Simplified Operations
New cloud instance for US central region
We have introduced a new Mist cloud instance, named Global 05, for the US central region. This cloud instance will be visible on the cloud selection pane on the Mist login page. The new cloud instance provides all services except WAN Assurance for SSR, which will soon be available on this cloud. For additional information on Juniper Mist clouds, see Juniper Mist Firewall Ports and IP Addresses for Firewall Configuration.
View webhook delivery status
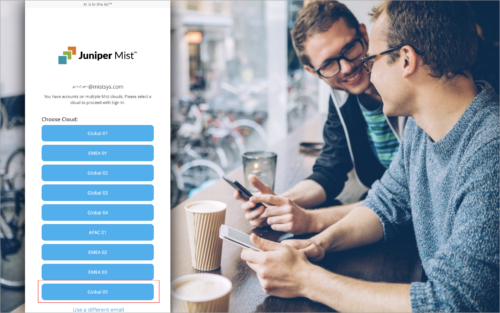
You can view the delivery status of webhook events data on the Webhooks tile of the Organization > Settings page (for organization-level configuration) or the Organization > Site Configuration page (for site-level configuration).
To view the status, click the View hyperlink in the Deliveries column on the Webhook tile, and you will be taken to the Webhook Deliveries page. This page displays webhook delivery status (Success or Failure) along with status code and other details. For each failed delivery, the page displays an error message containing additional insights into the failure.
Currently, only the following webhook topics support this feature: Alerts, Audits, Device Up/Down and Ping. The status information is available for the webhook deliveries reported during the last 61 days.
Marvis
New Wireless Marvis Action: ISP Offline
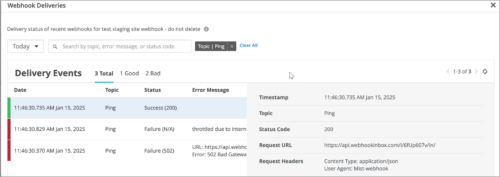
We have added a new Marvis Action, named ISP Offline, to Mist. This action detects access points (APs) that are offline because of ISP-related issues, such as ISP regional outages, routing issues, DNS issues, or issues caused by incorrect network settings. Marvis can determine whether the issue is limited to APs in a specific site or spread across multiple sites. It can also pinpoint the ISPs through which the impacted APs were connected, making the troubleshooting process easier.
If you see an ISP Offline action, here are some of the steps that you can take:
- Check the ISP’s portal for any outage reported.
- Check the router or modem configuration for any changes.
- Contact the ISP support team.
Download Marvis client
You can download Marvis client app from the Mist portal.
Marvis client lets you view your network from clients’ perspective. You can view detailed data and telemetry about how a client experiences the wireless connection, including insight into client roaming behaviors. The Marvis client recognizes connection types (cellular or wireless) and the corresponding signal strength. Marvis Client is available through a per-client subscription model (SKU: S-VNACLIENT).
You can download the Marvis client installer from the Organization > Mobile SDK > Marvis Client page. The download page lists the Windows, macOS, and Android versions of the app.
Wireless Assurance
Wi-Fi 7 support
You can enable or disable Wi-Fi 7 per WLAN from the WLAN configuration page. This option applies to Access Points that support Wi-Fi 7 and has no impact on APs that do not support Wi-Fi 7.
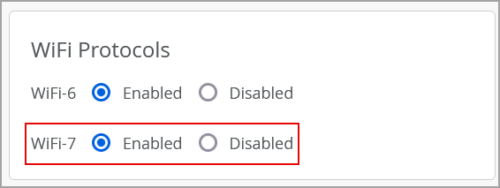
Wi-Fi 7, or the IEEE 802.11be Extremely High Throughput (EHT) standard, introduces new features and delivers several improvements over Wi-Fi 6 and Wi-Fi 6E. To leverage the benefits of Wi-Fi 7, both the AP and the connected client will need to support 802.11be.
For more information see Wi-Fi 7 (802.11be) Technology.
Automatically disable WLANs in failure scenarios
Introducing options to control WLAN availability based on AP connectivity status and tunnel failovers.
- Support to disable WLANs when the AP has no IP address or no default gateway, or on tunneled WLANs when the Mist Edge tunnel is down. This is meant to prevent dead-ending of clients when the AP doesn’t have full network connectivity, or has lost connection to Mist Edge.
- Support to reconnect clients upon Mist Edge failover when the Mist Edge cluster changes. This will be useful to gracefully disconnect the clients if the same IP subnet is not used across Mist Edge clusters.
These are per-WLAN configurations. To disable a WLAN when the AP’s default gateway is unreachable, such as when the AP has no IP address or no default gateway, select the Disable WLAN when AP Gateway is unreachable checkbox in the WLAN Status section on the WLAN configuration page.
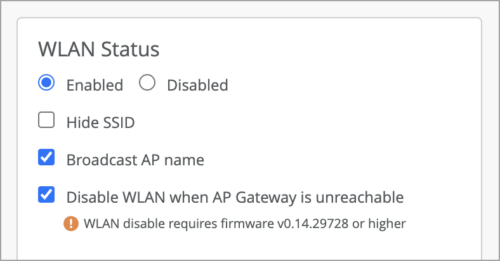
To disable the WLAN when the Mist Edge tunnel is down, check that option in the Custom Forwarding section on the WLAN configuration page. Similarly, to force clients to reconnect when the AP’s Mist Edge tunnel fails over to a Mist Edge in a different Mist Edge cluster, select the corresponding checkbox.
