On the 128T SSR this new feature, which is enabled when the Intent is added in Policies. There is nothing a User needs to do for this feature, only activation in an Application Policies on the Spoke is needed.
Intrusion detection is the process of monitoring the events occurring in your network and analyzing them for signs of possible incidents, violations, or imminent threats to your security policies. Intrusion prevention is the process of performing intrusion detection and then stopping the detected incidents. These security measures are available as intrusion detection systems (IDS) and intrusion prevention systems (IPS), which become part of your network to detect and stop potential incidents.
Note
For technical reasons the IDP Feature on SSR Devices is limited to only being executed on Spokes. Hubs should leverage additional Juniper SRX Devices for this function.
You can apply a profile (Alert, Standard, Strict) to an access-policy. Each profile has an associated traffic action. These actions define how the ruleset is handled on each service or access policy. Actions are not user-configurable. The following IDP profiles apply the policy enforcement.
- Alert – When the IDP engine detects malicious traffic on the network, only an alert is generated; no additional measures are taken by the system to prevent the attack. The IDP signature and rules are the same as the Standard profile. Alerts are typically only for low severity attacks, or when the administrator explicitly configures the alert action for a service and tenant.
- Standard – The Standard profile is the default and represents the set of IDP signatures and rules recommended by Juniper. Each type and severity of attack has a Juniper-defined, non-configurable action that is enforced when an attack is detected. These actions include:
- Close the client and server TCP connection.
- Drop current and all subsequent packets.
- Alert only, no additional action taken.
- Strict – The Strict profile contains a similar set of IDP signatures and rules as the Standard profile. However, when an attack is detected the actions are more likely to actively block any malicious traffic or other attacks detected in the network.
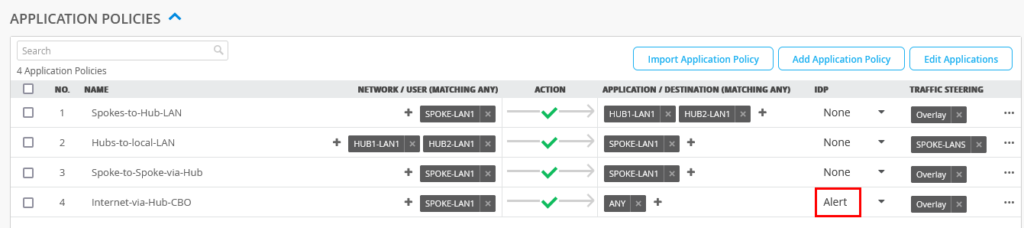
Go to the Spoke-Template via Organization -> WAN Edge Templates -> Select=”Spokes” and set on the last Application Policy “Internet-via-Hub-CBO” the IDP=Alert and then save your changes so that they get applied on all Spokes.
Note: The Policy Action must be PERMIT as the IDP setting will override the DENY statement
On all Spokes where this Traffic is NOT steered to a local LAN or WAN interface (for LBO) we need to add the IDP Service on the Hub. In our example we steer this Traffic to the Overlay VPN so we must also let the remote site (the Hub) know about this change.
Below you see the change of the forwarding Path on the Spoke the activation of this feature will cause. The side towards the LAN-Interface will stay as it is. Toward the WAN side a new automatic Service called: ANY-idp* and Tenant called: SPOKE-LAN1-idp*. Also, you see that there are basically two sessions seen inside the system. It’s important on the other side (the Hub) it expects a matching Tenant name “SPOKE-LAN1-idp*” and no longer “SPOKE-LAN1” that was used in our other documentation regarding Application Policies.
