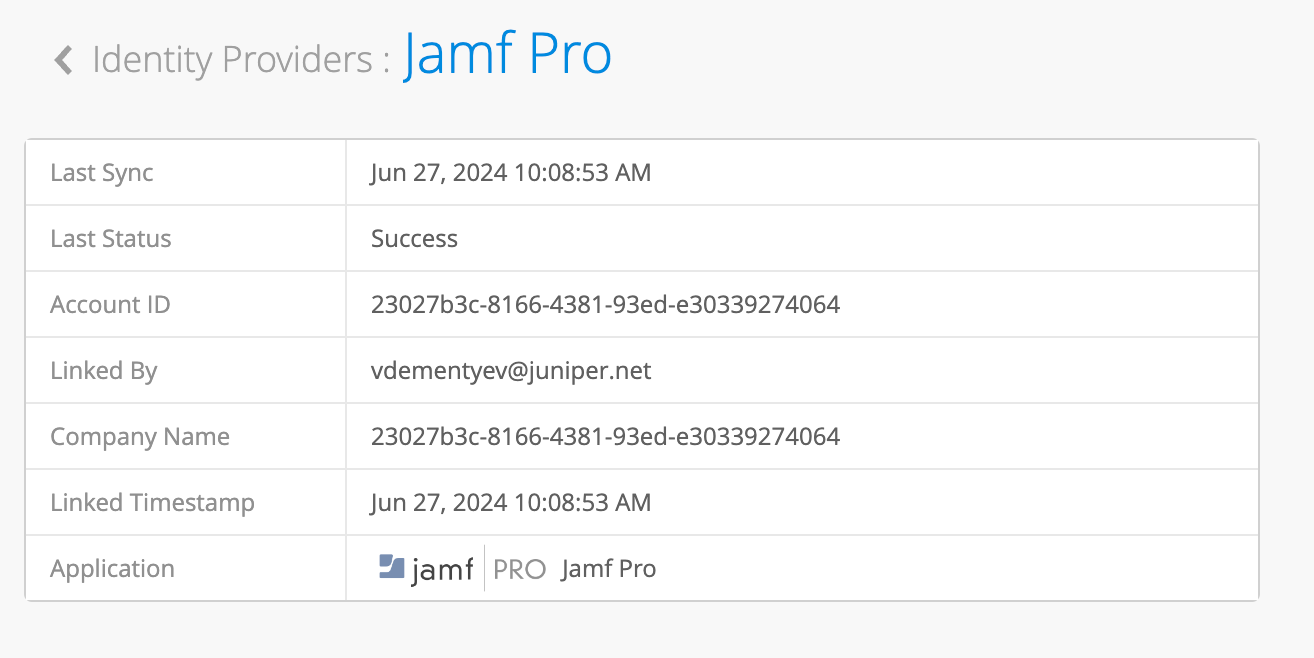
After linking is completed you can see last sync status and time:
Verification
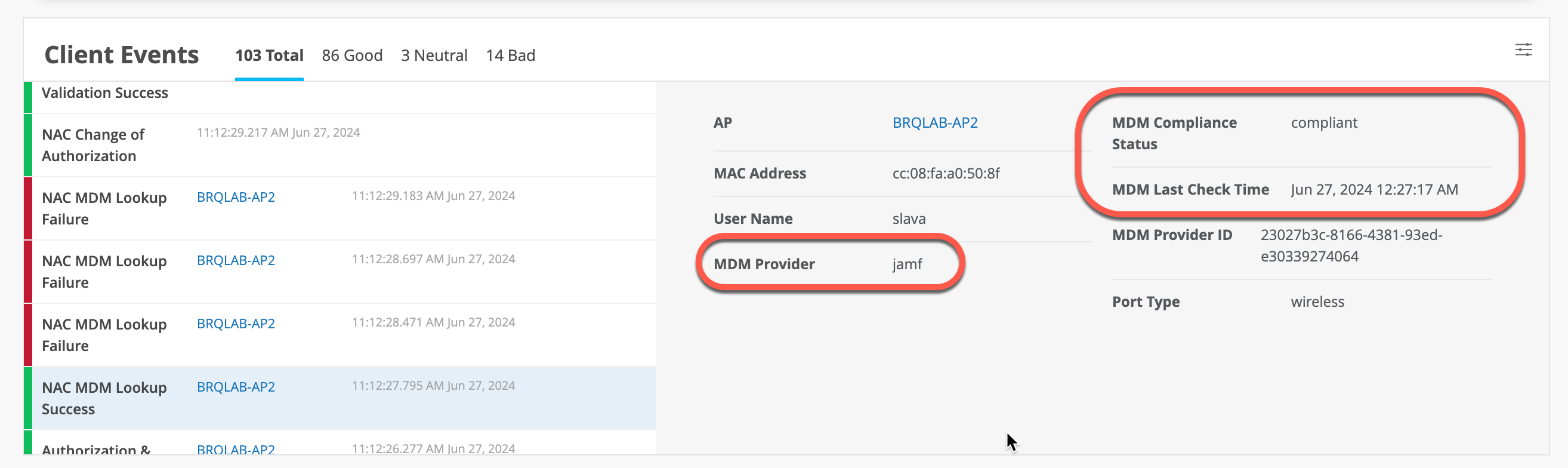
Under Client Insights you should now see MDM lookups happening for Apple managed devices:
Note that during initial MDM lookup for a new client, lookup happens post initial authentication. After MDM state changes, Mist Access Assurance would initiate CoA to re-authenticate the client and apply correct policy. Upon subsequent authentications, NAC would use mdm cache which is updated periodically to reflect any changes (every 2 hours).