Overview
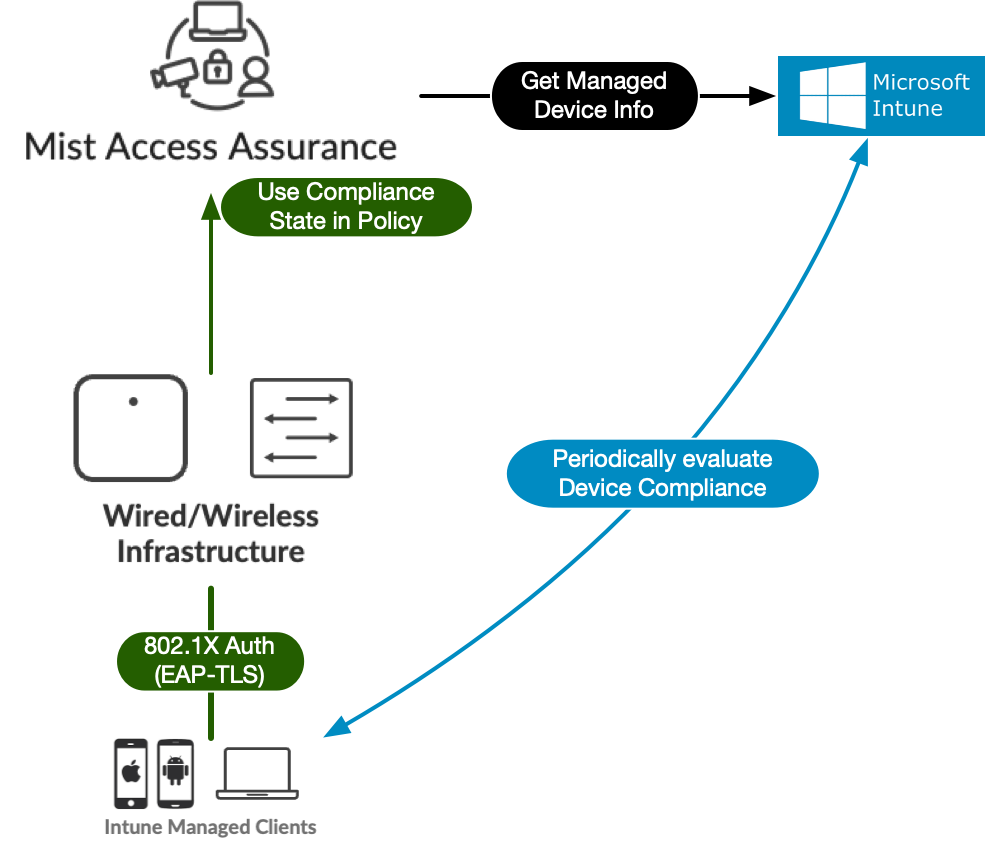
Mist Access Assurance allows you to integrate natively into Microsoft Intune Endpoint Management platform for the purposes of checking managed endpoint compliance state. Microsoft Intune managed devices (laptops, mobile devices) are evaluated by Intune for compliancy using Device Compliance Policies (presence of an antivirus, firewall status, latest security patches, and so on). Mist Access Assurance obtains the compliance state of the device and leverages that state in Auth Policy rules to perform posture assessment.
Microsoft Intune Device Data Retrieval
The following diagram outlines high-level authentication and authorization flow when Microsoft Intune integration is enabled:
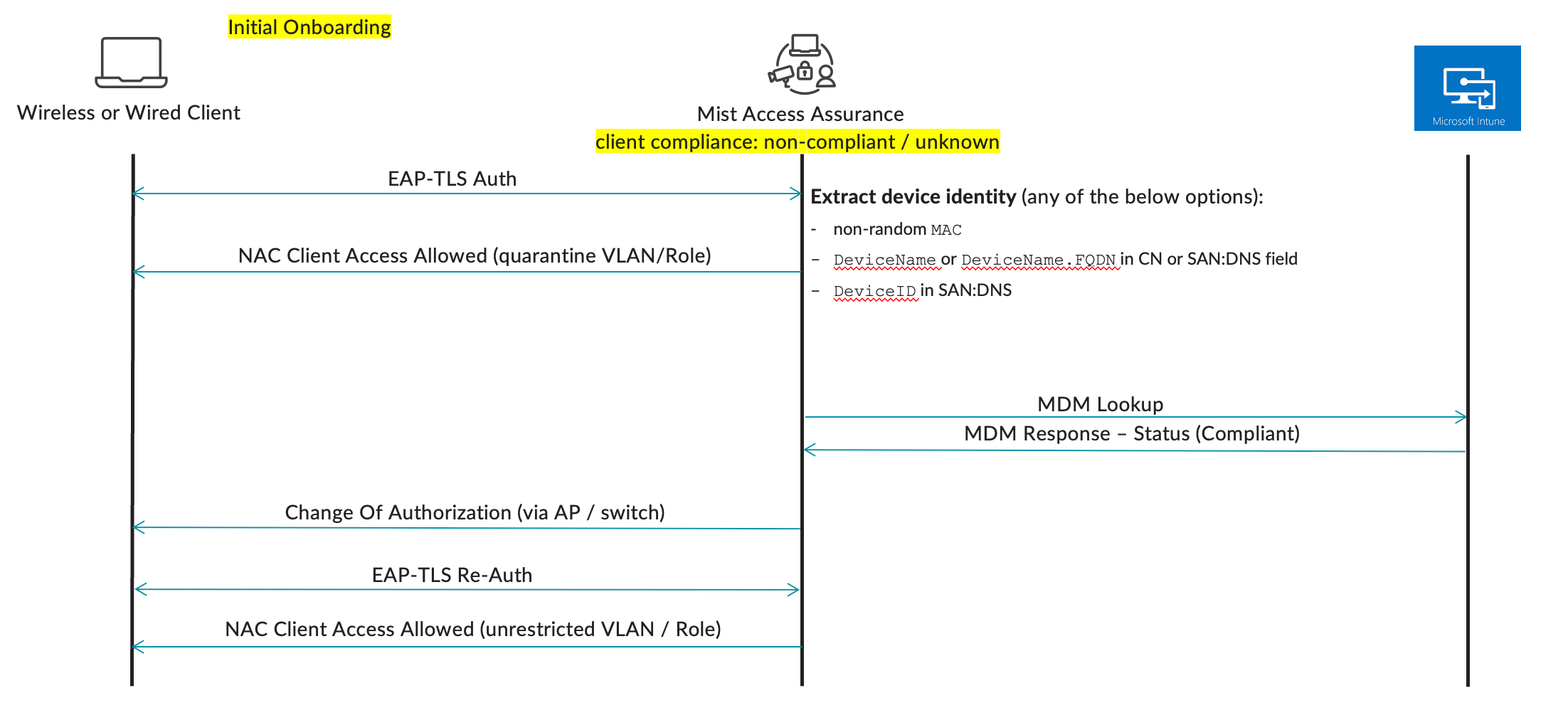
Mist Access Assurance retrieves Intune managed device data in the following manner:
-
Access Assurance uses API based polling mechanism towards Microsoft Intune (at the time of the writing Intune does not support real-time notifications) every 2 hours for every Intune-managed client that has previously authenticated. Compliance state information is cached for fast retrieval.
-
Information retrieval is performed out-of-band, i.e. after the authentication process to avoid any additional delays. After initial device onboarding, information is updated every 2 hours. Note that typical Intune to device sync time is 8 hours (see more here).
- In case device compliance status changes, then Mist Access Assurance would automatically trigger a Change Of Authorization to re-run the policy and apply respective action.
