Simplified Operations
Client IP addresses in the webhook messages
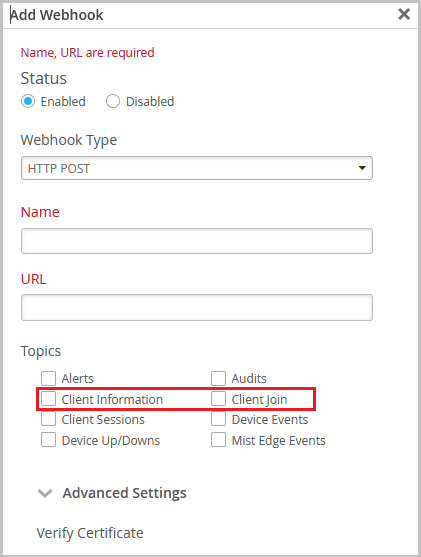
We have enhanced the Client Join webhook topic to include the IP addresses of the client devices that joined your network. We have also added a new Client Information topic to capture any changes in the clients’ IP addresses. You can enable these topics to receive the IP addresses of the clients the moment they join the network. This enhancement involves the following changes:
-
Update to the Client Join topic: We have included the client IP addresses (IPv4 and IPv6) in the Client Join webhook message, in addition to the other client information such as MAC address, RSSI, radio band, and connected AP. The IP address is included only if it is available when the webhook message is sent.
-
New Client Information topic: This is a new webhook topic, triggered when Mist detects a change in the IP address of a client. In the Client Information message, you can see the client MAC address along with the current IP address.
Both topics can be enabled in the webhook configurations at the Org (Organization > Settings) and the Site (Organization > Sites) settings page.
Filtered view of affected items on the Service Level Metrics page
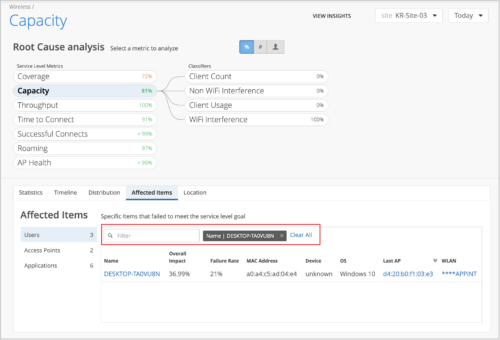
We have added a filter on the Affected Items tab of the Service Level Metrics page to help you view the relevant Affected items under each metric while you perform the root cause analysis of an issue.
Marvis
Troubleshoot your Zoom sessions with Shapley Feature Ranking
You can now better analyze and troubleshoot any bad zoom calls in your network with the help of Shapley Feature Ranking. This ranking helps you determine the average marginal contribution of each Shapley feature towards a negative user experience. The average marginal contribution is arrived at by factoring in all possible permutations of features. Here, features are network parameters that could include received signal strength indicator (RSSI), latency, jitter, and so on. The Shapley feature ranking is computed for every minute of bad audio or video that a user experiences during the Zoom call.
You can access the Shapley Feature Ranking from the Meeting Details table on the Clients Insights page.
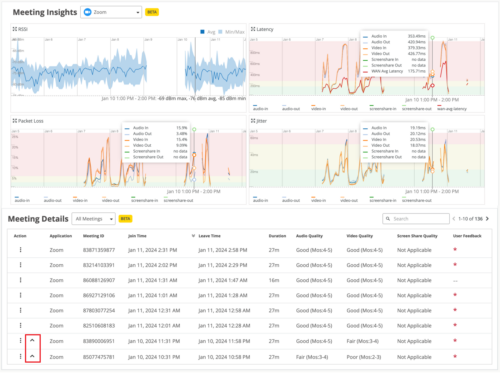
In the above sample image (Meeting Insights), the lowest two rows of the Meeting Details table are expandable. This means that each of those two rows represents a Zoom meeting that had a bad user experience reported and has a Shapley Feature Ranking associated with it. You can expand the rows by clicking the caret symbol (^) to access the Shapley Feature Ranking page.
