Marvis
Application Experience Correlation and SLEs
Monitoring the network health is critical to ensuring a positive user experience across an organization. With this release, Juniper Mist provides a cloud-to-cloud integration to analyze, correlate, and classify collaboration user experience based on correlation of network parameters. Mist uses performance indicators from Zoom and Microsoft Teams to assess the network health, as these applications are considered highly sensitive to network performance. The underlying idea is that if Zoom and Teams are performing well, it is a strong indication that all other user applications are also performing well.
You can view the user experience data for these applications on the Application tab of the service levels page (Monitor > Service Levels > Application). The Application tab appears only for those organizations that have Zoom or Teams integrated and have an active ‘Marvis for Wireless’ subscription. For more information on how to integrate these applications with Mist, see Zoom Integration Overview and Microsoft Teams Integration Overview.
The Application tab on the service levels page shows the following information:
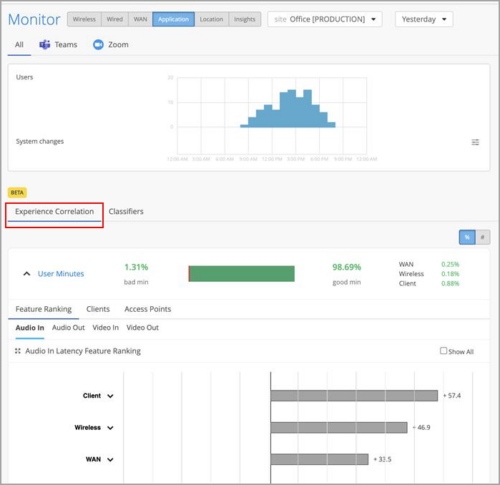
- Experience correlation—The experience correlation view provides visibility into the performance of Teams and Zoom applications at a site or an organization level. The correlation data helps network administrators quickly identify issues causing bad user experiences across a site or an entire organization. This view includes a feature contribution ranking graph that highlights which feature contributed the most to an issue. It also provides insights into the impacted clients and APs that the clients are connected to.
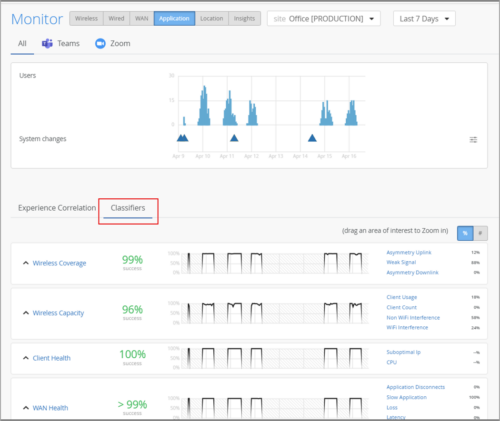
- Application SLE Classifiers—Mist organizes the factors contributing to positive or negative user experiences into Service-Level Expectations (SLEs). The SLE dashboard provides a high-level view of the low service levels and the types of issues that need to be addressed. The following SLE metrics are available: Wireless Coverage, Wireless Capacity, Client Health, WAN Health, and Partner Link.
For more information, see Application Experience and SLE Classifiers.
Wired Assurance
Juniper CloudX is generally available for EX2300, EX3400, EX4650, and QFX5120 switches
Juniper CloudX, a new architecture integrated into Junos OS to provide faster and more secure communication between Juniper switches and the Mist cloud is now generally available for EX2300, EX3400, EX4650 and QFX5120 switches. Previously this feature was generally available only for EX4100 and EX4400 switches.
Benefits of CloudX
- Real-time data updates—Utilizing the Junos Telemetry Interface (JTI), CloudX ensures that events are transmitted to the cloud every 10 to 15 seconds, with statistics updated every 60 seconds, providing up-to-date network insights.
- Packet capture—The Mist cloud offers on-demand packet capture for switches, allowing the initiation of packet capture on a single switch port or a range of ports to view transit or control traffic. It also offers dynamic packet capture for wired ports.