- Mist APs require firmware version of 0.14. or above
The following info during client authentication can be used to correctly match a client with a device record in Microsoft Intune:
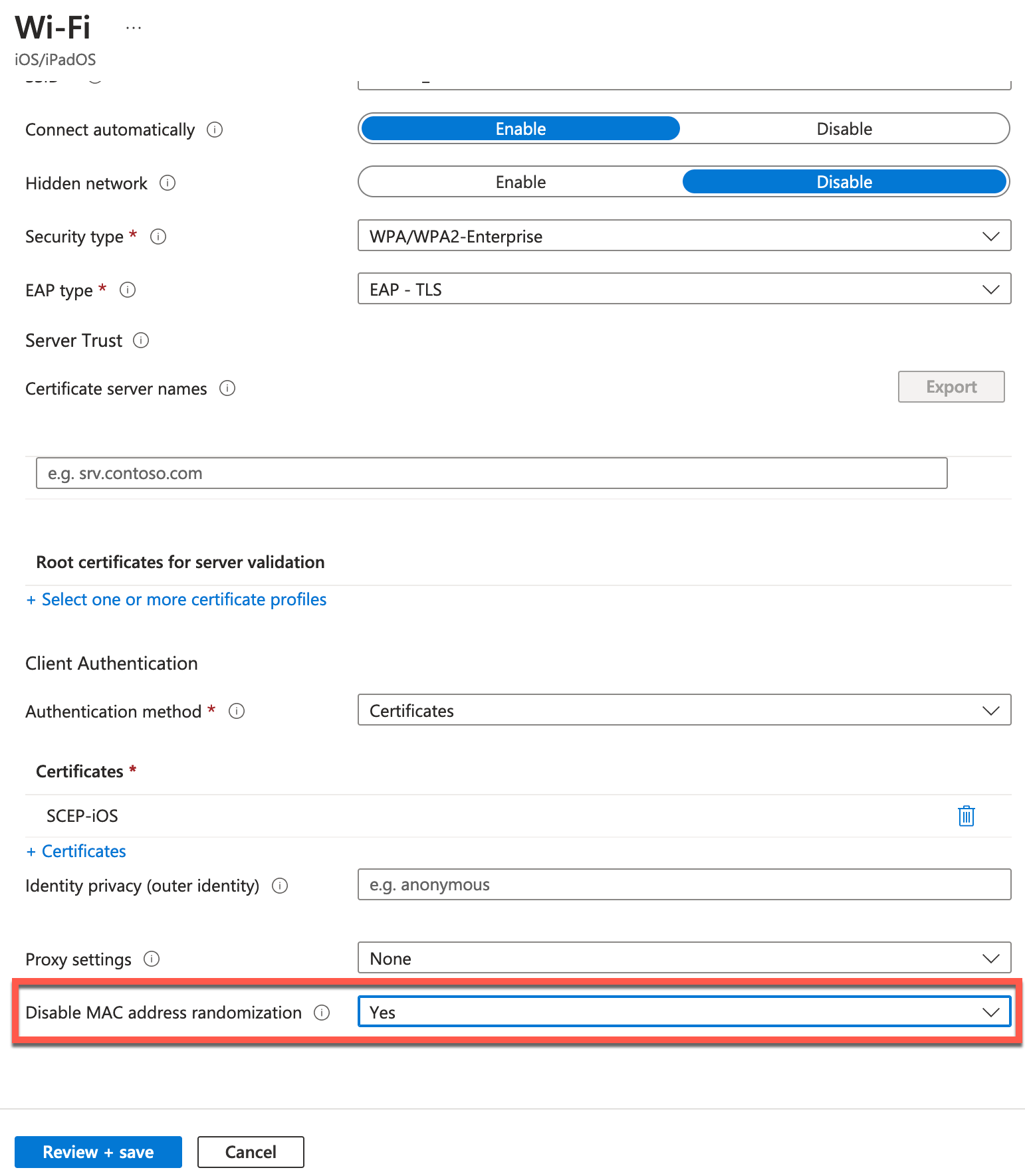
- Non-randomized MAC address. This method can be used with EAP-TTLS or EAP-TLS authentication, client device MAC is matched with a device MAC present in Intune. For WiFi profile make sure mac randomization is disabled, which you can achieve by Intune configuration following this example:
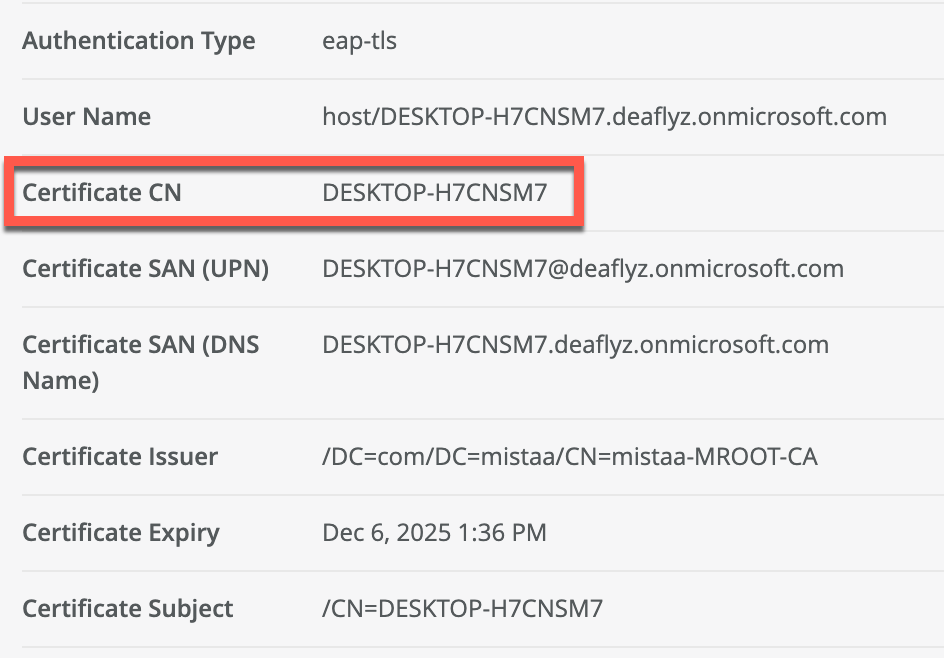