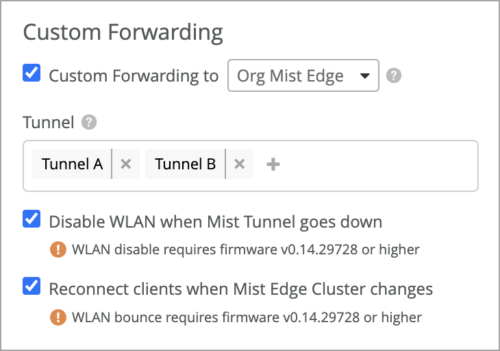
These features require the AP firmware version 0.14.29728 or newer.
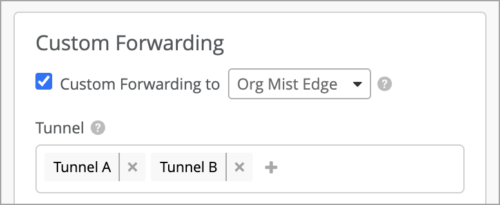
Add multiple Mist tunnels to WLANs
A single WLAN can now forward to multiple Mist Edge tunnels, as well as local breakout. Within a WLAN you can decide the forwarding behavior by VLAN. The intended use for the per VLAN forwarding control is to enable extremely high scalability in large environments since the AP can forward to different Mist Edge clusters. Another use is SSID consolidation with flexible forwarding.
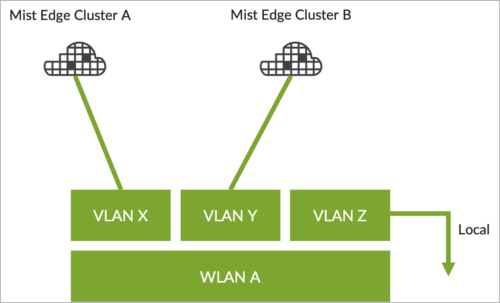
You can select multiple tunnels when you set custom forwarding to Org Mist Edge (previously called ‘Mist’) from the WLAN configuration page. You must ensure that a VLAN is not duplicated on multiple tunnels. To select multiple tunnels for custom forwarding, click the + button under the tunnel field to add one or multiple tunnels.
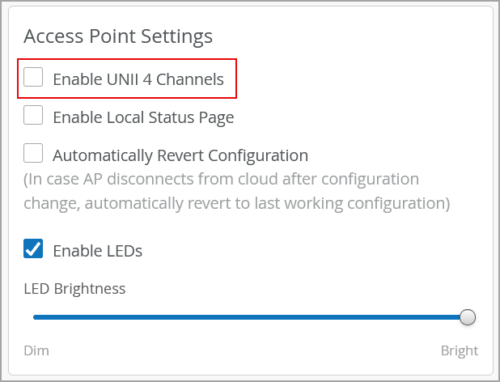
Enable or disable UNII 4 channels
The AP47 adds support for UNII-4 channels in the United States. Those are 5 GHz channels 169, 173, and 177. Due to mixed levels of client support, we have elected to disable UNII-4 channels by default. At the time of writing, many Windows and Android devices support UNII-4 channels, but the Apple ecosystem does not support these channels. Mist provides a site configuration option to enable UNII-4 per site, similar to the option we used to have with channel 144 until channel 144 client support improved. When UNII-4 channels are enabled, RRM will automatically allow these channels to be used for automatic channel selection on AP models that support UNII-4 channels. You don’t have to select channels manually in RF templates or device profiles.
You can enable or disable the UNII 4 channels from the Access Point Settings section on the site configuration page (Organization > Site Configuration).
If you enable UNII 4 channels, they will be displayed and configurable on the AP configuration page, device profile, RF templates, and RRM site settings in Mist. If you disable UNII 4 channels, they will not be displayed or configurable on Mist.
AP autoplacement is now generally available
We have made the access point autoplacement feature on Mist generally available. With the autoplacement feature, Juniper Mist can place the access point (AP) X,Y coordinates on a floorplan automatically. This feature saves time and makes for an easier deployment.
Note: You should only attempt autoplacement during a maintenance window. The amount of downtime you need to schedule depends on how many APs you have on the floorplan.
Autoplacement is supported on Wi-Fi 6 APs and newer. The minimum required firmware version for autoplacement is 14.28310.
For more information, visit Autoplacement: Position New Access Points.
Auto-provisioning enhancements for APs
We have added the Apply to Model parameter to the following AP auto-provisioning workflows:
- Site Assignment workflow: You can use AP Model as a parameter in determining the site to which an AP should be assigned. This parameter is available when you select LLDP System Name or DNS Suffix as the source for deriving the site from. This option is already available for the source AP Name.

- Profile Assignment workflow: You can use AP Model as a parameter in determining the device profile to which an AP should be assigned. This parameter is available when you select AP Name, LLDP System Name, or DNS Suffix as the source for deriving the device profile from.
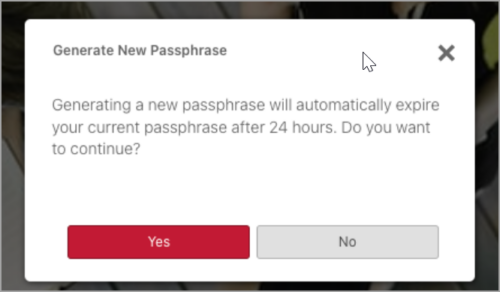
Update to passphrase generation workflow
In the PSK portal, when you click the Generate New Passphrase button, you will get a confirmation window with a message indicating that generating a new passphrase causes your current passphrase to expire after 24 hours. On the confirmation window, you need to click Yes to proceed. Previously, clicking the Generate New Passphrase button used to generate the passphrase without a confirmatory message.