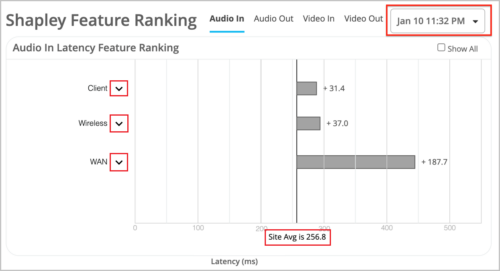
In the above example, the X axis of the graph shows the latency reported (in milliseconds). The Y axis shows the latency contributed by each feature (Client, Wireless and WAN) in addition to the site-average latency. You can further expand the Client, Wireless, and the WAN sections to view the additional feature set to understand which feature contributed to the maximum latency. For each bad user minute, the Shapley Feature Ranking view provides data under the Audio In, Audio Out, Video In, and Video Out headings. If there are multiple bad user experience minutes within a meeting, you can select the minute from the drop-down list on the upper right to view the feature ranking for the specific occurrence.
See Troubleshoot Zoom Sessions Using Shapley Feature Ranking for more information.
Access Assurance
Microsoft Intune integration with Access Assurance
You can integrate your Microsoft Intune account with Juniper Mist Access Assurance. Microsoft Intune is a cloud-based mobile device management (MDM) solution that helps you manage the mobile devices on your network and secure corporate data when the devices access on-premises resources. The Access Assurance solution makes access control decisions for the enrolled mobile devices based on the compliance state of the device as reported by Intune. If a device does not comply with the Intune compliance policies, the Access Assurance can move it into a quarantine VLAN or role for remediation. The Microsoft Intune integration involves the following steps:
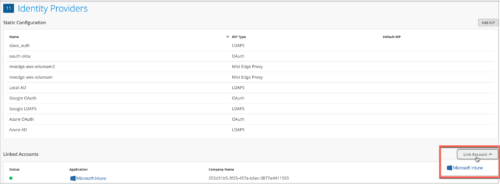
- Link your Microsoft Intune account with Mist Access Assurance solution. You can do this from the Identity Provider page (Organization > Identity Providers).
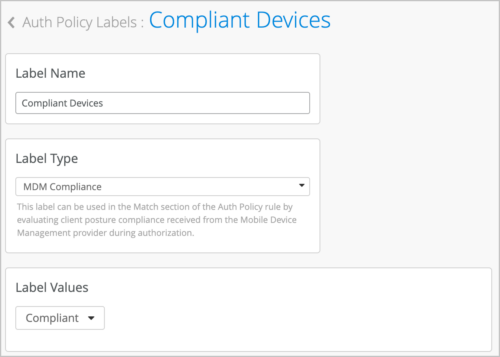
- Create an Auth Policy Label of the type MDM Compliance (Organization > Auth Policy Labels). You can choose to specify the following label values: Compliant, Non-Compliant, and Unknown.
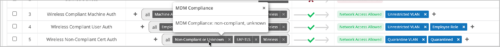
- Leverage the MDM compliance labels in an Auth Policy rule (Organization > Auth Policies) so that policy matching is done by evaluating the client compliance posture received from the MDM provider during authorization.
The MDM-specific events are displayed on the Client Events or NAC Events page.
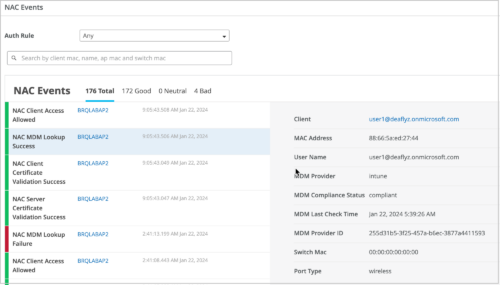
Hit count for NAC rules in Auth Policies (Juniper Mist Access Assurance)
We have added a new column named ‘Hit Count’ on the Auth Policies page (Organization > Auth Policies) to show the number of NAC events for each rule. You can filter the hit count information for the last 60 minutes, last 24 hours, last 7 days, today, yesterday, this week, or for a custom date or range.
