prerequisite
Before you begin configuring the Radius proxy service on Mist Edge, below steps are prerequisite –
- Mist Edge claimed and configured (OOBM IP, Tunnel IP)
- Mist Tunnels configured and mapped with Mist Edge cluster
- WLAN configured with radius authentication and forwarding mapped to Mist Tunnels
All above steps are covered in Mist Edge Getting Started guide – https://www.mist.com/documentation/category/mist-edge/
Radius Proxy
In certain instances where the deployment is big and includes a larger number of Mist Access-points that must be installed and require SSIDs with 802.1x authentication. In this scenario, it may not be possible to add all these access points as individual clients in the RADIUS server.
This document talks about an alternative approach to fit this use case. In such situations, a RADIUS proxy can be set up such that instead of adding the access points as individual clients, only one IP of RADIUS proxy can be used.
The Radius proxy acts as a server toward the Wi-Fi AP RADIUS clients, and as a client toward RADIUS servers.
Configure Radius PRoxy on mist edge
The RADIUS proxy feature allows for the use of the Mist Edge as the source of RADIUS Access-Request messages instead of the access points themselves. This means that the RADIUS server should be configured to whitelist the Mist Edge OOBM IP (or Tunnel IP if enabled Tunnel as source) instead of adding individual access points as clients. This allows bypassing the addition of multiple individual Access points to the radius server for larger deployments.
org-Level MIST edge
Mist Edge by default is an ORG level object, where Mist AP from all sites can form tunnels with.
configuration using dashboard
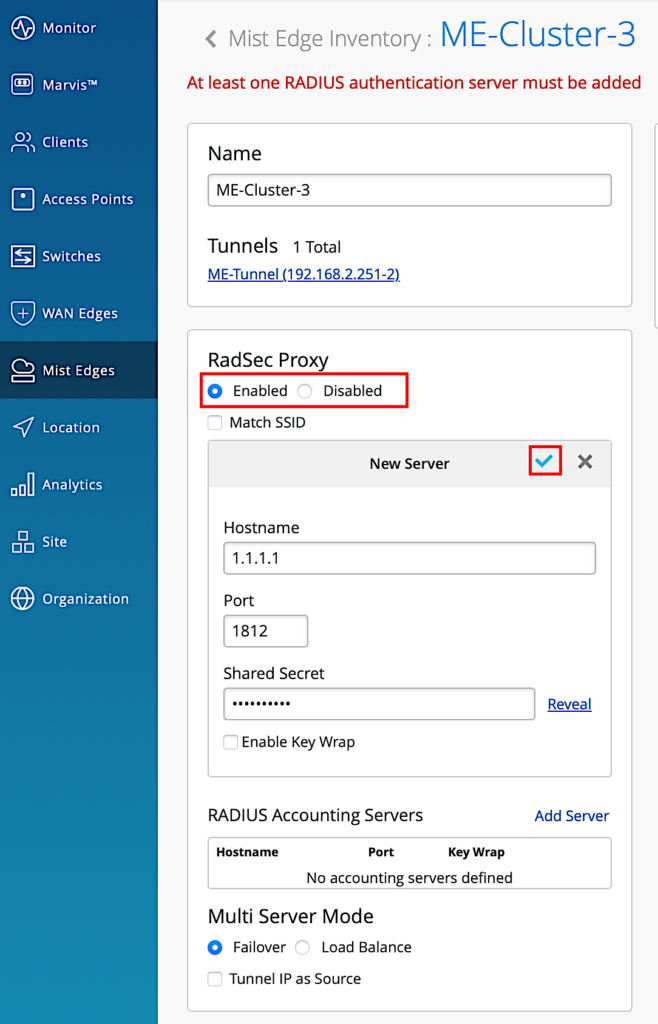