Wired Assurance
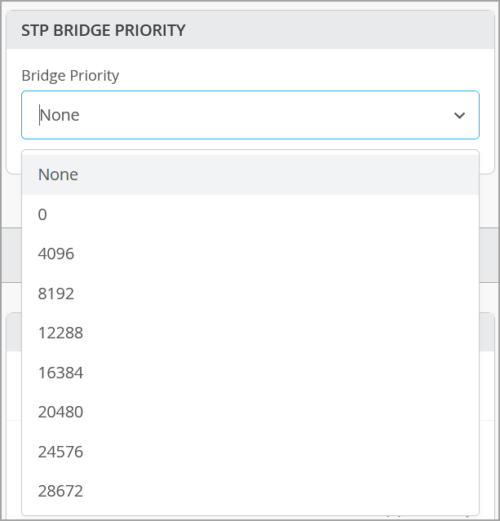
Configure bridge priority at switch level
Mist provides an option to configure bridge priority at the switch level. The bridge priority value along with the device MAC address forms the bridge ID which determines the bridge to be elected as the root bridge in a Spanning Tree Protocol (STP) topology. The priority value is useful when two bridges have the same path cost to the root bridge. If you do not set the bridge priority (or select the value ‘none’), the default value (32,768) is configured. The bridge priority can be set only in increments of 4096 (between 0 and 61,440). You can configure bridge priority from the STP Bridge Priority tile in the Management section of the switch details page.
The priority value set from the Additional CLI section takes precedence over the value set from the STP Bridge Priority section.
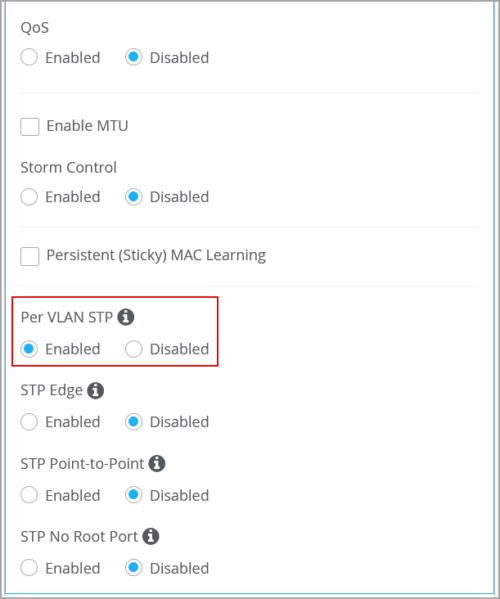
STP configuration per VLAN
You can configure a switch with VLAN Spanning Tree Protocol (VSTP) or per-VLAN Spanning Tree. This configuration is available in port profiles in the organization and site templates and on the switch details page. VSTP helps in preventing loops in Layer 2 networks on a per-VLAN basis. One Spanning Tree per VLAN enables fine grain load balancing. We recommend enabling this feature for other vendor’s devices (for example, Cisco) that operate per-VLAN spanning tree by default. When VSTP is enabled on a port, RSTP is automatically disabled on that port.
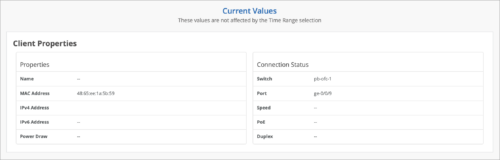
Historical connection data for wired clients
Mist can now retrieve and display the client properties and connection status data for the wired clients that are disconnected from the switch. This information, displayed in the Client Properties section on the clients Insights page, includes the client MAC address, switch name, and the switch port to which the client was previously connected. This enhancement allows you to access historical connection data, helping in troubleshooting and network management even when clients are not connected to the switch. Previously, the client properties and connection status data were available for clients only when they were connected to the switch.
To view the client properties and connection status data, navigate to the Insights page (Monitor > Service Levels > Insights) and then select the wired client using the scope selector on the Insights page. Alternatively, use Marvis Conversational Assistant to search for the client’s MAC address and then click the result to open the client Insights page.
Access Port Security classifier under Successful Connect SLE
We have added a new classifier, named Access Port Security, to the Successful Connect SLE for switches. This classifier helps you identify client connection failures caused by access port security issues. This classifier groups the reasons for connection failures into the following sub-classifiers:
- BPDU-Guard: Detects clients that are unable to connect because the port is set as STP Edge port (via port profile), and the clients are sending BPDUs.
- MAC Limit: Detects connection failures reported when a client exceeds the MAC limit configured on the switch port.
- Dynamic ARP Inspection: Identifies clients that encounter ARP failure. An ARP failure occurs when a switch drops ARP requests because the clients that are sending these requests are not in the DHCP snooping table.
- Rogue DHCP Server: Identifies client connection failures caused by a rogue DHCP server event. This could be an event where an untrusted port drops traffic from DHCP servers to block unauthorized servers.