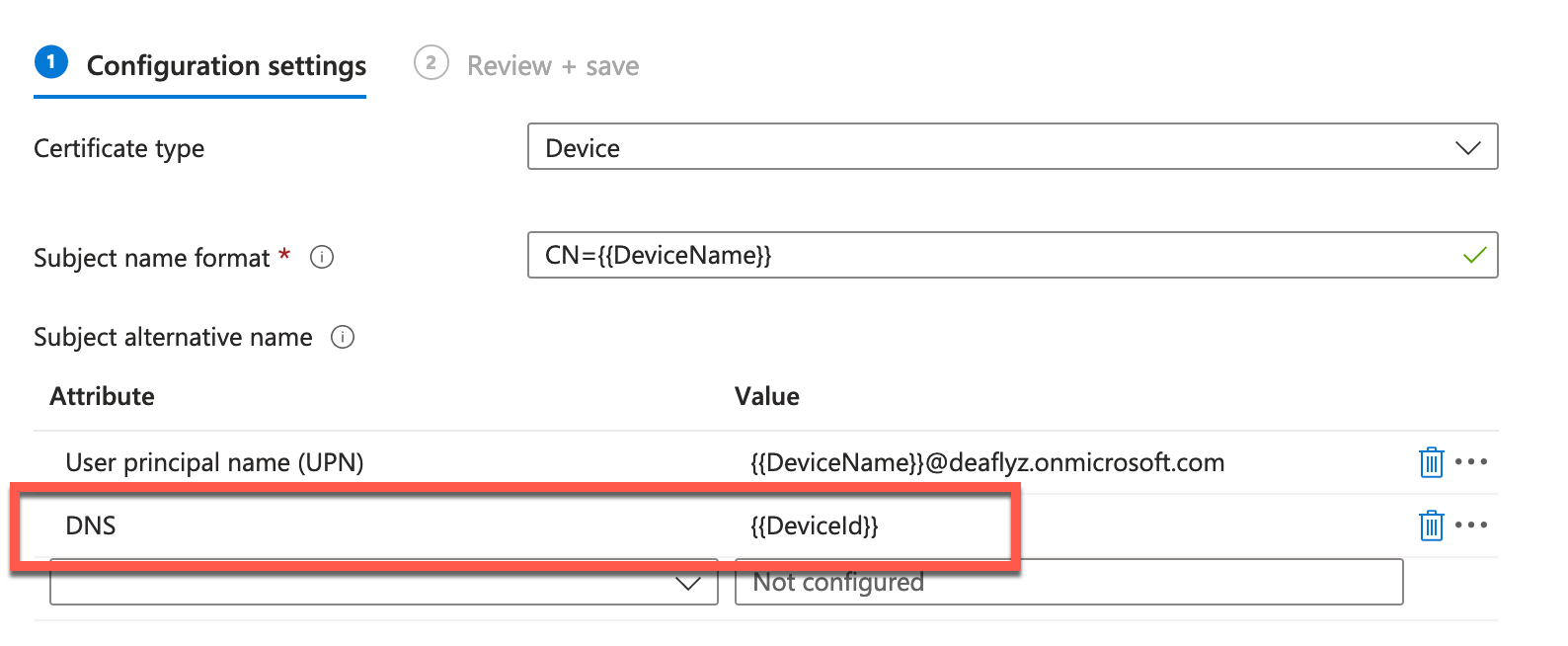
- DeviceName or DeviceName.FQDN used as CN certificate field during machine authentication, for example:
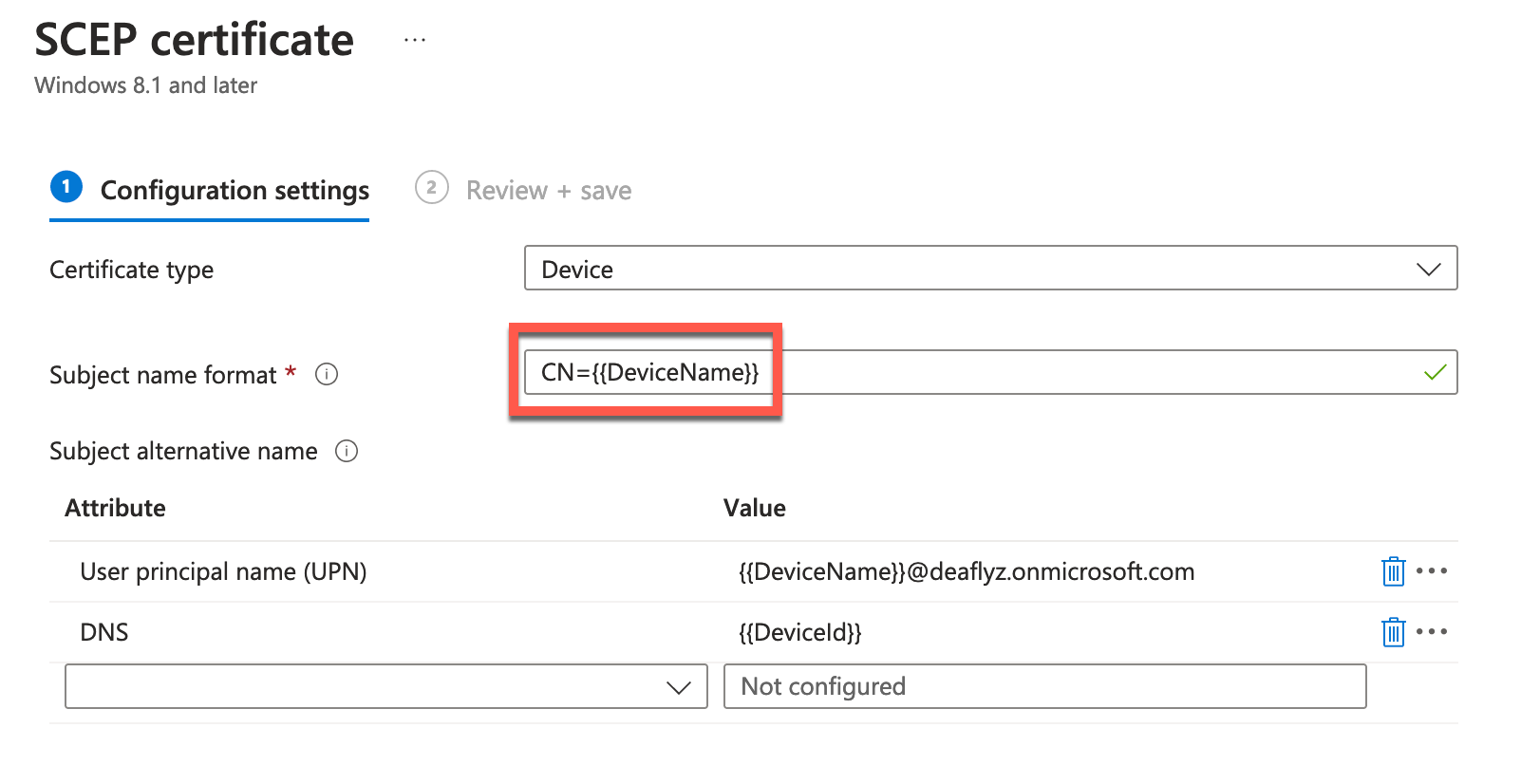
In Intune SCEP profile use the following variables to create this certificate:
- Intune Device ID encoded in SAN:DNS certificate attribute:
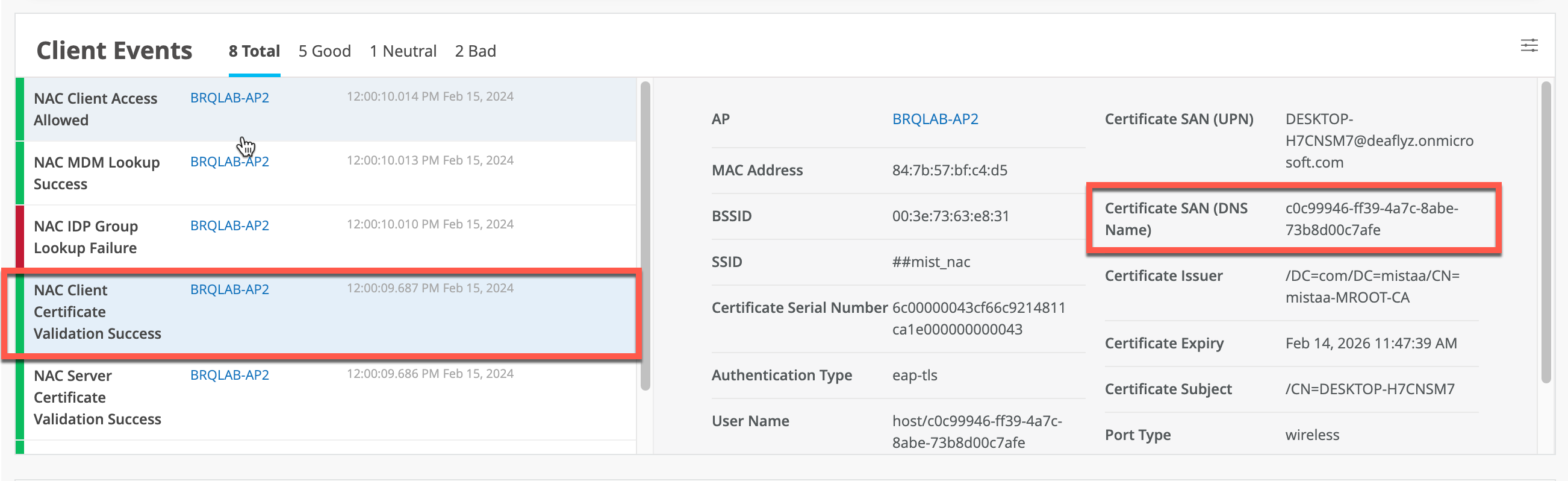
In Intune SCEP profile use the following variable to encode Intune Device ID in the SAN:DNS certificate field:
Configuration
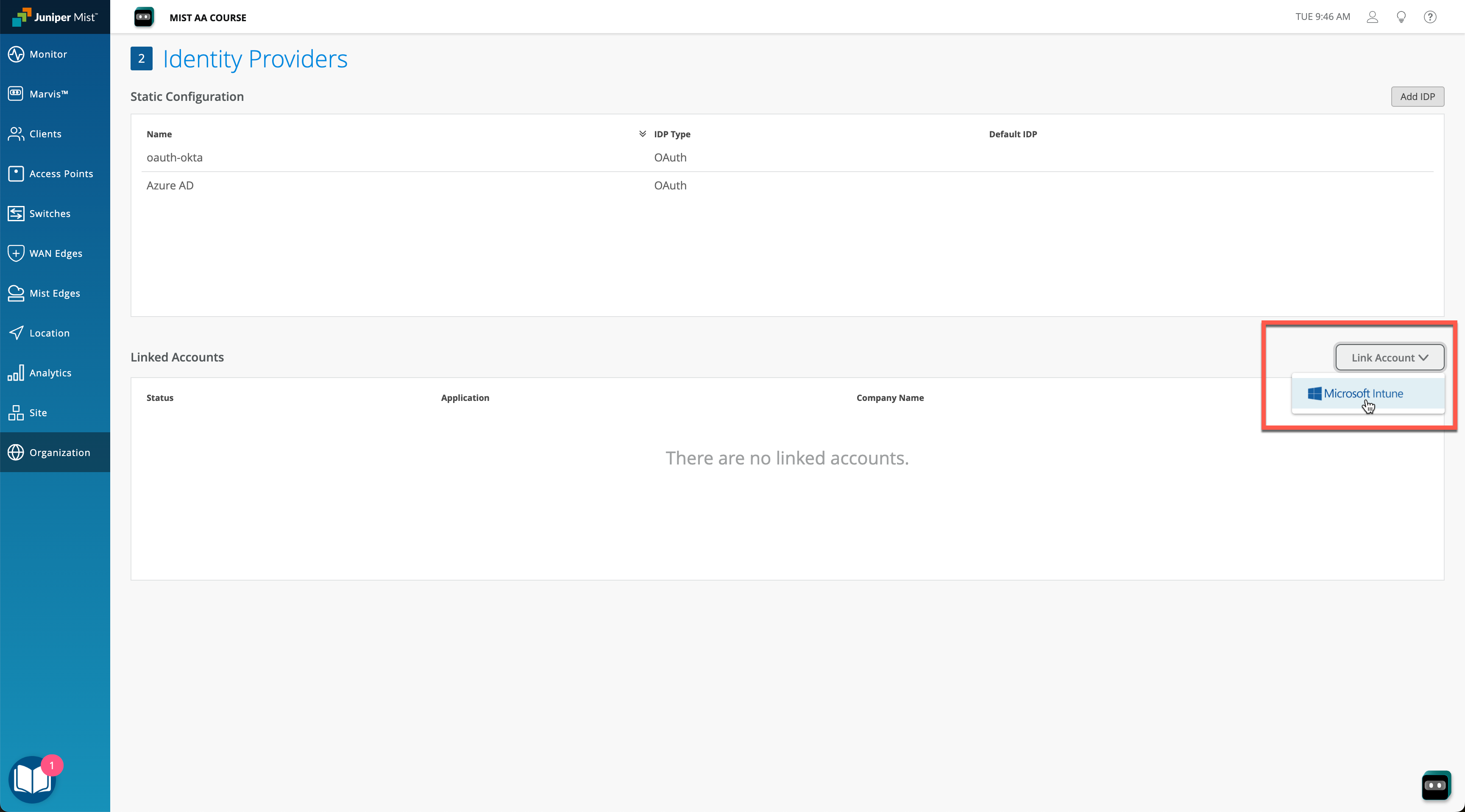
Link Microsoft Intune Account