- Proxy server support—CloudX supports both static and dynamic proxy configurations, allowing switches to connect to the Mist cloud via a proxy server. Dynamic proxy information can be provided through DHCP option 43.
Supported platforms and availability
CloudX is generally available on the following platforms with the specified Junos OS releases:
| Platforms | Supported Junos OS Release |
| EX2300/EX3400 | 23.4R2-S4 and above |
| EX4000/EX4400/EX4100 | 22.4R2-S1 and above |
| EX4650/QFX5120 | 23.4R2-S4 and above |
CloudX is installed on the above switches by default when they are upgraded to the Junos versions mentioned.
You must ensure that the firewall port towards jma-terminator.xx.mist.com is open and SSL encryption is disabled on the firewall (for more information, refer to Juniper Mist Firewall Ports and IP Addresses for Firewall Configuration). If you don’t see CloudX enabled on your switch even after upgrading it to a supported Junos release listed above, contact Juniper support. To check if your switch is communicating with Mist cloud by using CloudX, refer to the steps listed in Troubleshooting Juniper CloudX.
Schedule and automate switch upgrades
You can now easily create and manage Junos OS upgrade schedules for switches that are connected to the Mist cloud. You can also configure settings to automatically upgrade new switches when they are onboarded to Mist.
The option to create and manage upgrade schedules can be accessed from the Firmware Upgrade tile on the organization settings (Organization > Settings) or site configuration (Organization > Site Configuration) page.

The switch upgrade enhancements include the following:
- Add Upgrade—This setting allows you to schedule upgrades for switches that are already connected to the Mist cloud. You also have an option to execute upgrades immediately. Upgrade schedules can be set up for specific switch models (upgrades all switches of the specified model) or specific switches across sites.

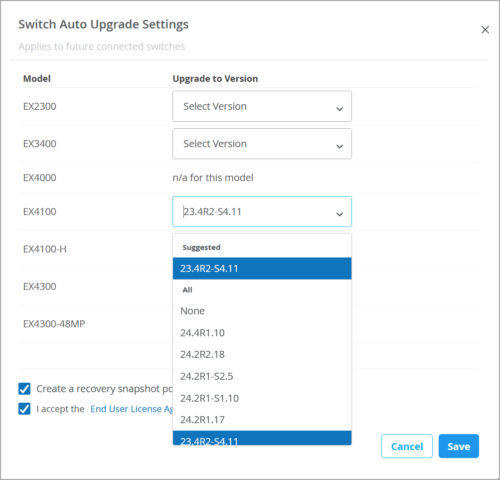
- Auto Upgrade Settings—If you select the Enable Auto Upgrade check box, you can specify a Junos version per switch model, to automatically upgrade a switch the first time it connects to the Mist cloud. This does not apply to the switches that are already online. This feature is available only at the organization level.
- Upgrade Status—Lets you view the status of your scheduled upgrades and past upgrades. You can also modify or cancel the upgrade schedules.
For more information, refer to Upgrade Junos OS on Switches.
Virtual Chassis modification made easy
Previously, each Virtual Chassis device in Mist used the physical MAC address of the FPC0 member as the device ID. This meant that removing or replacing the FPC0 member could disrupt the connectivity. With this release, each newly onboarded Virtual Chassis will get a device ID which is not tied to any member device. This device ID is a virtual MAC address that is cloud-assigned. In a virtual MAC-enabled Virtual Chassis, you can replace or renumber all members (including FPC0) in a single step without disrupting the connectivity.

The Existing Virtual Chassis devices connected to the cloud will continue to function with FPC0 as the device ID unless the FPC0 is replaced or renumbered from the cloud. Removing or replacing the FPC0 member from an existing Virtual Chassis will transition that Virtual Chassis to a virtual MAC-enabled device without impacting operations.