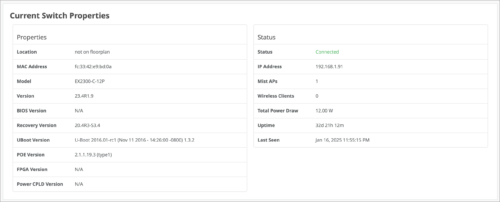
Enhancement to Current Switch Properties in switch Insights
The Current Switch Properties section on the switch Insights page displays the following additional information about the switch: BIOS Version, Recovery Version, Uboot Version, PoE Version, FPGA Version, Power CPLD Version.
Protect-RE configuration optimized for NTP
For switches, we have optimized the Protect-RE configuration for the protocol NTP. Previously, when the Protection of Routing Engine feature was enabled on a switch, the output of the command ‘show ntp status’ used to fail. With this update, we have fixed that issue.
WAN Assurance
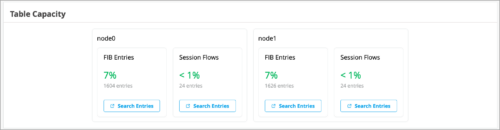
Table Capacity Insights (FIB Entries, Session Flows)
The WAN Edge Insights page provides the following indicators in the new Table Capacity section:
- FIB Entries: Displays the current number of FIB entries and the percentage of utilization, essentially showing how much of the available FIB space is currently being used.
- Session Flows: Displays the current number of active sessions and the percentage of session flow utilization based on the device’s capacity.
You can also click the Search Entries button under each metric to open a shell view in a new window where you can search for entries after specifying filters. In the case of a high availability cluster, Table Capacity indicators are displayed for each node.
OSPF testing tools for WAN edges
The Utilities menu on the WAN edge details page now includes testing tools for verifying Open Shortest Path First (OSPF) configuration and statuses. The following OSPF tools are now available:
- Show Summary: Displays a summary of OSPF database information (equivalent Junos command: ‘show ospf database summary’).
- Show Interfaces: Displays the status of OSPF interfaces (equivalent Junos command: ‘show ospf interface’).
- Show Neighbors: Displays information about OSPF neighbors (equivalent Junos command: ‘show ospf neighbor’). CPU utilization might increase while the device learns its OSPF neighbors. We recommend that you run this test after the device learns and establishes OSPF neighbor adjacencies.
- Show Database: Displays the entries in the OSPF version 2 (OSPFv2) link-state database, which contains data about link-state advertisement (LSA) packets. You can choose to view the data with the Self Originate flag set as True (equivalent Junos command: ‘show ospf database advertising-router’ self) or False (equivalent Junos command: ‘show ospf database’).
- Show Routes: Displays the entries in the OSPF routing table (equivalent Junos command: ‘show ospf route’).
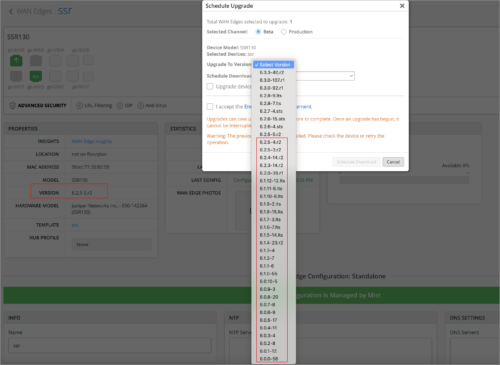
Support for firmware downgrade (SSR)
You can now downgrade the firmware version running on an SSR. You can do this by selecting a lower version of the firmware from the Upgrade Firmware page, accessed from the Utilities menu on the WAN edge details page.
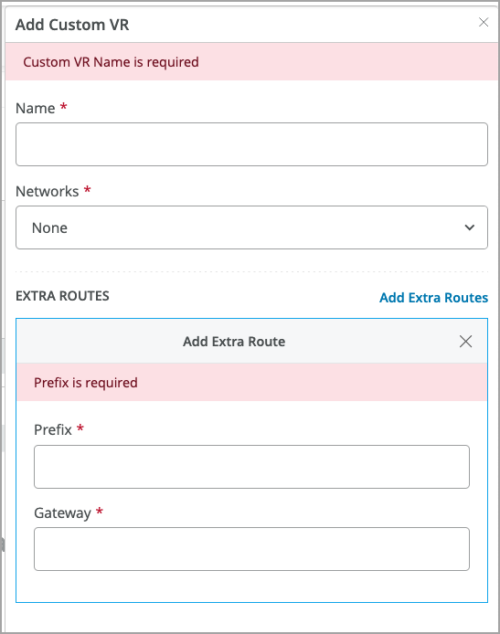
Static routing support in custom VRs (SRX)
You can configure static routes in virtual routers (custom VRs) at the organization level templates, site level templates, or at the device level configurations for SRX series firewalls. Previously, Mist supported only OSPF and BGP routes in custom VRs. Static routing is preferred when the complexity of a dynamic routing protocol is not desired.
To configure static routes, use the Add Extra Routes button on the Add Custom VR window, accessed from the LAN section of the WAN edge configuration page (or template).