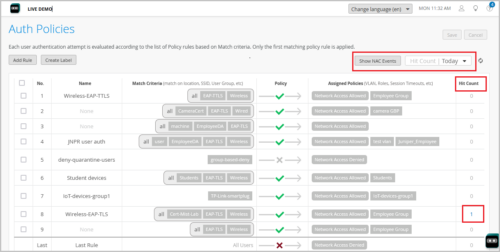
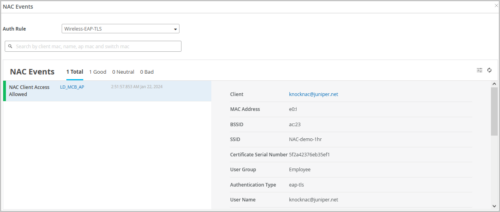
You can click the Show NAC Events button to go to the events page which lists all the NAC events. Click the hit count value of a particular NAC rule if you want to view the events for that particular rule, as shown below.
Wired Assurance
Support for overriding port configuration through bulk port edit
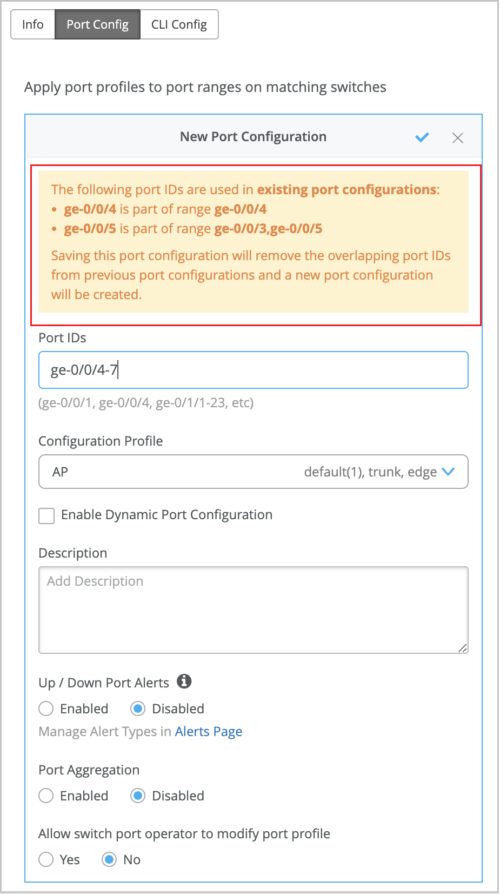
You can use the bulk port configuration option on the switch details page to override any existing port configuration on a switch. To do that, select the ports to be configured from the Front Panel on the switch details page, and click Modify Port Configuration. In case the selected ports are already part of an existing port range configuration, a warning message indicating the same is displayed. When you save the new configuration, it will replace the existing configuration for the selected ports. Previously, you had to manually remove any port configuration overlap before you carry out a bulk port edit.