To identify a virtual MAC-enabled Virtual Chassis, look for the Device IDs on the switch details page (Virtual Chassis page). A device ID starting with 0200 indicates that the Virtual Chassis is virtual MAC address-enabled.

Connect collapsed core switches in full mesh (EVPN Multihoming)
EVPN Multihoming (collapsed core with ESI-LAG) campus fabric now supports connecting switches in full mesh topology in the collapsed core layer. In a full mesh topology, you can connect each switch to every other switch. This support provides the EVPN Multihoming campus fabric with greater resiliency, which ensures continued network functionality even if one device fails. In the image below, you can see an option to connect the switch to all the other three switches added to the collapsed core layer. Previously, switches in the collapsed core layer were connected in a ring topology where each switch was connected to only two other switches even when there were, for example, four switches in the topology.

For more information, refer to Configure Campus Fabric EVPN Multihoming.
Support for Q-in-Q tunneling
You can configure switch ports with Q-in-Q tunneling using all-in-one bundling. Q-in-Q tunneling enables Layer 2 protocol tunneling (L2PT) on interfaces that are not encapsulation tunnels and utilizes MAC address rewrite operation.
Using Q-in-Q tunneling, providers can segregate or bundle customer traffic into fewer VLANs or different VLANs by adding another layer of 802.1Q tags. Q-in-Q tunneling is useful when customers have overlapping VLAN IDs, because the customer’s 802.1Q VLAN tags are prepended by the service VLAN (S-VLAN) tag.
You can configure Q-in-Q tunneling under Port Configuration at the switch level (Switches > Switch Name), site level (Site > Switch Configuration > Select Switches Configuration), and organization level (Organization > Switch Templates > Select Switches Configuration). The configuration includes selecting Q-in-Q as a configuration profile, choosing a Port Network (S-VLAN), and specifying other port configuration parameters.
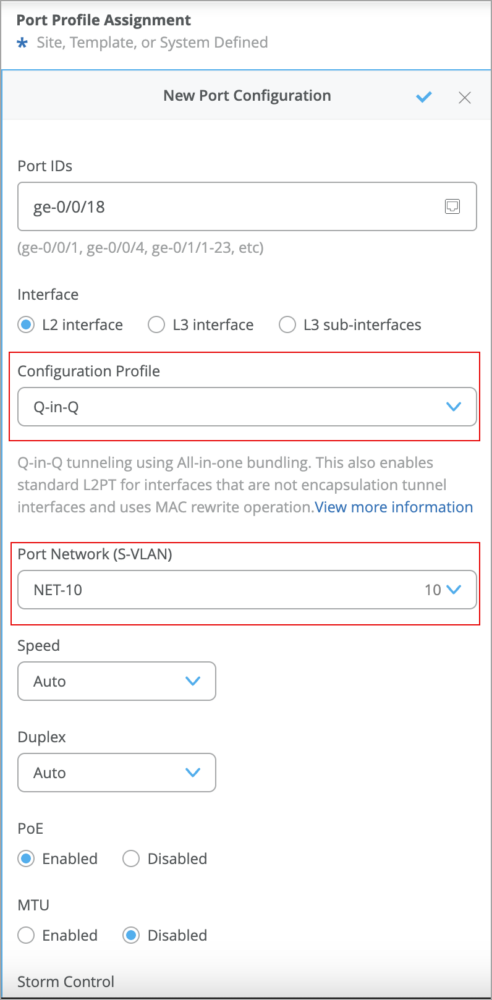
For more information, refer to Configure Q-in-Q Tunneling on a Switch Port.
Site variable support for DHCP server and relay configuration
Mist supports the use of site variables in DHCP server and relay configuration. You can configure DHCP server and relay from the switch details page. The site variable support is also available for the DHCP relay configuration in campus fabric (on the Networks Settings tab).
Note: The configuration fields that support site variables show the variable format underneath them.