Note: The information below is taken from the SSR PCLI that is only accessible locally on the device.
show service ============================================== ==================== ====================================================== ================= =========================== ======= ========== ============== ============== Service Prefixes Transport Tenant Allowed Service-Policy State Sessions Tx Bandwidth Rx Bandwidth ============================================== ==================== ====================================================== ================= =========================== ======= ========== ============== ============== ANY 0.0.0.0/0 - SPOKE-LAN1 ANY-sp . . ANY-idp* 0.0.0.0/0 - SPOKE-LAN1-idp* ANY-sp Up 0 0 bps 0 bps . . show sessions ====================================== ===== =============================== ================= ======================= ======================= ====== ======= ================= ========== ================= =========== =============== ========== =================== ========= ================= Session Id Dir Service Tenant Dev Name Intf Name VLAN Proto Src IP Src Port Dest IP Dest Port NAT IP NAT Port Payload Encrypted Timeout Uptime ====================================== ===== =============================== ================= ======================= ======================= ====== ======= ================= ========== ================= =========== =============== ========== =================== ========= ================= 3e3bc1d9-3e6f-455b-87f8-902d459eec5e fwd ANY SPOKE-LAN1 ge-0-3 ge-0-3_1099 1099 ICMP 10.99.99.99 10 9.9.9.9 10 0.0.0.0 0 True 4 0 days 0:59:25 3e3bc1d9-3e6f-455b-87f8-902d459eec5e rev ANY SPOKE-LAN1 idp-in idp-in 0 ICMP 9.9.9.9 10 10.99.99.99 10 0.0.0.0 0 True 0 0 days 0:59:25 2d1251ac-1e3a-42b7-8d5b-83403be09677 fwd ANY-idp* SPOKE-LAN1-idp* idp-out idp-out 0 ICMP 10.99.99.99 10 9.9.9.9 10 0.0.0.0 0 True 4 0 days 0:59:25 2d1251ac-1e3a-42b7-8d5b-83403be09677 rev ANY-idp* SPOKE-LAN1-idp* ge-0-0 ge-0-0 0 UDP 192.168.129.191 16405 192.168.173.114 16414 0.0.0.0 0 True 0 0 days 0:59:25 . .
To archive matching a Tenant-Name on the Hub side being use for this example we go to the Hub Profile via Organization -> Hub Profiles -> Select=”hub1” and set on the Application Policies “Spokes-to-Hub-LAN” and “Spokes-Traffic-CBO-on-Hub” the IDP=Standard and then save your changes. This will help to sync the Tenant-Names used on both sides so that they can communicate with each other again.
Warning
When you activate this feature for the first time on a Spoke plan to do it in a maintenance window. The start of the IDP Engine and inclusion into the path from LAN to WAN (aka service-chaining) will take a few minutes and may interrupt ongoing communications.
To see the effects of the IDP based security scanner one must launch some attacks at least for testing. Security / Penetration Testing Linux distributions such as Kali-Linux give you a wide variety of tools at hand for this task.
In the below we leverage the desktop1 VM of the Lab to install a simple security scanner for webservers called “nikto” and let it run against the unhardened Apache Tomcat webserver local to this Lab. We’ve done this for simplicity of the setup as we only need this additional tool installed and a local webserver where we can send plain/unencrypted HTTP-Requests for the IDP to inspect. Below is an example of the process where we install the Tool, check the presence of the HTTP-Server and then forge the attacks.
virsh console desktop1
apt-get update
apt-get install -y nikto
# Using your individual Lab-Access-IP we test if the labinternal
# Apache Tomcat Server of the Apache guacamole container is avail
wget http://172.16.77.155:8080
–2022-09-16 15:47:32– http://172.16.77.155:8080/
Connecting to 172.16.77.155:8080… connected.
HTTP request sent, awaiting response… 200
Length: unspecified [text/html]
Saving to: ‘index.html’
index.html [ <=> ] 10.92K –.-KB/s in 0s
2022-09-16 15:47:32 (85.3 MB/s) – ‘index.html’ saved [11184]
# Now start our security scanner for the first time
nikto -h http://172.16.77.155:8080
– Nikto v2.1.5
—————————————————————————
+ Target IP: 172.16.77.155
+ Target Hostname: 172.16.77.155
+ Target Port: 8080
+ Start Time: 2022-09-16 15:48:22 (GMT0)
—————————————————————————
+ Server: No banner retrieved
+ The anti-clickjacking X-Frame-Options header is not present.