Here is how a warning that indicates a port configuration overlap is displayed when you bulk edit ports:
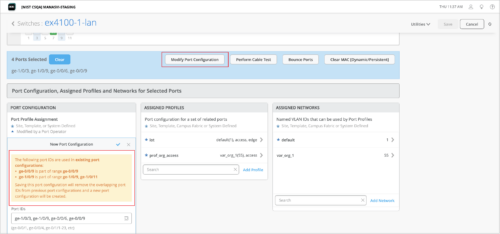
You can also see the port configuration overlap warning (if there is an overlap) when you try to edit the configuration from the Port Config tab of a switch template (organization or site level) or from the PORT CONFIGURATION tile on the switch details page. The following sample image shows the Port Config tab on the switch template:
Support for configuring IP settings and static route as site variables
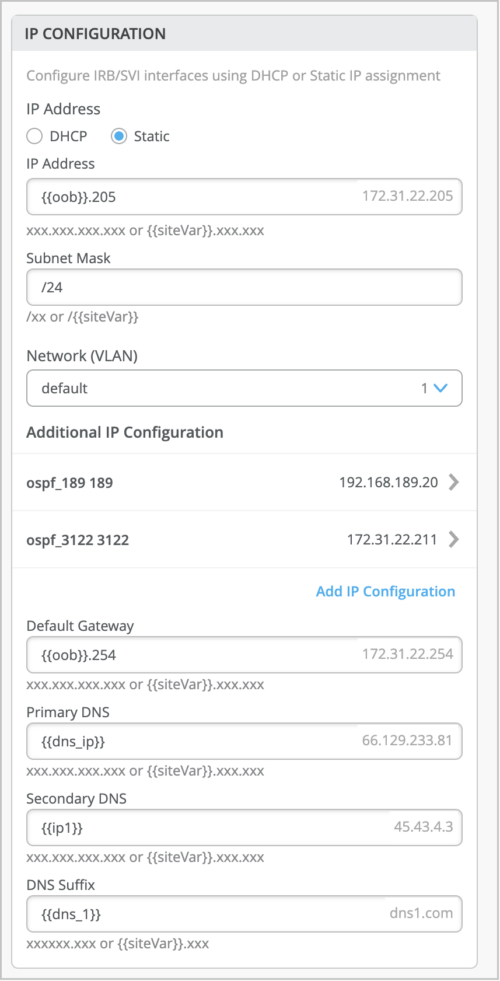
Mist supports configuration of static route and IP settings as site variables at the device level, site level, and organization level. Site variables help you address use cases that require you to configure a set of unique fields for different sites. Site variables provide a way to use tags to represent real values so that the value can vary according to the context where you use the variable. This means the same variable can configure different values in different sites.
Under IP Configuration, you can configure IP Address, Subnet Mask, Default Gateway, Primary DNS, Secondary DNS, and DNS Suffix as site variables.
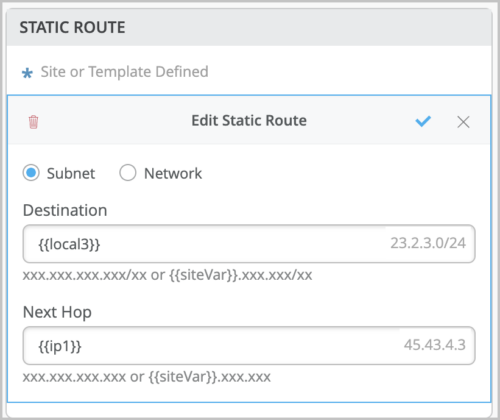
Similarly, in the static route configuration section, you can configure the Destination and Next Hop fields with site variables.
Site variables are now available for the following fields at the device level (switch details), site level (switch template), and organization level (switch template):
- DNS servers and DNS suffix
- NTP
- Radius servers
- Static route
- Networks (VLAN ID, subnet, or subnet mask)
- IP Configuration (including Additional IP configuration): Default Gateway, Primary DNS, Secondary DNS, and DNS Suffix.
- IP Configuration (OOB)
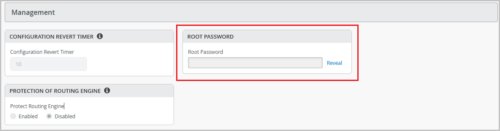
Updates to root password configuration
As a Super User, you can configure your Junos root password from the switch template (at the site or organization level) or from the switch details page. Previously, this configuration was available only on the site configuration page (Organization > Site Configuration). The root password you already defined on the Organization > Site Configuration page is now available on the site-level template (Site > Switch Configuration) and is inherited by the associated devices.
If you are not a Super User, you can only see the password (if available) as an encrypted text. The Root Password field is optional.
With this release, you can configure root password from the following pages (in addition to the site configuration page):
-
Organization-level switch templates (Organization > Switch Templates).
-
Site-level switch templates (Site > Switch Configuration).
-
Switch details page (Switches > Switch Name).