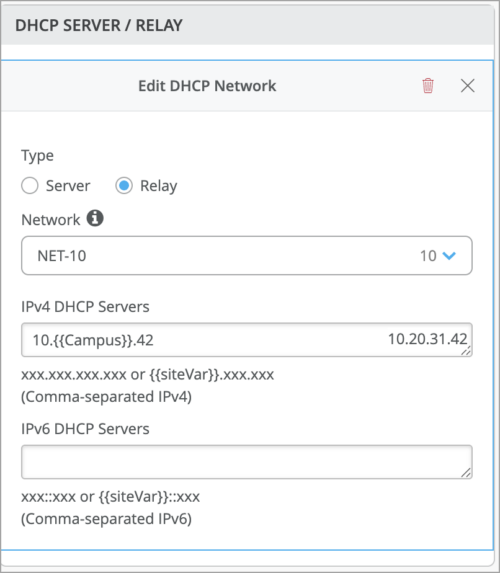
Site variables help you address use cases that require you to configure a set of unique fields for different sites. Site variables provide a way to use tags to represent real values so that the value can vary according to the context where you use the variable. This means the same variable can configure different values in different sites.
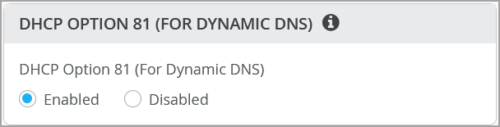
Support for DHCP option 81
You can now enable switches with DHCP option 81 support. When this option is enabled on a switch, the clients connected to that switch can send their fully qualified domain name (FQDN) to the DHCP server while requesting an IP address. This allows the DHCP server to update DNS records accordingly.
You can enable a switch with the DHCP option 81 support at the organization level (Organization > Switch Templates), site level (Site > Switch Configuration) and device level (Switches > Switch Name).
Filter switch events by multiple event types
On the Switch Insights page, you can now filter switch events by multiple event types. This allows you to view events related to the specified event types at the same time. Previously, you could filter the events by only a single event type.

Protection of Routing Engine configuration improvements
We have made the following improvements to the Protection of Routing Engine feature:
- In the default BGP configuration, we have included two different filter terms for source and destination to accommodate any variations in different EX Series switch models. This change will have no impact on BGP sessions.
- In the ‘allow_dns’ term in the DNS configuration, we have included a prefix list which can be used to allow traffic only from DNS servers configured on the device. This change ensures that no client with source-port 53 and protocol TCP/UDP is sending rogue traffic to the switches on the network.
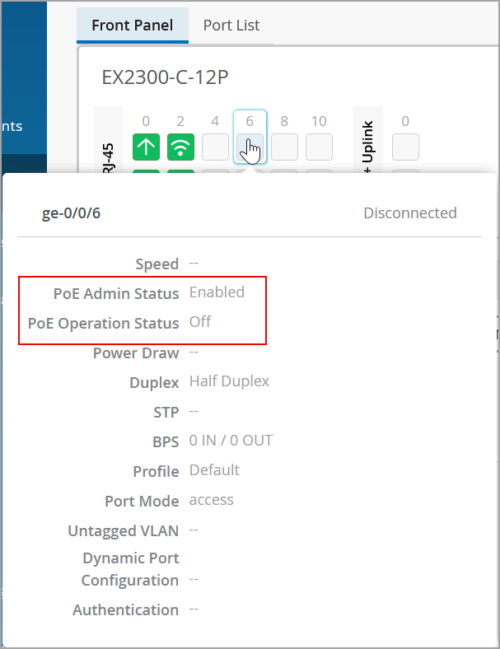
Enhancements to PoE status display
To improve the clarity of the Power over Ethernet (PoE) status display, we have made the following enhancements to PoE status display on the switch port status view (displayed when you hover over the port) in the front panel section of a switch details page:
- Renamed the field ‘PoE’ to ‘PoE Admin Status’. This field indicates the PoE interface’s administrative status, which can be Enabled or Disabled. If the PoE interface is disabled, it can provide network connectivity, but it cannot provide power to connected devices.