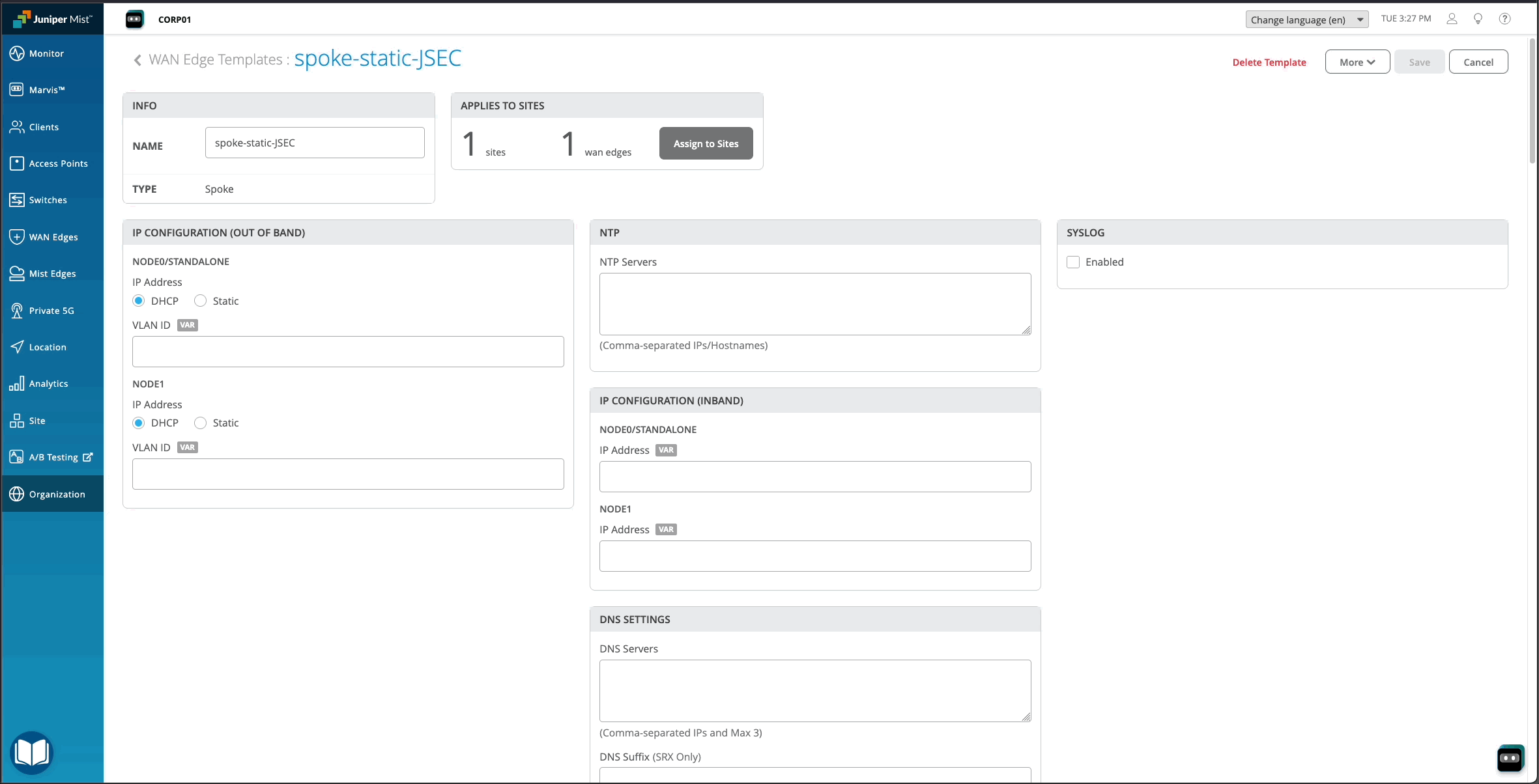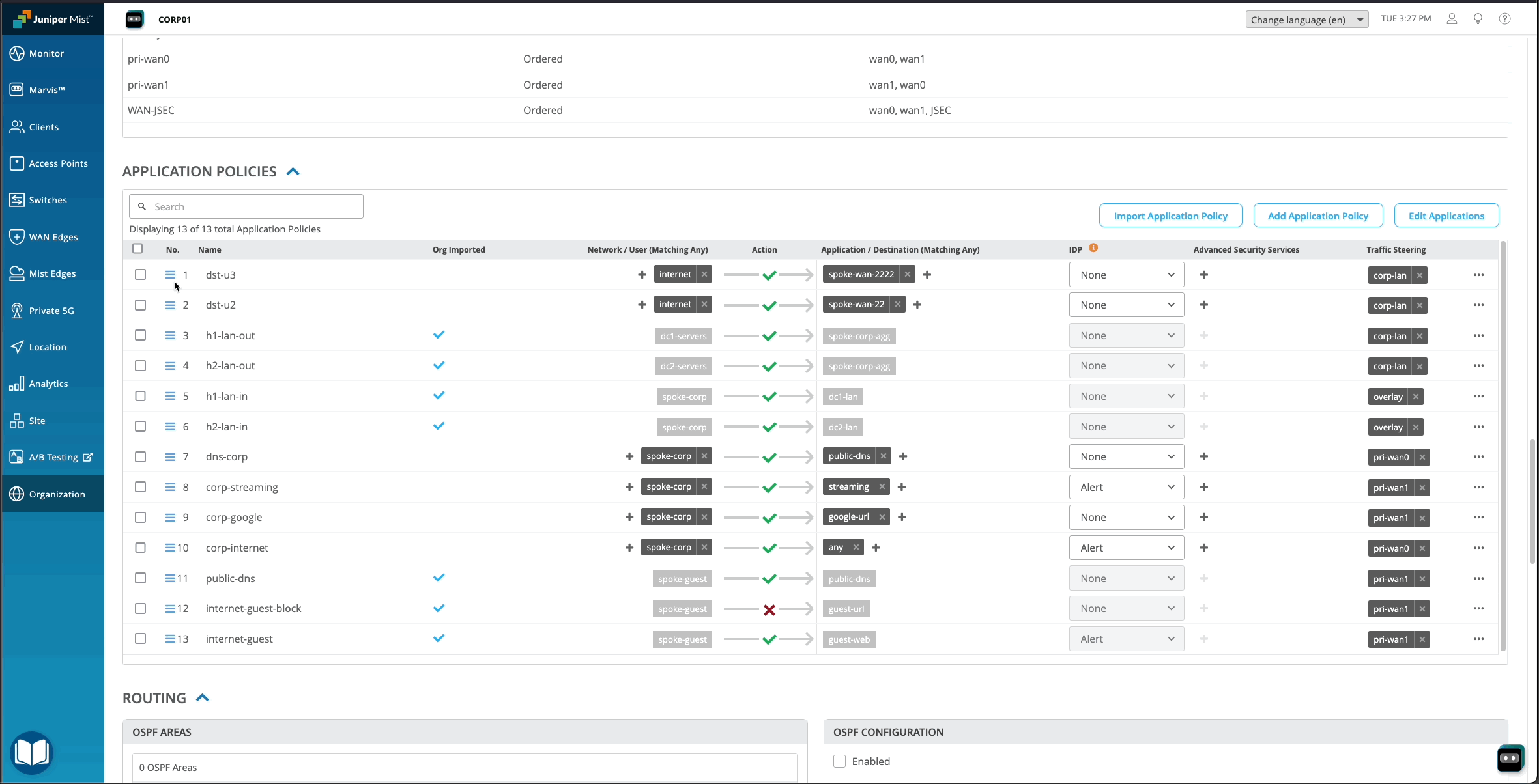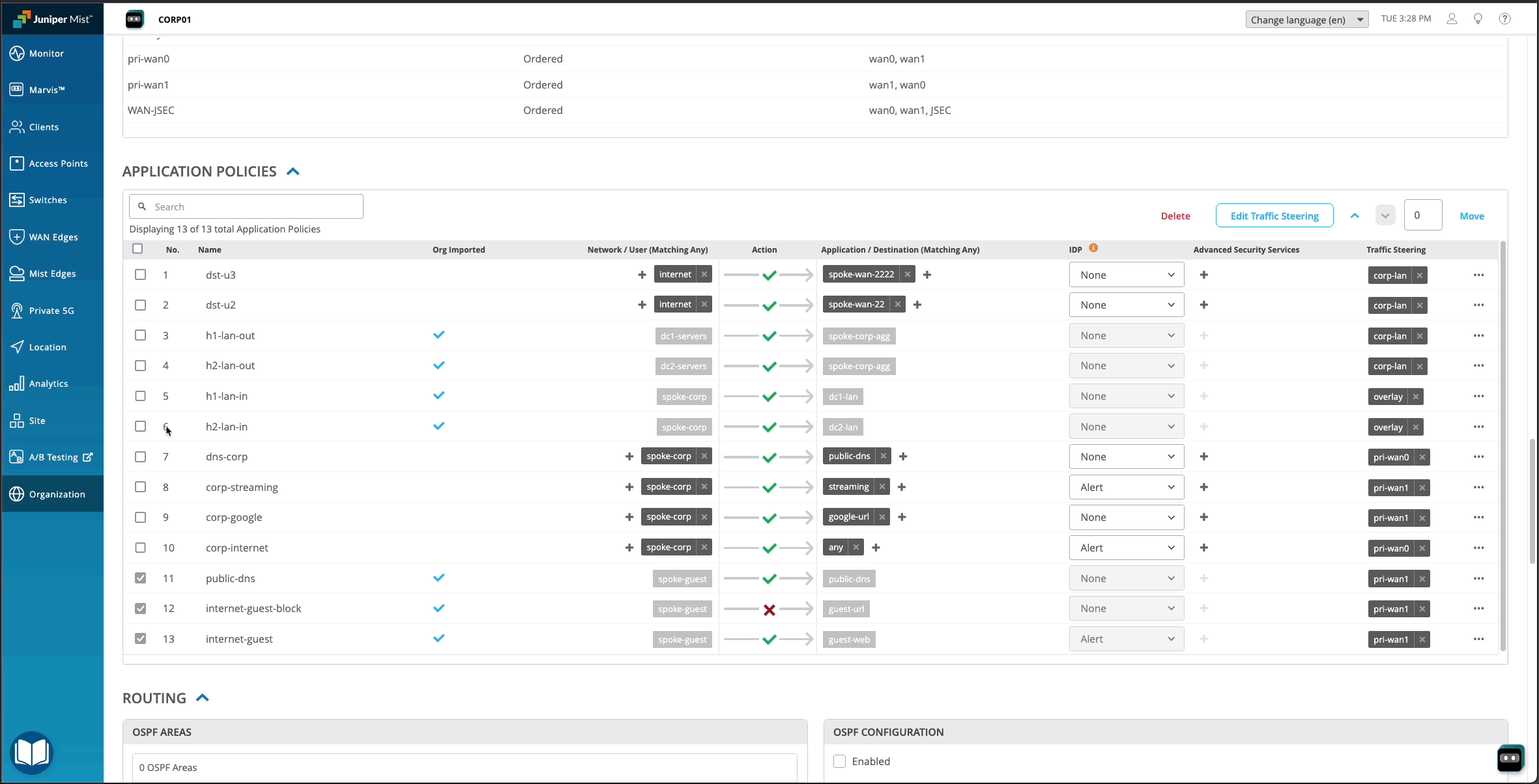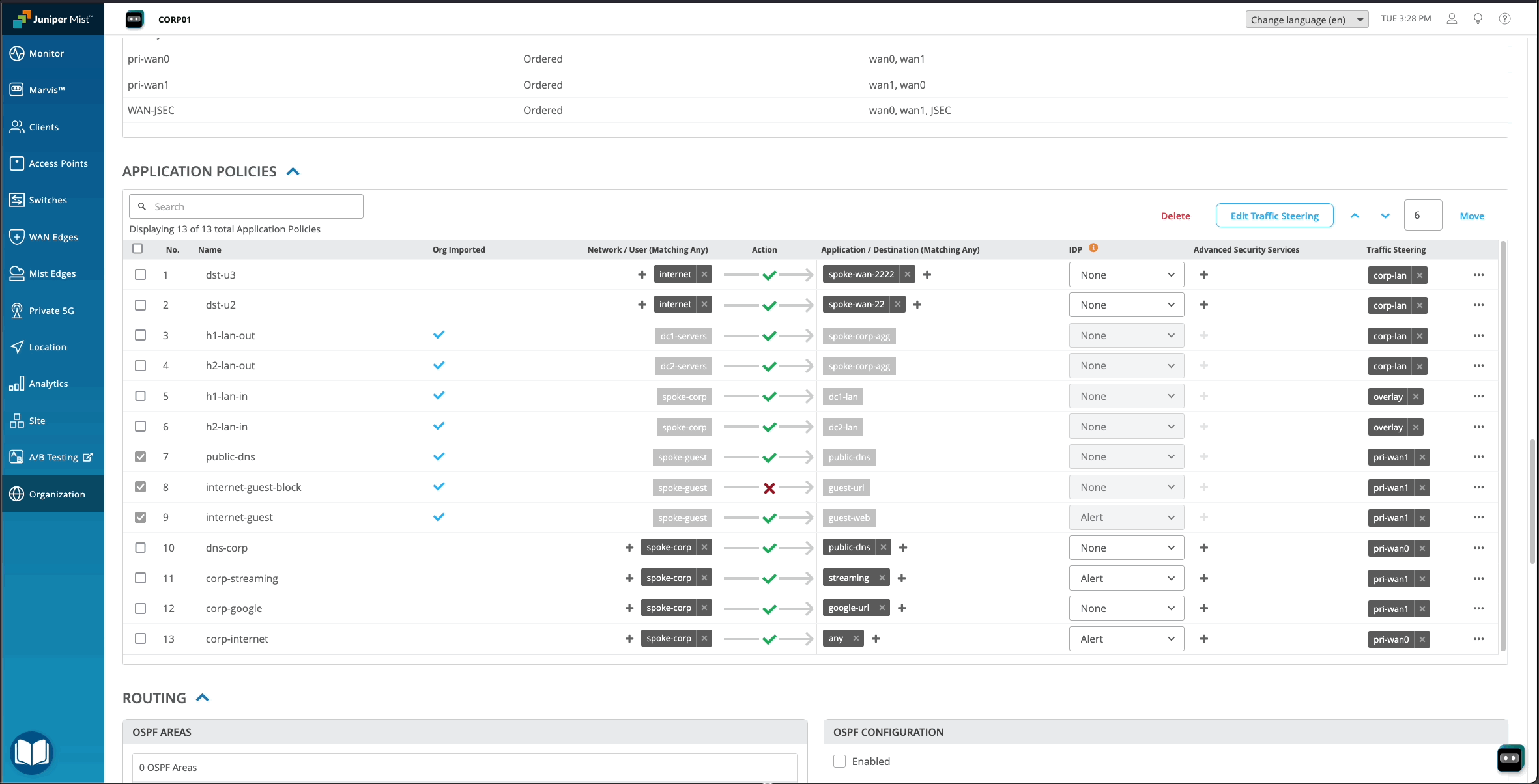
Drag and drop to reorder application policies
On the WAN Edge templates, you can easily reorder application policies by using drag and drop. This option is helpful when a template contains a large number of application policies, and you need to change the order in which the policies are listed or applied.
Support for testing your WAN link speed (SRX)
You can test the speed of WAN links on SRX devices to ensure optimal performance. This feature allows for new link qualification and on-demand speed tests if a low link speed is suspected. This feature is already available for SSR devices.