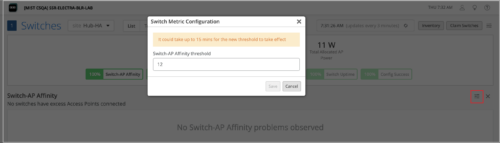
Option to configure AP threshold for the Switch-AP Affinity metric
You can configure a threshold value for the number of APs per switch to be considered in the Switch-AP Affinity metric calculation. The Switch-AP Affinity metric is one of the compliance parameters used to track the performance of switches. This metric shows the weighted percentage of the switches for which the number of APs connected exceeds the threshold configured. By default, the Switch-AP Affinity threshold is set to 12 APs per switch.
To configure the AP threshold, click the Switch-AP Affinity indicator, and then click the hamburger icon on the right of the Switch-AP Affinity section.
WAN Assurance
Dynamic packet capture support (SSR)
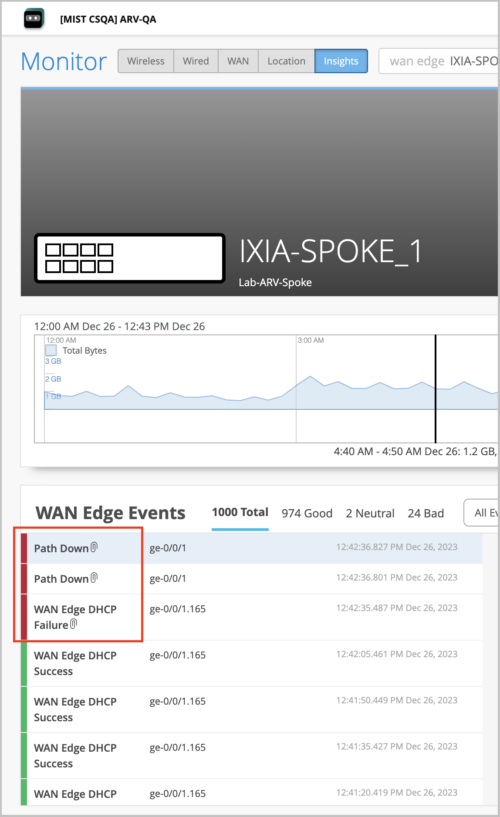
To improve your troubleshooting experience, Mist provides dynamic packet capture (dPCAP) support for SSR devices. Dynamic packet captures are automatically saved and available for you to download in the WAN Edge Events section on the WAN Edge Insights page. Events with a dynamic packet capture available are indicated by a paperclip icon next to the event name. To download the packet capture file, click that event and then click the Download Packet Capture button available in the Events Details section on the right.
Here are the events which can generate a dynamic packet capture for an SSR device:
-
Failure of the ARP request to next-hop gateway
-
DHCP address resolution failure
-
WAN Edge failure to establish BGP peering based on configuration
-
WAN Edge failure to establish SVR peering based on configuration
Support for switching local breakout paths when SLA thresholds are breached (SSR)
To improve your network monitoring experience with SSR devices, Mist now supports switching local breakout traffic from one path to another when the path does not meet the associated SLA requirements for the link latency, jitter, and loss parameters.
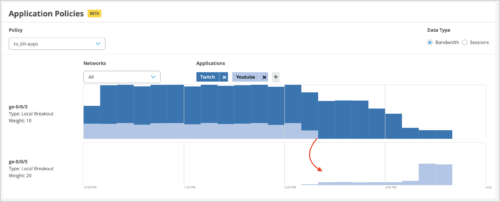
The SSR devices compare the SLA parameters (latency, jitter, and loss) for all the local breakout paths against the thresholds configured for these parameters for each application. Whenever a set threshold is breached (that is, a local breakout path fails to meet the associated SLA requirements), the traffic shifts to another path based on the traffic steering configuration. Any such shifts in traffic are displayed on the Application Routing Visibility graph on the Application Policy dashboard.
The following sample image shows a traffic shift from the ge-0/0/3 interface to the ge-0/0/5 interface because of an SLA threshold breach:
Configuration of this feature involves the following steps:
-
Configure the threshold values for jitter, latency, and loss in the Advanced Settings section on the Add Application screen (Organization > Applications > Add Applications). You must configure these parameters per application.