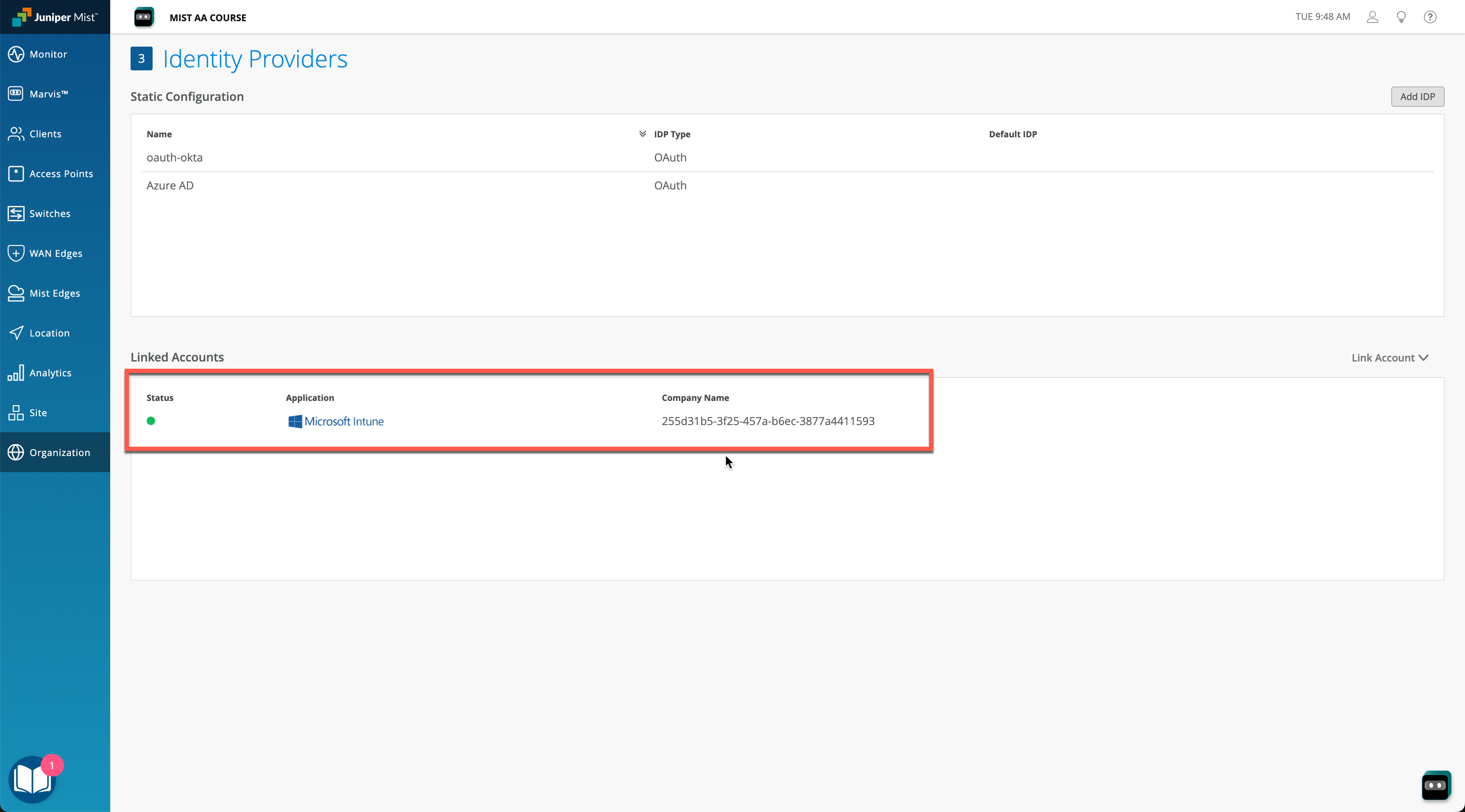
In order to integrate with Microsoft Intune, navigate to Organization > Access > Identity Providers tab, then click on Link Account and select Microsoft Intune:
Upon attempting to link Intune account, you will be redirected to Microsoft Entra ID / Intune for SSO login:
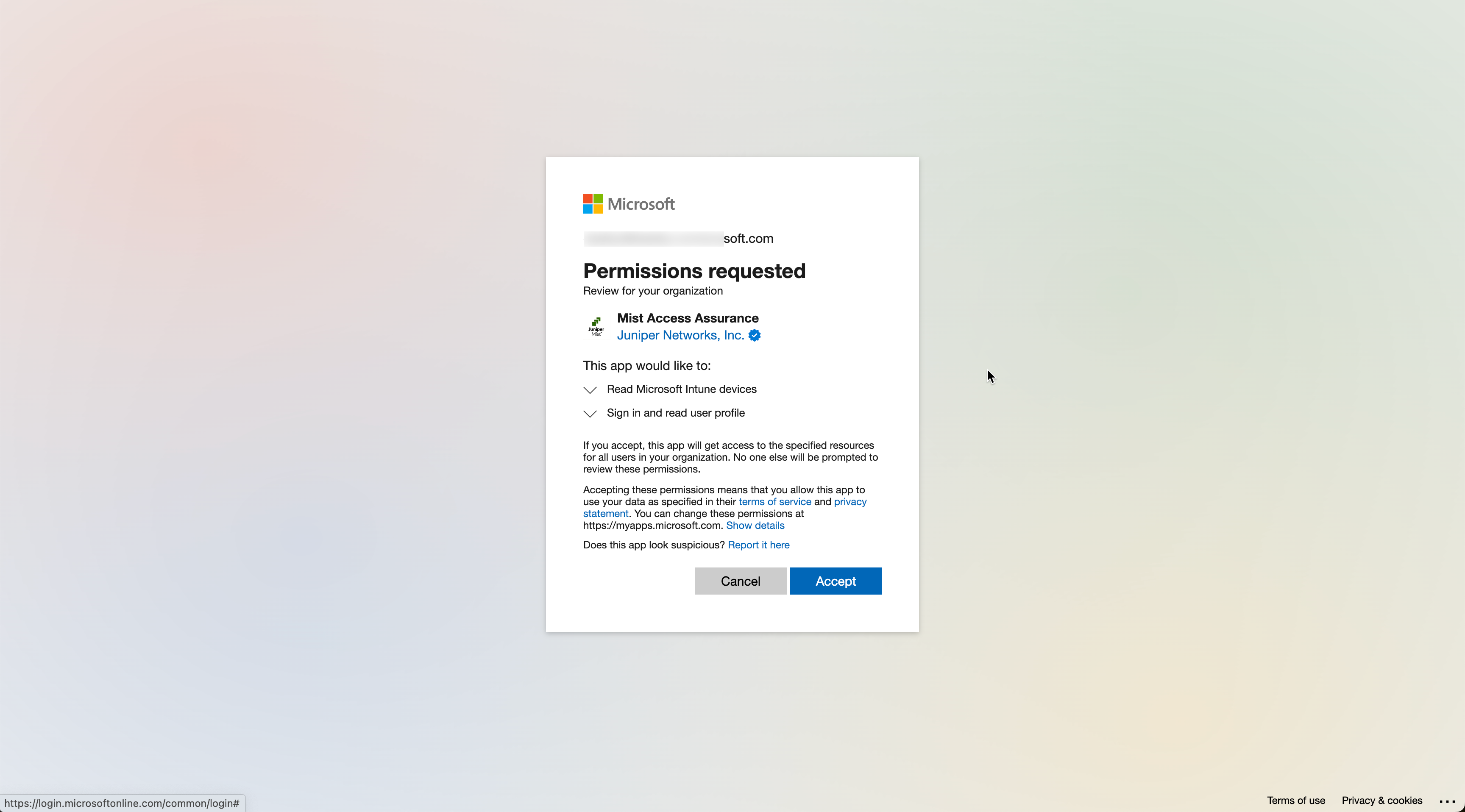
Note that for the integration to work you would need to grant permissions to read Microsoft Intune device data, which generally requires Global Administrator or Privileged Admin role on the Microsoft Entra ID side:
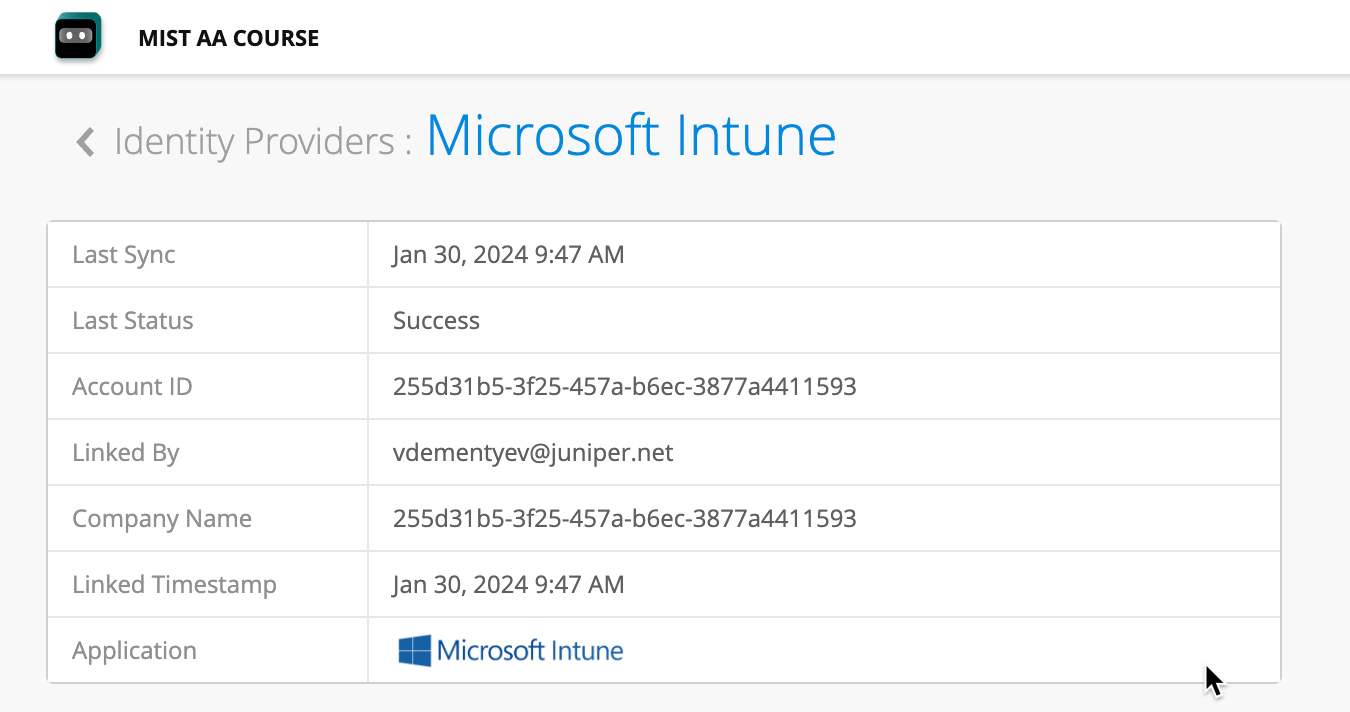
Once the Intune accounted is linked, you will see connected Intune account status on the Identity Providers page:
Use Compliance Status in Auth Policy Rules
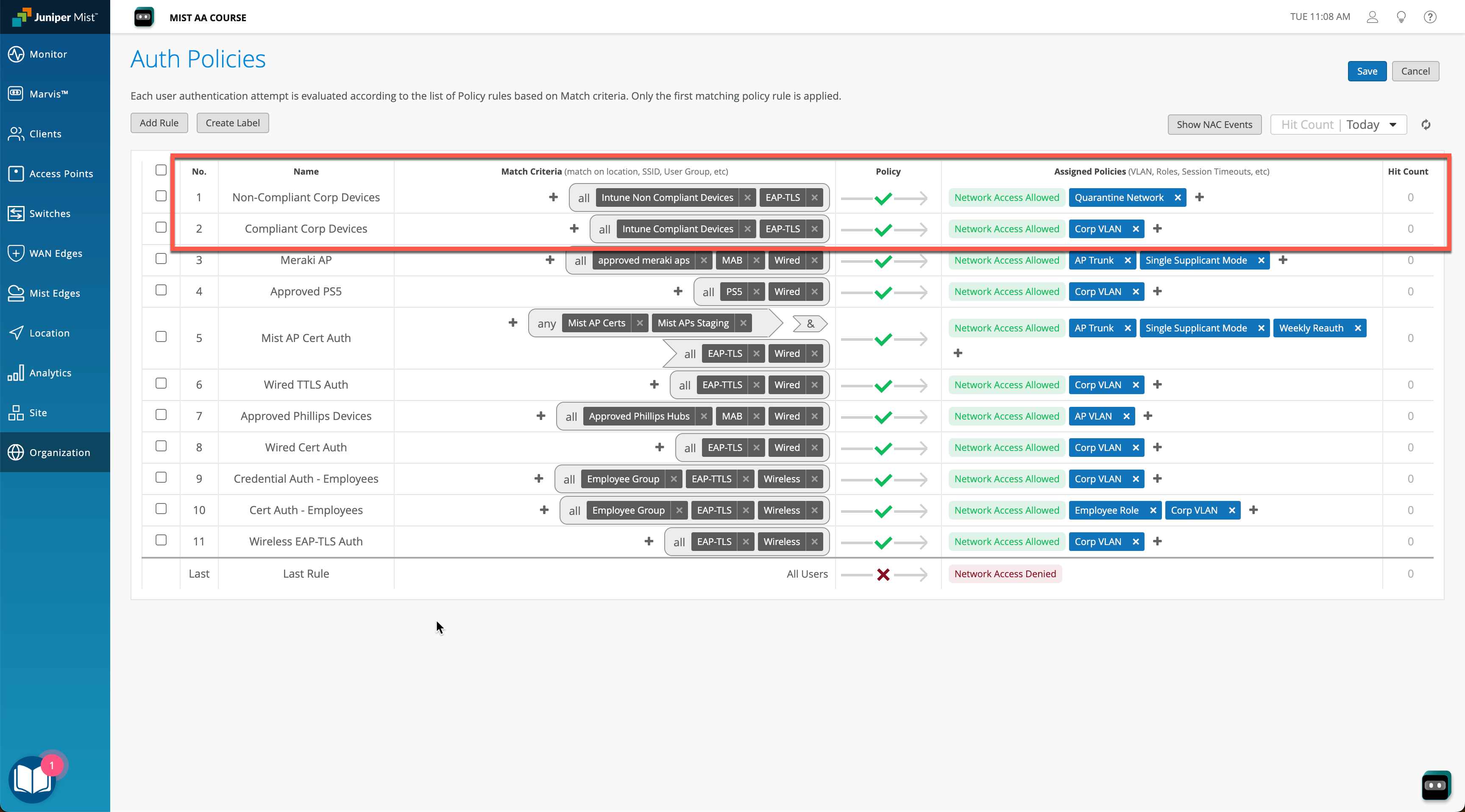
Now as we have Intune account linked, we are able to leverage managed device compliance status in Auth Policy Rules. The most common use-case is to move clients into quarantine VLAN/Role if a device is not compliant, while allowing compliant devices to connect to the unrestricted VLAN.