To run a speed test, navigate to the SRX WAN edge details page (WAN Edges > WAN Edges > WAN Edge Name), select the WAN port from the port panel, and then click the Run Speed Test link in the Networks section.
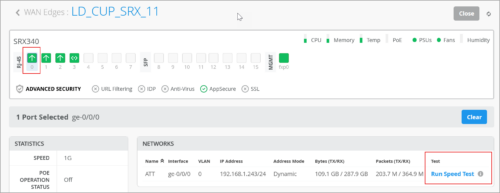
Before running the test, ensure that the WAN link has connectivity to the Internet, where the speed test infrastructure can be reached. The speed test feature does not require any firmware version update for your SRX.
Anti-virus configuration for application policies
You can apply an anti-virus configuration to application policies under Advanced Security Services for WAN edge devices. Antivirus is part of our secure AI native WAN edge feature set, which includes, in addition, IDS/IPS (IDP), URL Filtering, and SSL proxy. You can either select an anti-virus configuration from a set of predefined values (Default, HTTP(S) Only, and No FTP), or create a custom anti-virus configuration. To apply an anti-virus configuration to an application policy, click the + button in the Advanced Security Services column on the Application Policy page (Organization > WAN > Application Policy). To create a custom anti-virus configuration, use the Add Anti-Virus Profile button. You can also view the security events against the anti-virus configured from the Site > Security Events > Anti-Virus page.