-
Configure the required traffic steering in the WAN Edges template associated with the site (Organization > WAN Edge Templates) or on the WAN Edge details page (WAN Edges > WAN Edges > WAN Edge Name).
-
Include the traffic steering configuration in the application policy associated with the site. You can do this from the WAN Edges template (Organization > WAN Edge Templates) or on the WAN Edge details page (WAN Edges > WAN Edges > WAN Edge Name).
This feature is already available for SVR paths.
Enhanced policy framework with an expanded application list
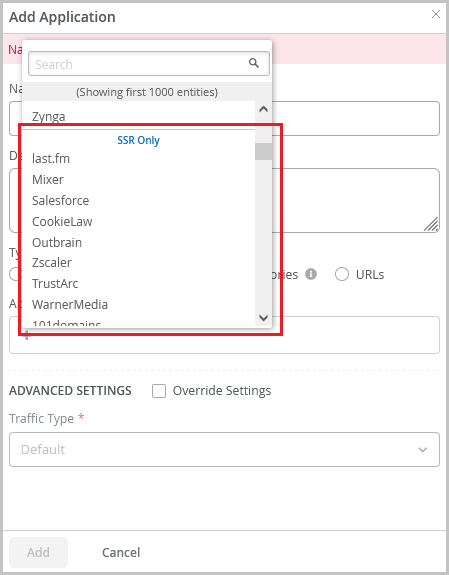
We have significantly expanded the list of applications in Mist cloud to include thousands of applications supported by the WAN edge devices. The application list now groups the applications under the following sections for easier selection:
- Applications
- SSR Only
- SRX Only
On the application creation screen (Organization > Applications > Add Applications), you can now view and select these applications and use them in Application Policies to block traffic or make traffic steering decisions.
Previously, Mist supported application traffic steering only for a set of curated applications, though it displayed all the learned applications on the Insights page.
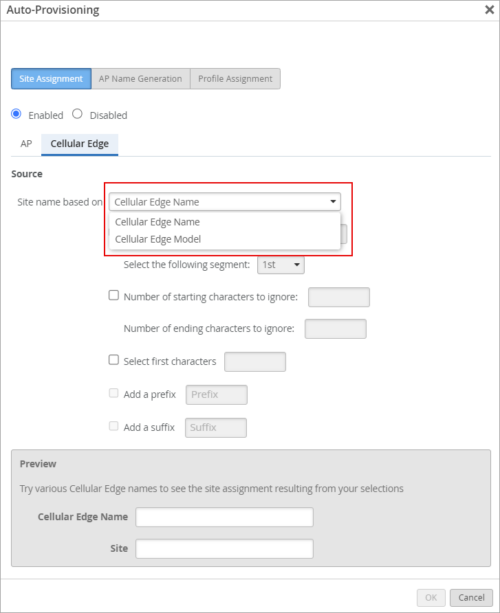
Automatic site assignment for Cellular Edge devices
Juniper Mist now supports automatic site assignment for Cellular Edge devices. This support is currently available only for Cradlepoint devices. This feature enables you to configure rules for Cradlepoint devices to be assigned with relevant sites automatically. You can configure the automatic site assignment settings from the Organization > Settings page. You can use one of the following methods:
- Name-based: Lets you configure rules to derive the site name based on the device name (Cellular Edge Name).
- Model-based: Lets you assign sites per device model (Cellular Edge Model).
When Mist detects a Cradlepoint device, it assigns the device with a site in accordance with the automatic site assignment rules configured. If automatic site assignment is not configured, Mist uses the LLDP information on the Cradlepoint device to identify the directly connected Juniper device in the same organization and assigns the Cradlepoint device with the same site that is assigned to the Juniper device. For the LLDP-based automatic site assignment to work, you must ensure that LLDP is enabled on both the Cradlepoint and the Juniper device. Automatic site assignment is applicable only to the devices connecting to the Juniper Mist dashboard for the first time.