- Added a new field named ‘PoE Operation Status’. This field reflects the PoE Operation Status of the interface. The status can be one of the following:
- ON—The interface is currently supplying power to a powered device.
- OFF—PoE is enabled on the interface, but the interface is not currently supplying power to a powered device.
Alert timer for switch offline event
You can now configure a switch offline alert timer which defines how long after a switch goes offline users should be alerted to the issue. As a best practice, set the timer to send alerts to users 5 minutes after the switch goes offline. Delaying the alert generation in a switch offline event ensures that you don’t receive an offline alert for any connectivity flaps. The supported timer range is 0 to 240 minutes. By default, the timer is set to 0 minutes (to alert the user immediately after the switch goes offline). Previously, the only available alert timer was a global setting and was applicable to all the device types (such as switches and APs).

Upcoming Changes: Enhancements to default user ‘mist’ for accessing remote shell
For an improved user experience and role-based control, the next Mist cloud release will offer a few enhancements to the way users control the remote shell utility. The enhancements will include the following:
- The following two new users will be added to all switches connected to the cloud:
- mist-web-admin
- mist-web-viewer (read-only)
The remote shell function will begin to use the user ‘mist-web-admin’. The user ‘mist’ will be phased out.
- You will also have an option to select the user ‘mist-web-viewer’ for controlling the remote shell utility from the organization settings. This user will only have read-only access.
Location Services
Auto Zone (Beta)
You can now use Auto Zone to automatically identify location zones for you based on the boundaries of a given floorplan. To do this, navigate to Location > Live View and select the floorplan. Then, select the Beacons and Zones button, and finally, select the Auto Zone button. Auto Zone is especially useful for customers whose deployments contain a vast number of rooms, as it automatically identifies and names the zones for you, thus allowing for more precise analytics to be gathered.

Auto Zone does the bulk of the work for you. Once Auto Zone identifies the zones for you, you must finalize them. You can physically drag the corners of a suggested zone to adjust it as needed. You can also delete and rename any of the suggested zones as you see fit. If your floorplan has zone names clearly labeled on it, Auto Zone will carry those zone names over for you.
WAN Assurance
Juniper Advanced Threat Prevention features for SRX
We have introduced the following Juniper Advanced Threat Prevention (ATP) features for SRX Series firewalls:
- Security Intel (SecIntel)—SecIntel profiles, which are included in application policies, enable you to block malicious and unwanted traffic such as Command and Control (C&C) communications, compromised IP addresses or IP subnets, and domains connected to malicious activities (See also: SecIntel Feeds Overview and Benefits). You can create these profiles from the application policy screen (Organization > Application Policy).

In a SecIntel profile, you can configure the following actions:- C&C Default Action—Lets you configure actions against C&C servers that have attempted to contact and compromise hosts on your network.
- DNS Default Action—Lets you configure actions against the domains that are known to be associated with malicious activities.
- Infected Host Default Action—Lets you configure actions against infected hosts, which are local devices that are potentially compromised because they appear to be part of a C&C network or exhibit other symptoms.
- Advanced Anti-Malware (AAMW)—This feature detects and blocks malware and unwanted files on the network before they reach an endpoint. Like SecIntel, anti-malware profiles can be created from the application policy screen (Organization > Application Policy) and included in an application policy.