Navigate to Mist Edges > Mist Edge Clusters and select/edit a cluster config
- Enabled the Radius Proxy
- Select Add Server for Radius Authentication Servers
- Enter the Hostname and Shared secret
- Click on blue check mark to save the server settings
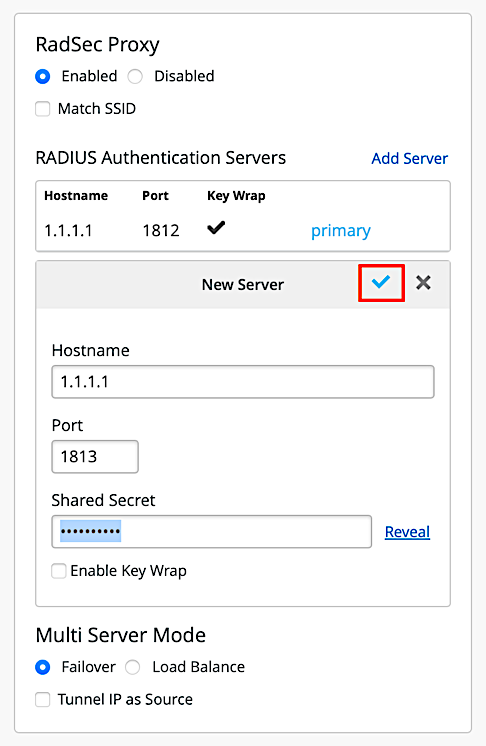
Note: Radius Authentication and Accounting servers are in an ordered list, which means if the first server is not reachable than Radius proxy forwards the request to next available server in the list.
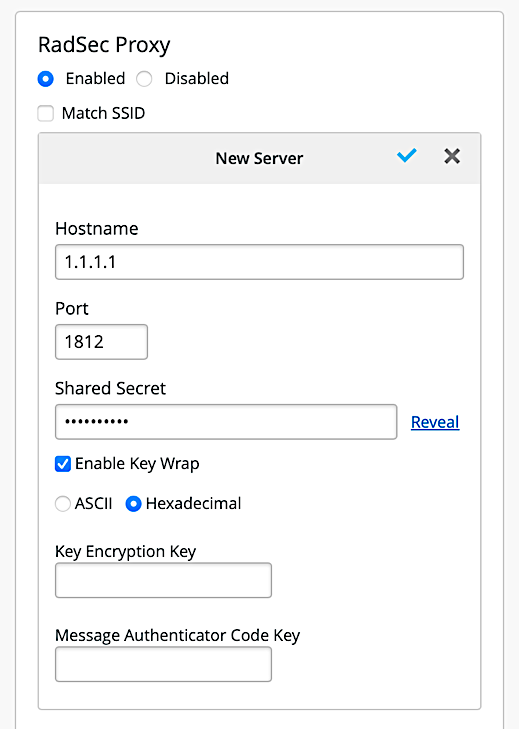
- [Optional] To enable the keywrap and configure the KEK and MACK, select the Radius Authentication Server from the list, and check the Enable Key Wrap field, it will enable additional fields of key type (select ASCII or Hex) and Key values
- [Optional] Repeat the steps 2-5 for Radius Accounting Servers
- [Optional] Select Tunnel IP as Source if you want radius packets (and accounting) to originate with source as Tunnel IP.
Note: In this case the NAS client on the NAC server would be the Tunnel IP of Mist Edge, Else it would be OOBM IP.
- To save the radius proxy settings to the Mist Edge cluster, select the save button
configuration using API
PUT /api/v1/orgs/<ORG-ID>/mxclusters/<CLUSTER-ID>
site-level mist edge
There are some instances, where distributed deployment is required for transitioning from legacy architecture or where sites are large enough to host a Mist Edge(s) on site, Juniper Mist Edges can be assigned to a site and configured for tunneling and radius proxy service for the Aps in the site.
configuration using dashboard
All parameters are same as ORG-level Mist Edge Cluster, except in this case configuration will be present on the Site Configuration.