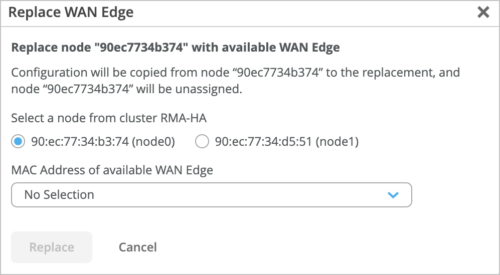
Support for replacing an SSR node in a high availability cluster
The Mist portal now supports replacing a faulty node with a new one in an SSR cluster. You can replace a node in an SSR cluster by using the Replace WAN Edge option on Utilities menu on the SSR cluster details page (WAN Edges > WAN Edges > WAN Edge Name).
On the Replace WAN Edge window, you can select the old faulty SSR node to be replaced and the new replacement node’s MAC address (from the MAC Address of available WAN Edge drop-down list). After you click Replace, Mist takes about 15 minutes to complete the replacement operation.
Before replacing the SSR node, you must:
-
Remove the cluster fabric cables from the node being replaced and connect it to the new replacement node.
-
Ensure that the new replacement node is of the same model as the node being replaced.
-
The new replacement node has a firmware version greater than 6.0.
-
If you are replacing a node with a new out of the box SSR node, ensure that you:
-
Claim the new node to the same site where the SSR cluster is present.
-
Upgrade the firmware of the node to a version above 6.0.
-
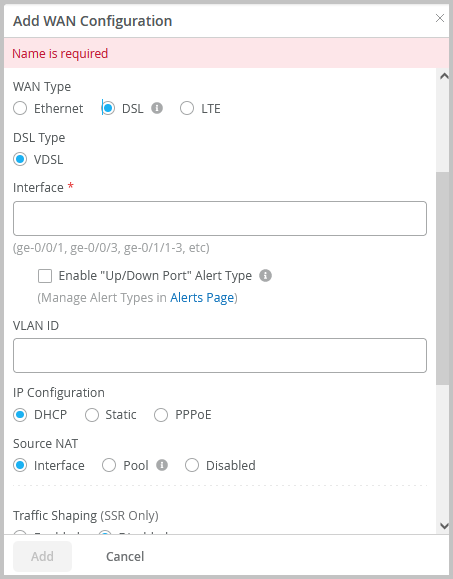
VDSL support for SRX Series devices
Mist now supports very-high-bit-rate digital subscriber line (VDSL) technology for SRX Series devices which have a DSL MPIM card installed. You can configure this from the WAN configuration section of the WAN Edge details page (WAN Edges > WAN Edges > WAN Edge Name) or WAN Edge Template (Organization > WAN Edge Templates). VDSL technology is part of the xDSL family of modem technologies, which provide faster data transmission over a single flat untwisted or twisted pair of copper wires.
Mist Edge
Mist Edge events on the Alerts page
The Monitor > Alerts page now displays the Mist Edge events. It displays critical, warning, or information messages based on the events.
-
Critical messages: Displayed for events such as disconnection of Mist Edge from cloud, Mist Edge service crash, and disconnection of all tunnels.
-
Warning messages: Displayed for events such as Mist Edge service failures, and detection of high CPU, memory, and disk usage.
-
Information messages: Displayed for events such as formation of tunnels, completion of Mist Edge connection to the cloud, and detection of inactive VLANs on the tunnel port.
Support for autopopulating tunnel IP addresses in Mist Edge cluster
The Mist Edge Cluster creation page autopopulates the Hostnames/IPs field in the Tunnel Termination Services section with the Tunnel IP address configured in the Mist Edge selected. You no longer need to manually enter the unique Tunnel Termination Services IP addresses for the Mist Edges included in the cluster. The autopopulate feature prevents any entry of incorrect Tunnel IP addresses. When you remove a Mist Edge from a Cluster, the associated Tunnel IP address gets removed.
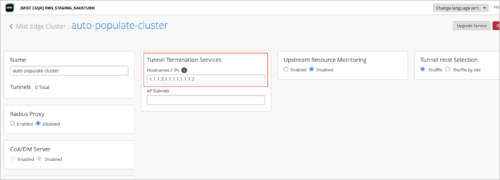
In the case of a remote Mist Teleworker, you need to manually enter the external IP of the Mist Edge.