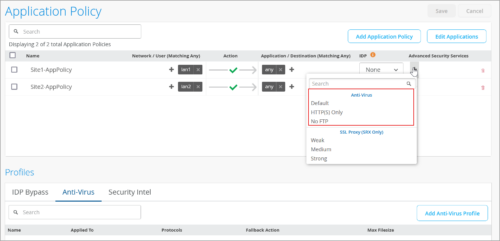
Note: This feature requires additional device side licenses.
Protect-RE configuration optimized for NTP (SRX)
For SRX firewalls, we have optimized the Protect-RE configuration for the protocol NTP. Previously, when the Protection of Routing Engine feature was enabled on an SRX firewall, the output of the command show ntp status used to fail. With this update, we have fixed that issue.
Mist Edge
Upgrade strategy for Mist Edge services
When you upgrade the Mist Edge services on multiple Mist Edges in a Mist Edge cluster, you can choose one of the following strategies:
- Simultaneous: The default option, which upgrades all the selected Mist Edges simultaneously. This is the fastest upgrade option.
- Serial: This option upgrades the Mist Edges one by one, one after another. The serial upgrade is the lowest impact option. APs are gracefully moved to another Mist Edge before the upgrade.
MSP inventory now lists Mist Edge devices
The Inventory page in the Mist Managed Service Provider (MSP) portal now lists the Mist Edge devices associated with the organizations that the MSP manages. The inventory page displays this information in addition to the already existing hardware and subscription details.
Security
Juniper Mist achieves SOC 2 Type II attestation
We are pleased to announce that Juniper Mist has achieved SOC 2 Type II attestation. This attestation underscores our ongoing commitment to ensure that controls were effectively designed and operated to protect customers’ data. If you want to obtain the Juniper Mist SOC 2 Type II report, contact your Juniper account representative. Juniper can share the report under a non-disclosure agreement (NDA).

Network Observability and Business Intelligence
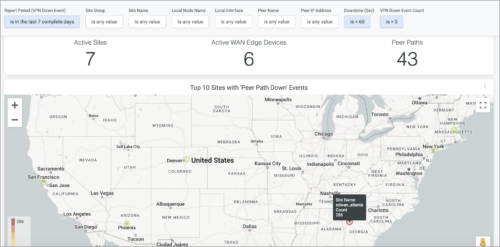
New Premium Analytics dashboard for WAN: Peer-Path Insights
We have added a new Premium Analytics dashboard, Peer-Path Insights, to Mist to give you a consolidated view of organization-wide peer paths and their path down events, such as the top sites and top peer paths encountering path down events. A peer path in the context of Juniper Mist WAN Assurance refers to the connections between session smart WAN edge devices over a WAN network, chosen for redundancy and optimal performance. In a large-scale deployment, this dashboard helps in identifying the most problematic sites, peer paths, and timeline of fluctuations.
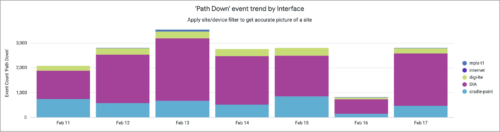
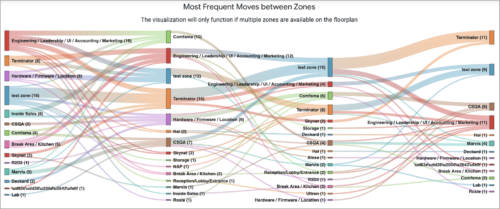
Enhancements to Occupancy Dashboards under Premium Analytics for Wireless
The Occupancy Analytics dashboard, part of Premium Analytics, provides valuable insights into employee visitation, dwell time, and movement within enterprise workspaces. These insights empower operations teams to better understand workspace utilization patterns, optimize space allocation, and improve energy efficiency.
Key Enhancements:
- Weekday Filters: Analyze occupancy trends for specific weekdays or working days to optimize scheduling and resource allocation.

- Time-Based Occupancy Insights: Understand peak usage hours by monitoring the occupancy trends by day of the week and hour of the day.

- Zone Occupancy Drill-Down: Gain deeper insights into specific zones to identify underutilized or overcrowded areas.
- Frequent Movement Tracking: Monitor transitions between zones and floors to enhance space planning and employee flow management.
Behavior Changes
Update to PCI reports
Before you run a Payment Card Security (PCI) report on any site (from the Site > Security page), ensure that all APs that are associated with that site are in connected state and have their firmware versions and IP addresses populated. Otherwise, for the APs that are in disconnected state, the appendix section of the report will display a message indicating that the AP’s firmware could not be determined.
Previously, a PCI report run on a site with disconnected APs used to fail indicating that the APs (which are in disconnected state) do not run the latest firmware versions.
Feature Deprecation
Unpaginated APIs responses to be deprecated
Currently, the GET /orgs/:org_id/inventory request returns an unpaginated, full list of inventory devices. Starting from April 30, 2025, this API will provide paginated responses, wherein each page will return up to 1000 devices and any additional devices must be fetched using the page parameter. Currently, if you query this API directly and have over 1000 devices in your organization inventory, we recommend that you update the scripts to handle the paginated responses.