+ No CGI Directories found (use ‘-C all’ to force check all possible dirs)
+ Server leaks inodes via ETags, header found with file /favicon.ico, fields: 0xW/21630 0x1556961512000
+ OSVDB-39272: favicon.ico file identifies this server as: Apache Tomcat
+ Allowed HTTP Methods: GET, HEAD, POST, PUT, DELETE, OPTIONS
+ OSVDB-397: HTTP method (‘Allow’ Header): ‘PUT’ method could allow clients to save files on the web server.
+ OSVDB-5646: HTTP method (‘Allow’ Header): ‘DELETE’ may allow clients to remove files on the web server.
+ /examples/servlets/index.html: Apache Tomcat default JSP pages present.
+ Cookie JSESSIONID created without the httponly flag
+ OSVDB-3720: /examples/jsp/snp/snoop.jsp: Displays information about page retrievals, including other users.
+ OSVDB-3233: /manager/manager-howto.html: Tomcat documentation found.
+ /manager/html: Default Tomcat Manager interface found
+ 6544 items checked: 1 error(s) and 10 item(s) reported on remote host
+ End Time: 2022-09-16 15:50:03 (GMT0) (101 seconds)
—————————————————————————
+ 1 host(s) tested
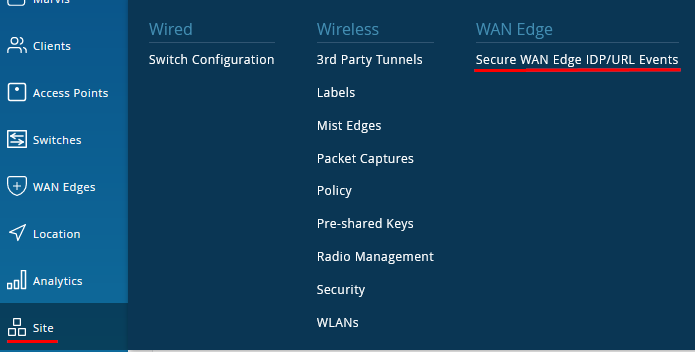
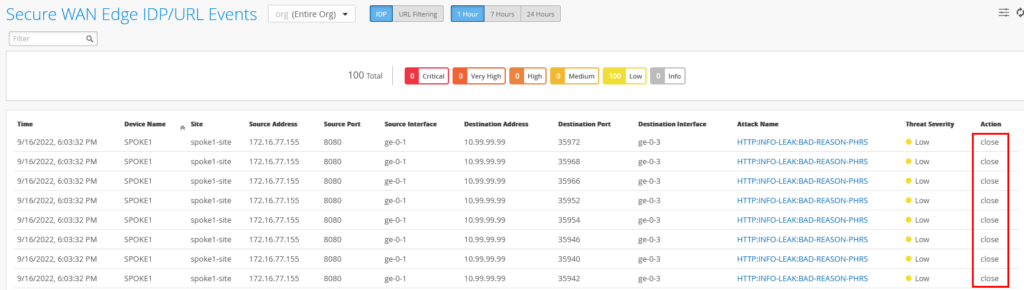
After there is enough generated events, we can inspect them. Now go to Site -> Secure WAN Edge IDP/URL Events
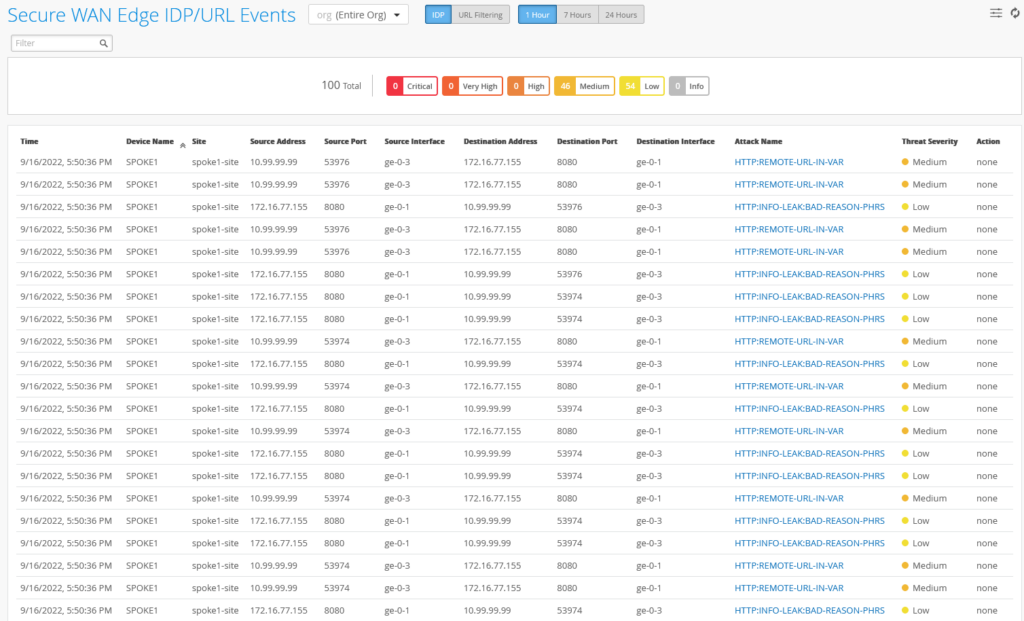
For the 128T SSR the detected events should look like this.
So far, we have only used the passive logging of those Events and did not stop/mitigate them. We have now become more aggressive and will start stopping those events. With the ‘strict’ Policy the IDP Engine tries to close TCP-Connections of ongoing Attacks it finds.