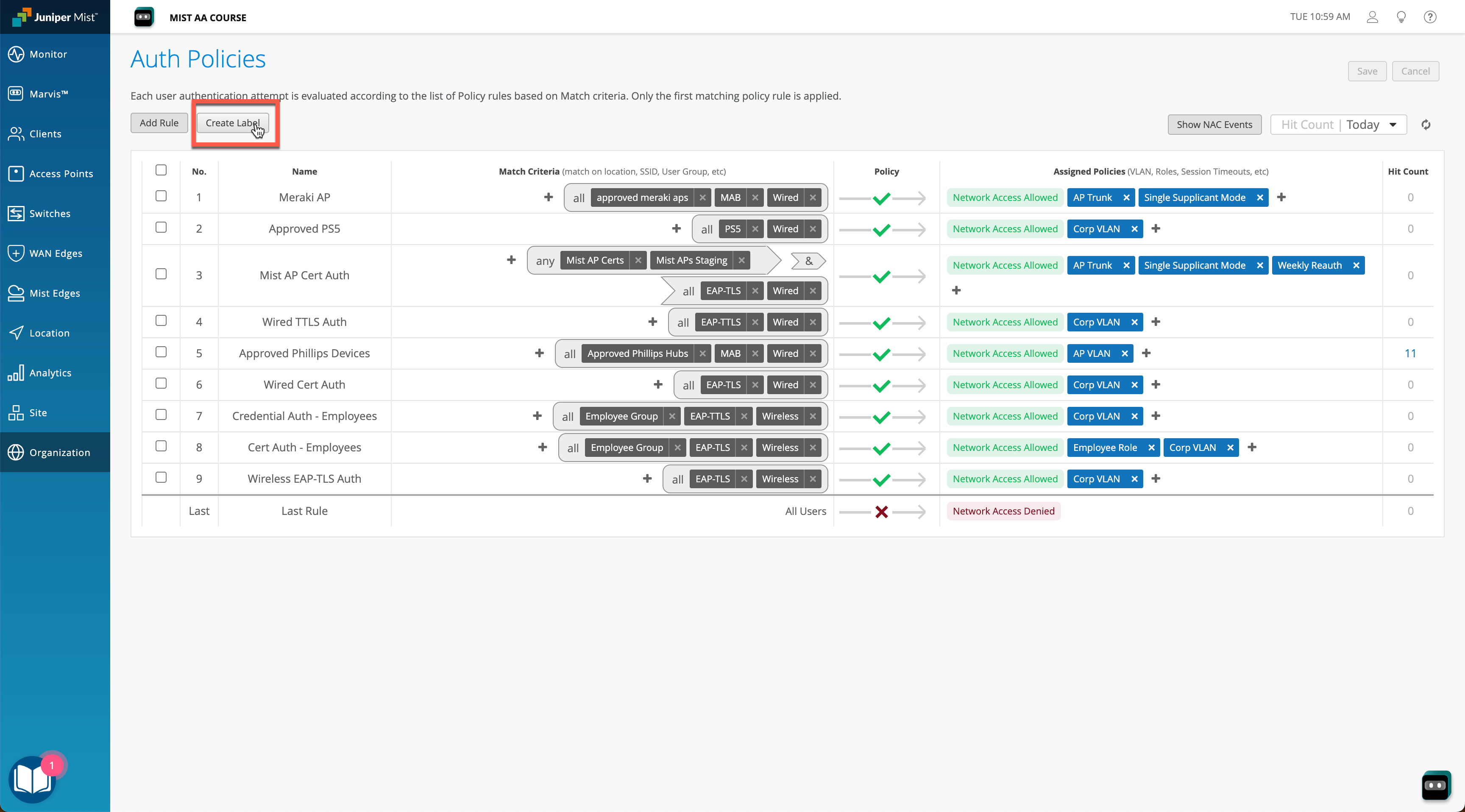
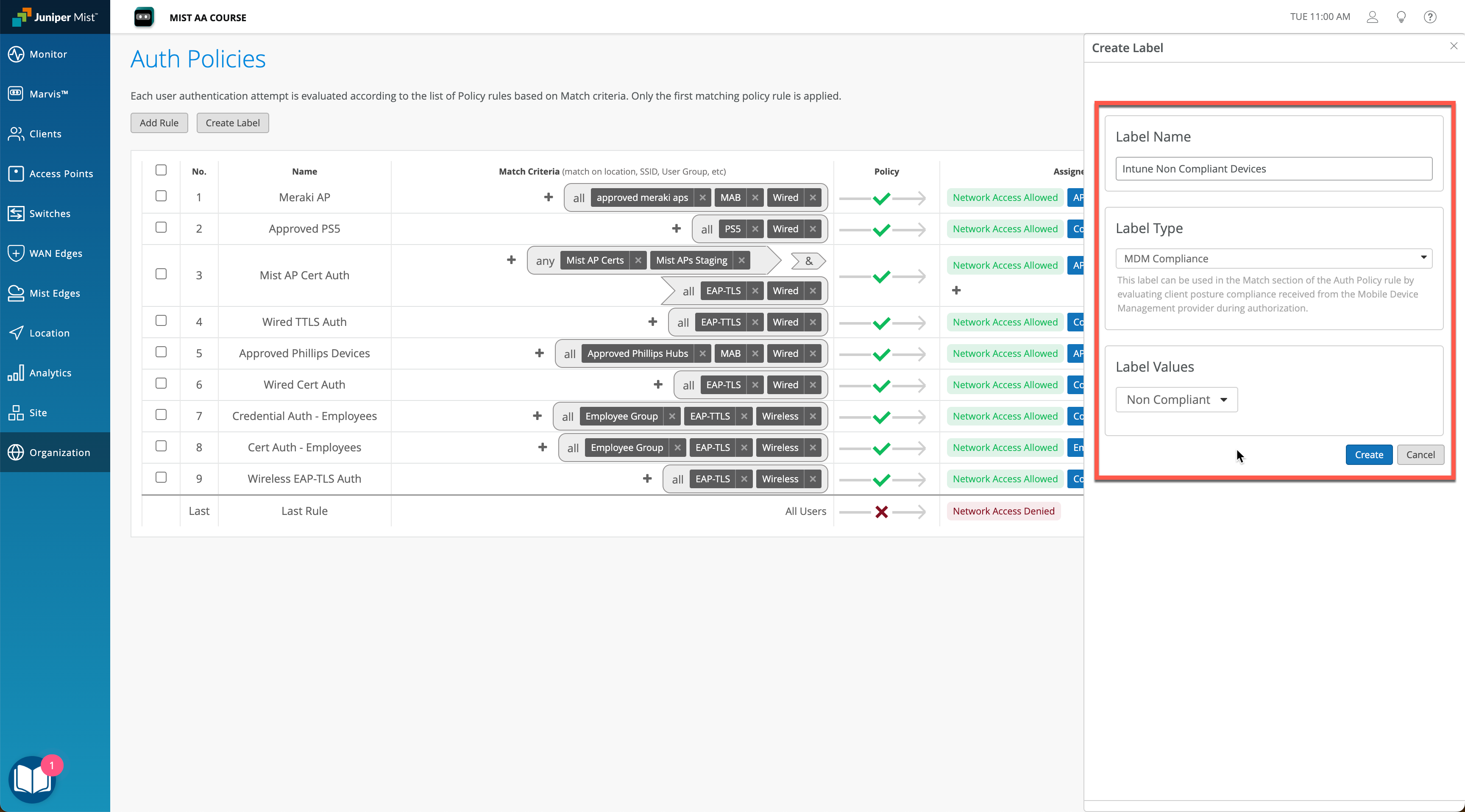
Navigate to Organization > Access > Auth Policies page and click Create Label:
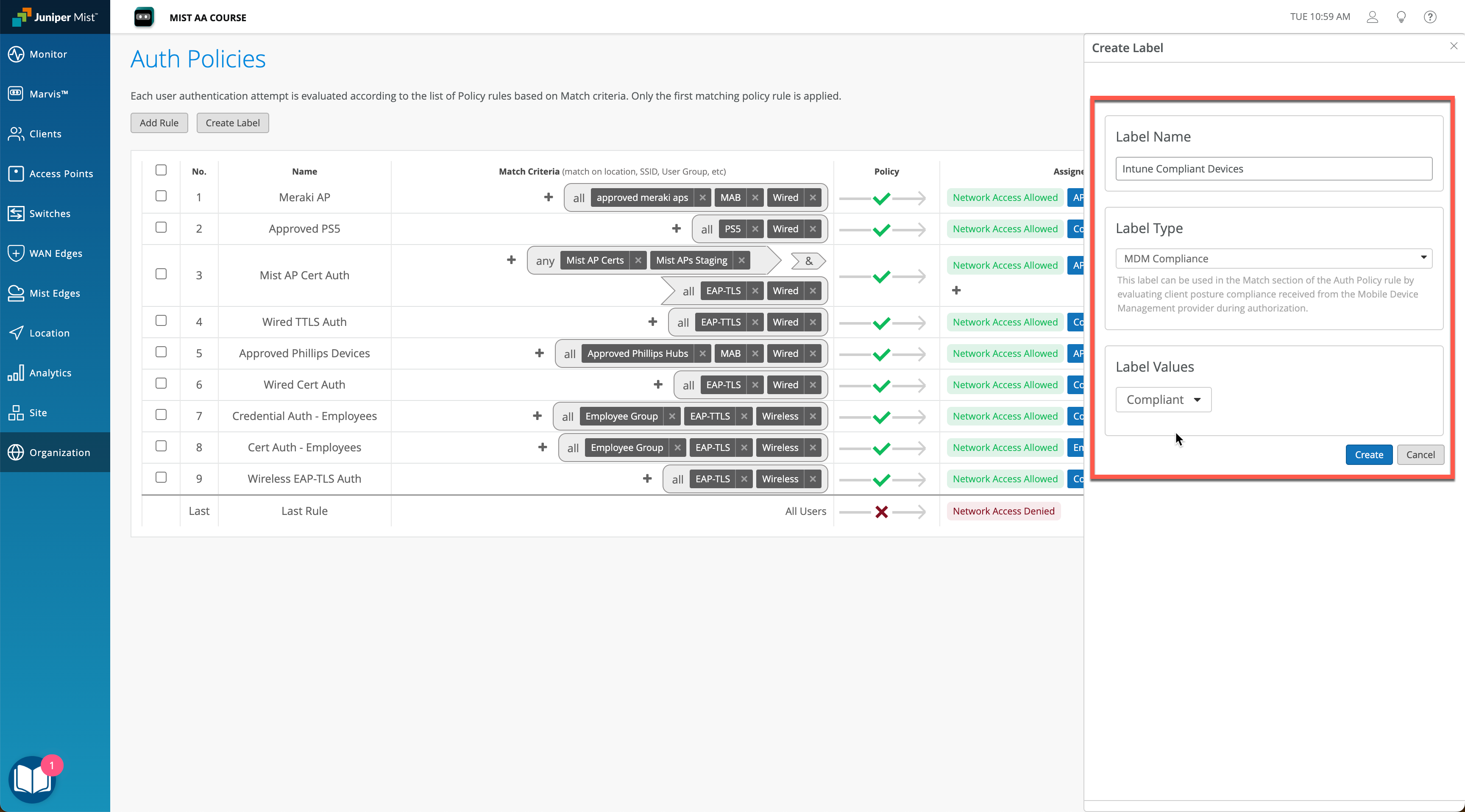
Select Label Type as MDM Compliance. Create two labels, one for compliant and another one for non-compliant devices:
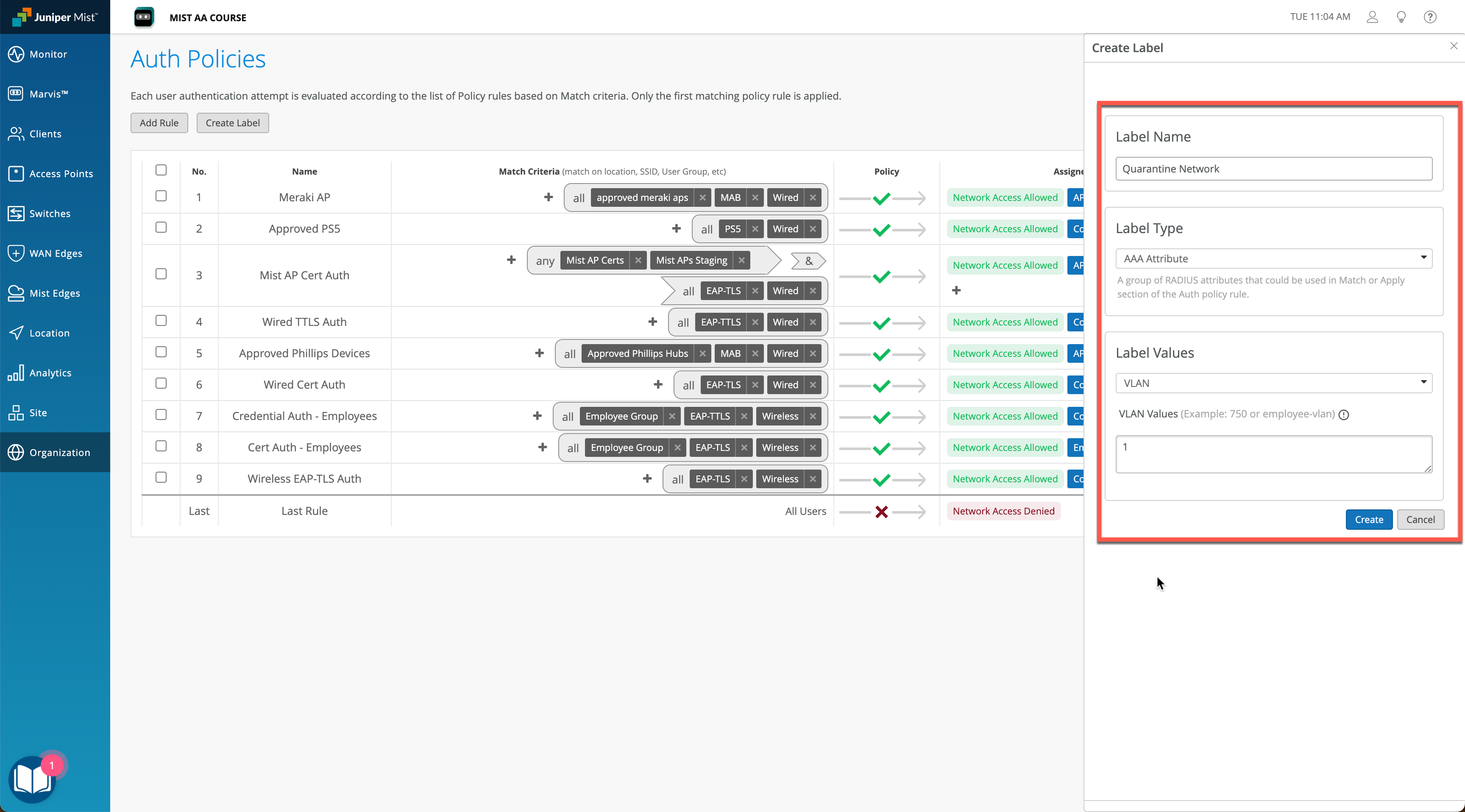
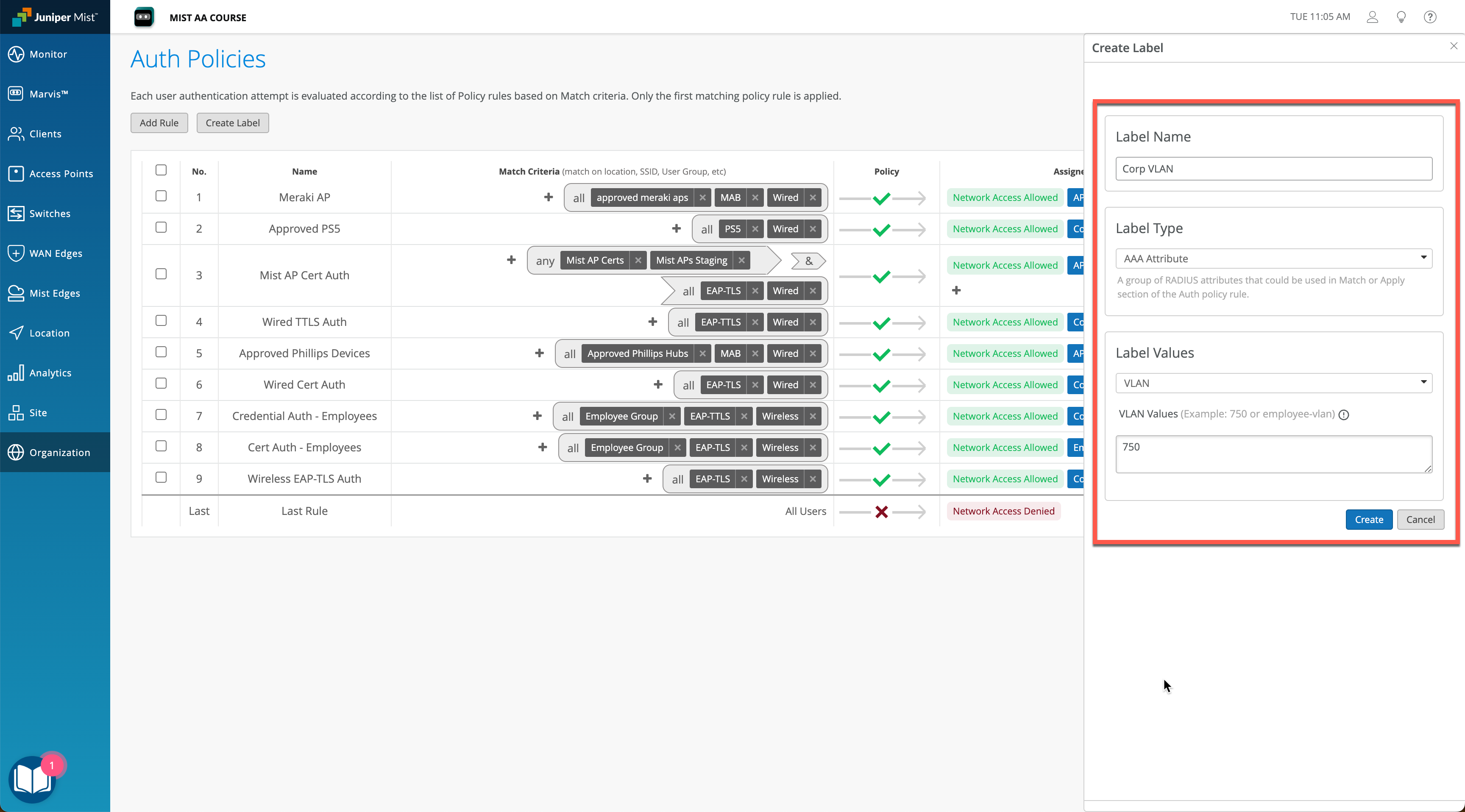
Secondly, create appropriate VLAN/Role labels as required for Quarantine and Unrestricted policies. In our example we will use Quarantine VLAN and Corp VLAN to differentiate.