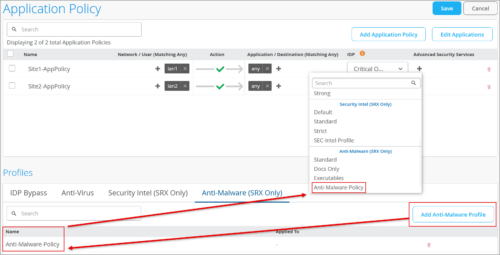
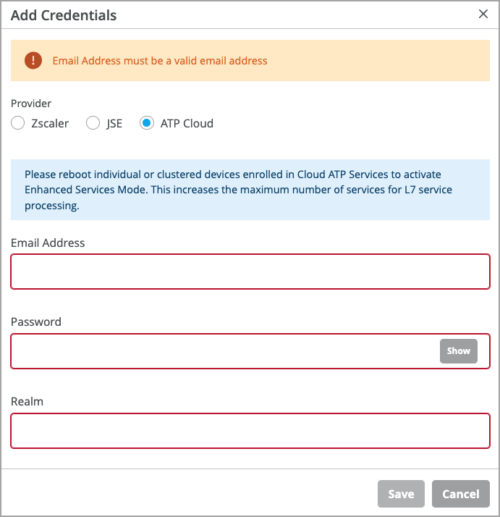
Mist will automatically enroll devices to Cloud ATP Services as needed. For that, you need to input your credentials through the Secure WAN Edge Integration tile the on the Organization > Settings page.
Note: Only the Global instance of ATP is supported in this release.
BGP multihop for WAN edges
BGP multihop enables BGP peers to establish a connection even if they are not directly connected. This feature is useful in scenarios where BGP peers need to communicate across multiple non-BGP routers (hops) to reach each other. You can enable BGP multihop support by setting the multihop time to live (TTL) value to greater than 1 from the Edit Neighbor section on the BGP Group configuration window. This allows the BGP packets to traverse multiple hops to reach the peer.

BGP over GRE tunnels
You can now set up BGP sessions over generic routing encapsulation (GRE) tunnels to enable BGP to function across non-directly connected networks. Generic routing encapsulation (GRE) provides a private path for transporting packets through an otherwise public network by encapsulating (or tunneling) the packets. The configuration includes the following steps:
- Create a secure edge connector custom tunnel with GRE protocol.
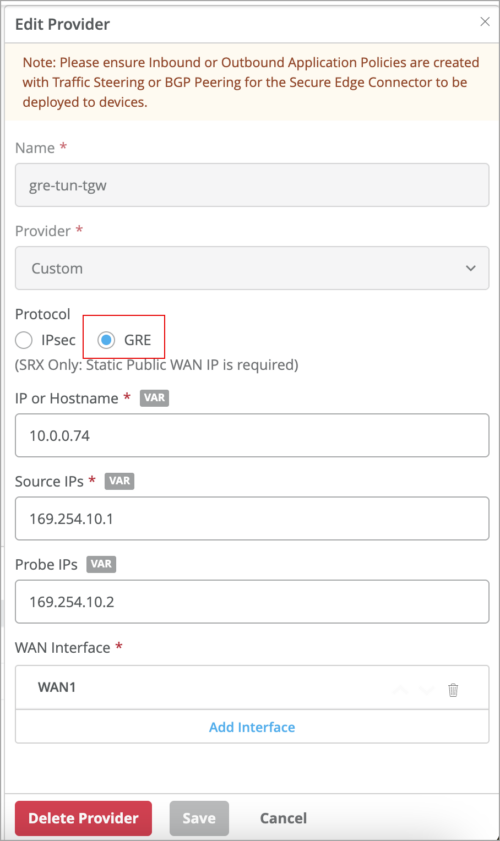
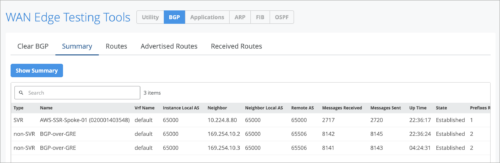
- Use this tunnel in the BGP group associated with the WAN edge.

- Use the WAN edge testing tool to verify the BGP sessions.