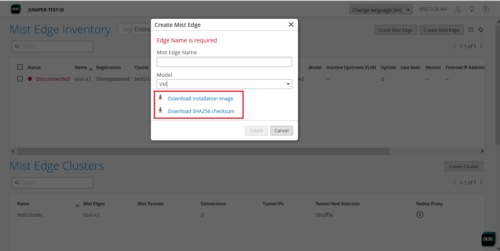
Option to download Mist Edge VM ISO image
We have made the virtual Mist Edge deployment easier by providing a download link for the Mist Edge Virtual Machine (VM) ISO image on the Create Mist Edge page. Previously, you had to search for the download link in the Mist Edge documentation. Using the virtual Mist Edge solution, you can run Juniper Mist Edge as a hypervisor on VMware to implement a virtual Mist Edge architecture using a Juniper Mist Edge appliance as virtual machine (VM). For added security, we also provide an option to download an SHA-256 checksum which helps you ensure that the copy of the VM image downloaded is not tampered with.
Support for replacing Mist Edge
We have introduced an option to replace a Mist Edge in your network with a new Mist Edge. The new option, Replace Mist Edge, is available on the Utilities menu on the Mist Edge details page.
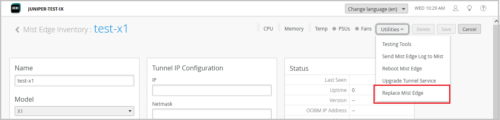
Clicking the Replace Mist Edge option takes you to the Replace Mist Edge page from where you can select the new replacement Mist Edge.
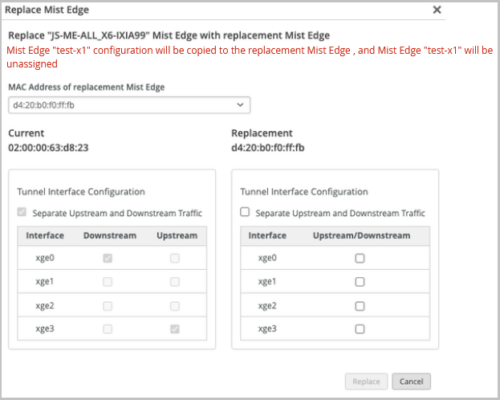
Before initiating the replacement process, ensure that the new replacement Mist Edge is:
-
Claimed but is not assigned to any site.
- Present in the inventory.
Configurations on the old Mist Edge that is being replaced are copied to the new replacement Mist Edge. Also, when the replacement activity is completed, the Mist Edge that is replaced is unassigned from its site. Though the port configuration is copied to the new replacement Mist Edge, you can modify the arm-mode. In the new Mist Edge, you can choose to use separate upstream and downstream ports (dual-arm mode) or a single port to handle both upstream and downstream traffic (single-arm mode).
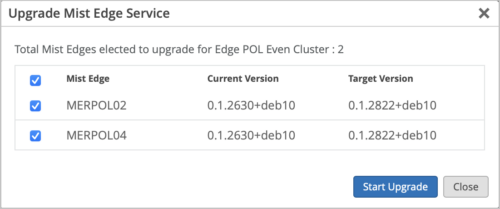
Simplified upgrade workflow for the Mist Edge services
While upgrading the Mist Edge service pack, you no longer need to select a target version. Mist automatically identifies the latest recommended target version for you to initiate the upgrade. This feature prevents you from accidentally selecting a version which is not recommended.
You can access the Mist Edge service upgrade window from the Mist Edge details page (from the Utilities menu) or from the Mist Edge Cluster details page. The upgrade window displays the Mist Edge Name, the current version, and the target version. You just need to select the device row and click Start Upgrade. If you are upgrading a Mist Edge cluster, you might see multiple device rows (one for each Mist Edge device in the cluster) on the upgrade window. You can choose to upgrade one or more devices in the cluster. For a Mist Edge upgrade, you will always see a single device row for selection.
The Mist Edge does not recommend any target version if the Mist Edge selected for upgrade is already running the latest service pack.