Now, putting things together, lets create two Auth Policy rules for compliant and non-compliant devices respectively.
Verification
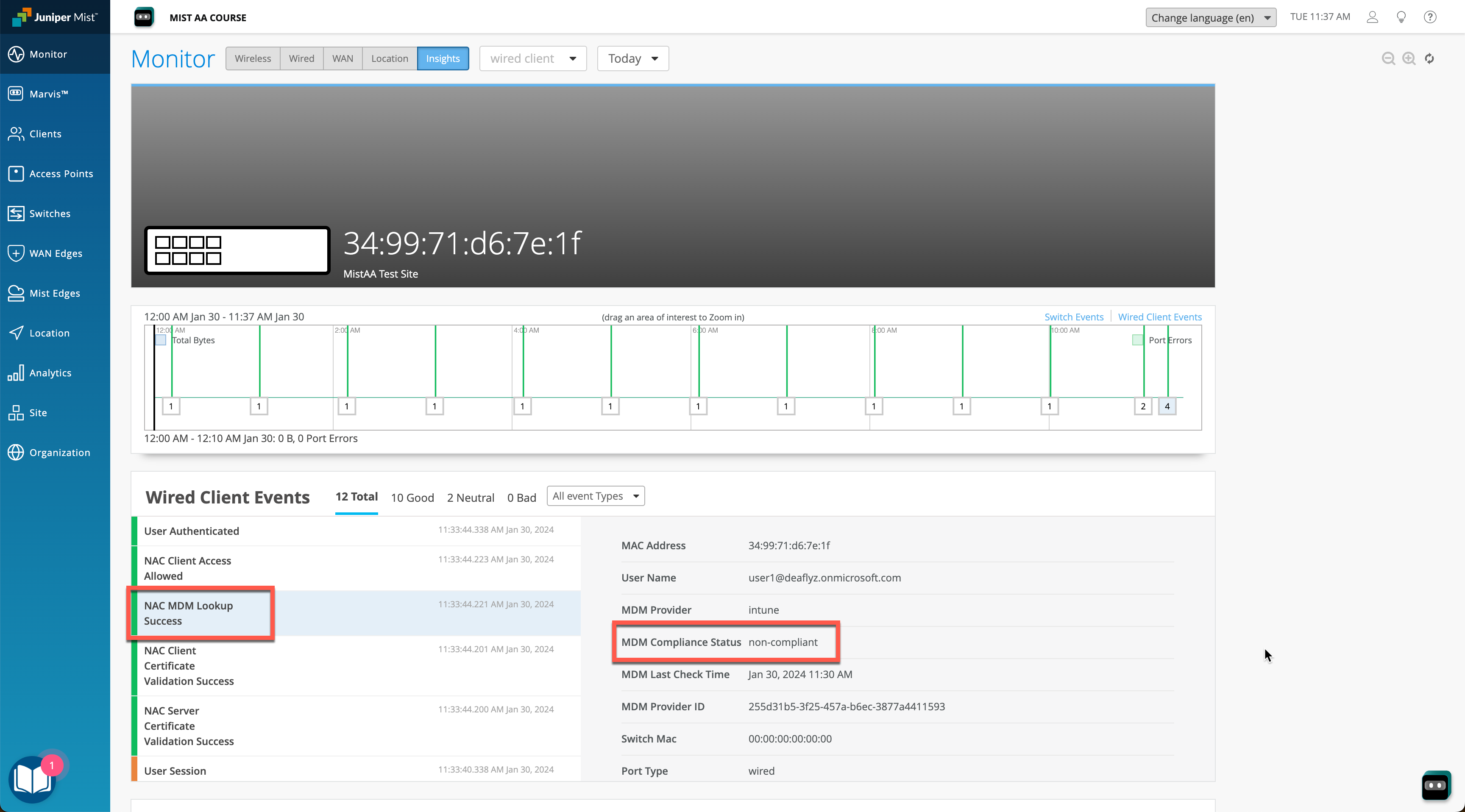
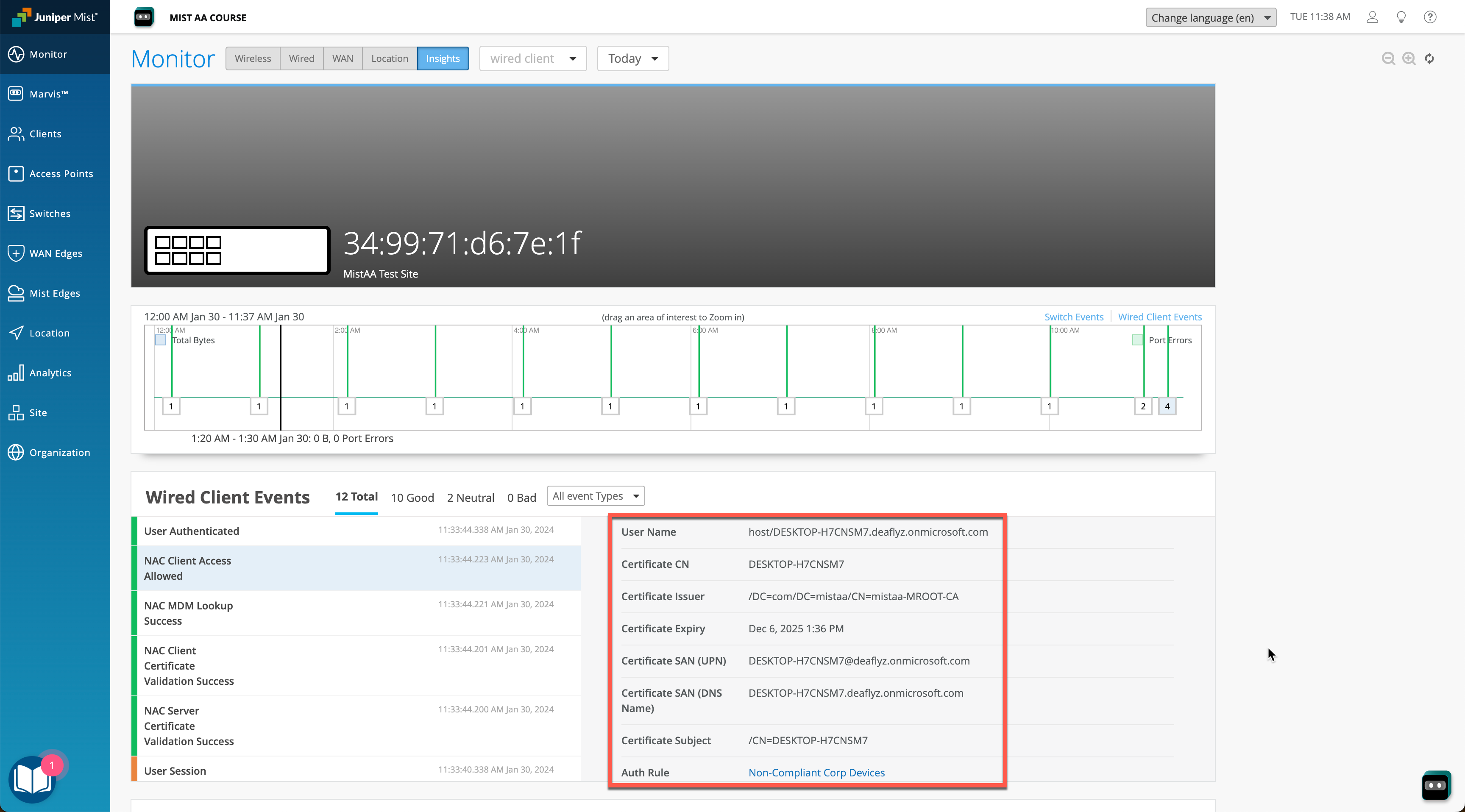
When a client is going through authentication/authorization process, Intune compliance state will be obtained and used in policy evaluation. We can verify the auth process either at the Wireless Client Insights (for wireless clients) or Wired Client Insights (for wired) or under Auth Policies > NAC Events view.
In our example we have a wired client that is performing machine authentication using EAP-TLS, and in this particular case Intune tells us that the device is not compliant, hence we move the client into a quarantine VLAN.