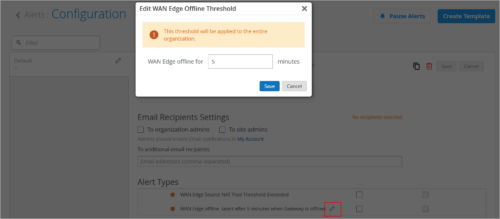
Alert timer for WAN edge offline event
You can now configure a WAN edge offline alert timer which defines how long after a WAN edge goes offline users should be alerted to the issue. As a best practice, set the timer to send alerts to users 5 minutes after the WAN edge goes offline. Delaying the alert generation in a WAN edge offline event ensures that you don’t receive offline alert for any connectivity flaps. The supported timer range is 0 to 240 minutes. By default, the timer is set to 0 minutes (to alert the user immediately after the WAN edge goes offline). Previously, the only available alert timer was a global setting and was applicable to all the device types (such as switches, WAN edges, and APs).
Network Observability and Business Intelligence
New Premium Analytics dashboard for location: Asset Insights
We’re excited to announce the launch of the Asset Insights Dashboard which gives you end-to-end visibility into BLE-tagged assets across your enterprise. The dashboard helps you monitor your assets and track their movements across your environment, enabling better planning, audits, and operational decisions.
The top section of the dashboard provides a high-level view of your asset inventory. It includes metrics like total tracked assets and the assets seen within the past two days. It also shows how assets are distributed across different sites and manufacturers. You can also identify inactive or unresponsive assets and browse the complete asset list using filters for faster discovery.
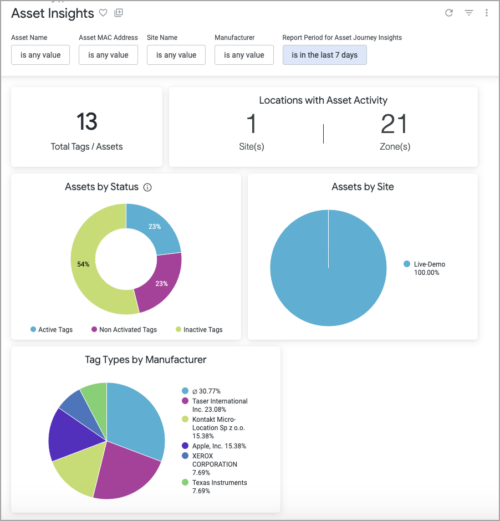
The second section, Asset Journey Insights, focuses on asset behavior and historical movement. It displays the sites and zones that have experienced asset activity, highlights the most frequently moving assets, and allows you to investigate the journey of a specific asset through a visual map. This is especially useful for uncovering utilization trends, reviewing workflows, or tracing movement paths during audits or recovery efforts.

Subscription management for Premium Analytics
We have enhanced the Premium Analytics (PMA) subscription management to efficiently apply available subscriptions to dashboard types and associated device types. Admins can now choose any combination of WAN, Wired, Wireless + Location dashboard types, and the PMA subscriptions will be counted only against the associated device types.
Upon selection of dashboard types, only the relevant dashboards will be displayed. If no selection is made, wireless dashboards will be enabled by default, and the PMA subscriptions will be counted against the access points.
For the existing PMA deployments, we recommend that you make the selections to comply with the subscription count.

Faster refresh on events dashboards (available by April 30th, 2025)
We have reduced the data refresh interval on Premium Analytics Dashboards from once a day to every two hours, significantly improving data timeliness and usability. This enhancement is being rolled out in stages. As part of this release, the following dashboards will now refresh every two hours:
- Wireless Client Events
- Security Assurance
- Access Assurance Insights
More dashboards will be transitioned to faster update cycles in upcoming releases.
Simplified Operations
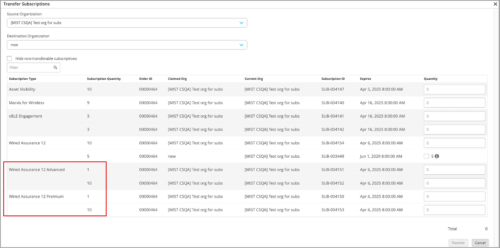
MSP Transfer Subscription enhancements
We have introduced a few enhancements to the Transfer Subscription feature in the MSP portal. Users will now be able to transfer Junos Flex Term subscriptions associated with Wired Assurance. Additionally, transfer subscription operations will be allowed under all conditions, aligning them with the behavior of API-based operations. Previously, the Mist portal did not permit transfers when the number of subscriptions was less than or equal to the number of devices. This update provides MSP operators with greater flexibility in managing subscriptions.