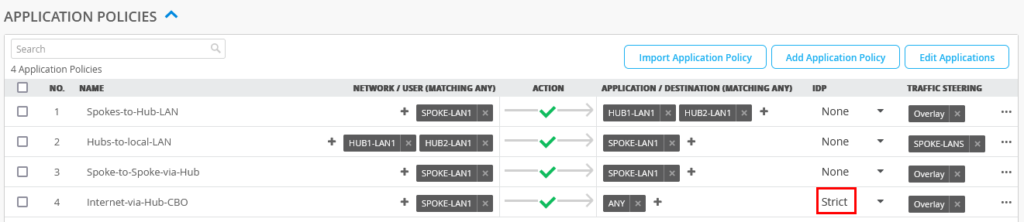
Change the Spoke Template and wherever you had formally configured IDP=Alert change it to now IDP=Strict as seen below for the 128T SSR.
Run the security scanner a second time and you will notice it will take longer to run, has way more errors and detects less items.
nikto -h http://172.16.77.155:8080
– Nikto v2.1.5
—————————————————————————
+ Target IP: 172.16.77.155
+ Target Hostname: 172.16.77.155
+ Target Port: 8080
+ Start Time: 2022-09-16 16:01:51 (GMT0)
—————————————————————————
+ Server: No banner retrieved
+ The anti-clickjacking X-Frame-Options header is not present.
+ No CGI Directories found (use ‘-C all’ to force check all possible dirs)
+ Server leaks inodes via ETags, header found with file /favicon.ico, fields: 0xW/21630 0x1556961512000
+ OSVDB-39272: favicon.ico file identifies this server as: Apache Tomcat
+ Allowed HTTP Methods: GET, HEAD, POST, PUT, DELETE, OPTIONS
+ OSVDB-397: HTTP method (‘Allow’ Header): ‘PUT’ method could allow clients to save files on the web server.
+ OSVDB-5646: HTTP method (‘Allow’ Header): ‘DELETE’ may allow clients to remove files on the web server.
+ /examples/servlets/index.html: Apache Tomcat default JSP pages present.
+ 6544 items checked: 5657 error(s) and 6 item(s) reported on remote host
+ End Time: 2022-09-16 16:05:27 (GMT0) (216 seconds)
—————————————————————————
+ 1 host(s) tested
Back on the Events overview you will now notice that the Action on some events was to close the session to mitigate it.
Some other mitigated events.