Auto Activation of Junos Application Identification (App-ID) licenses for Branch SRX
A Flex term subscription for WAN Assurance is a bundled subscription which includes WAN Assurance, VNA, and Junos App ID licenses. You can find the details of available Flex term subscriptions for WAN Assurance along with the supported SRX Series firewall models at Flex Term Subscriptions for SRX Series.
Previously, when the Flex term subscriptions were loaded onto the Mist portal, WAN Assurance and VNA would get auto-activated, but the Junos features included in Standard or Advanced license needed an additional step to get activated. Users had to use Juniper Agile Licensing (JAL portal) to obtain the Flex license file, and then install it via the CLI on individual SRX Series firewalls. This solution eliminates the manual step, and automatically installs Flex licenses on the SRX Series firewalls to enable relevant features on Junos.
| SKU | SKU Character Description | ||
| S-SRX-S/A-C1/C2/C3-1/3/5 | S—Software
SRX-Product name SRX Series C1/C2/C3 – Device class S-Standard A—Advanced 1/3/5—Subscription term 1, 3, or 5 |
||
| Class | SRX Models | ||
| Class 1 | SRX300/SRX320 | ||
| Class 2 | SRX340/SRX345 | ||
| Class 3 | SRX380 | ||
You can find more details at Software Subscriptions for SRX Series Firewalls and Flex Term Subscriptions for SRX Series Firewalls.
Installed Base Insights
Enhance your installed base insights through account integration
Linking your Juniper account to your Org will integrate the information Juniper maintains about your devices with your Assured experience.
Displayed through the Installed Base view, Asset and Contract information, Hardware or Software End of Life/Support/Engineering dates, Bug Exposures [PBNs], and Security Vulnerability Exposures [SIRTs] artifacts will be associated with both the devices that have been onboarded as well as those devices covered by an active Juniper support contract that have yet to be onboarded. Juniper support information, relevant and specific to your deployment, will now be pulled into your experience and will be available and current as you need it.
Support
Attach files to your support tickets
If you have any screenshots, log files, videos, or other files to better inform our support team about the issue, you can attach that to a support ticket. To do that use the Upload Attachments option on the support ticket creation page. A maximum of three files can be attached to a support ticket. The file size limit is 5 MB per file. This feature is available for the following ticket types: Problem, Questions, Configuration Help, and Subscriptions. The following file types are supported: jpg, jpeg, png, txt, doc, docx, ppt, pptx, xls, xlsx, rtf, zip, rar, log, and mp4.

Behavior Changes
Change in the inactivity timeout behavior
Mist now tracks the inactivity timeout duration configured at the organization level across your browser tabs. This means that when you have multiple Mist pages open in different tabs, staying active in one tab prevents the other tabs from logging you out once the inactivity timeout is reached. Previously, even if you were active on one of the tabs, the inactive tabs would log you out when the inactivity timeout was reached.
Feature Deprecation
Unpaginated APIs responses to be deprecated
Currently, the following API requests return an unpaginated, full list of inventory devices.
- GET /api/v1/orgs/:org_id/inventory
- GET /api/v1/sites/:site_id/stats/devices
Starting on April 30th, 2025, these API requests will fetch paginated responses to limit the size of the response. By default, the API response will fetch the first 100 entries in the list. You can modify the number of entries in the response (range: 1 to 1000) by using the query parameter ‘limit’.
Currently, if you query this API directly when you have more than 100 devices in your organization inventory, we recommend that you update the scripts to handle the paginated responses.
For more information, see Pagination.