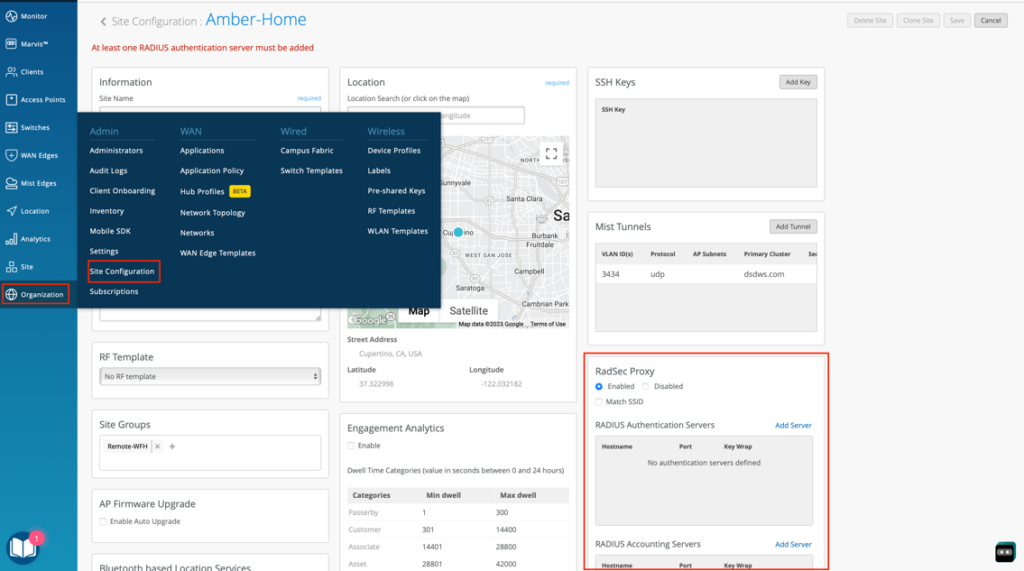
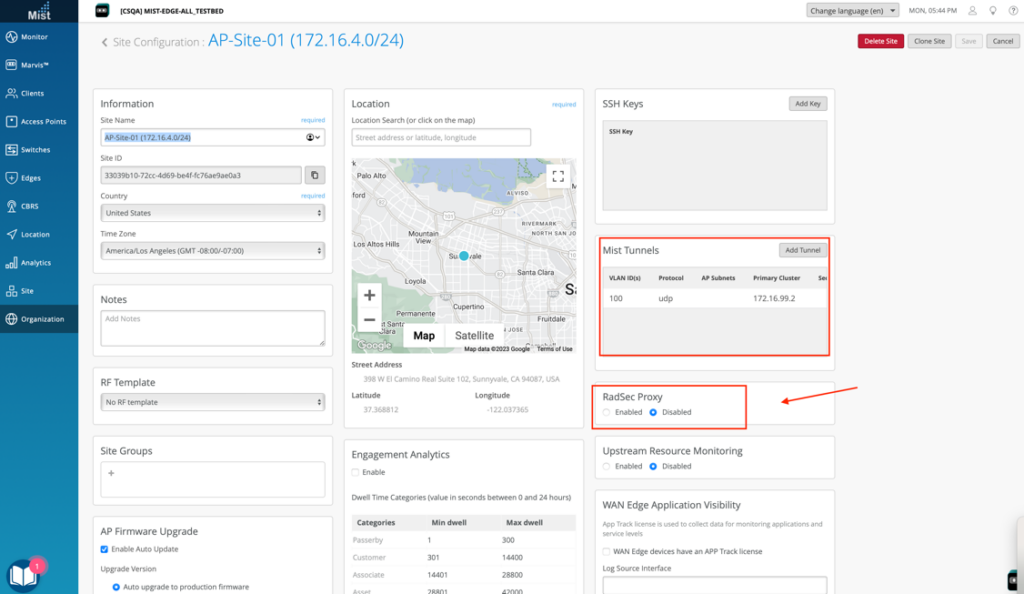
Navigate to Organization > Site Configuration and select/edit a site config
Once Mist Tunnels are configured (Prerequisite), Enable the Radius Proxy as highlighted below
- Add Radius Server details by clicking on Add Server
Configure the Server details (Hostname, Port and Shared Secret).
- [Optional] if Keywrap is required then click on checkbox, select ASCII or Hexadecimal, and enter KEK and MACK
- [Optional] Select Tunnel IP as Source if you want radius packets (and accounting) to originate with source as Tunnel IP
- Once all Server configuration is done, click on blue checkmark to save the configuration. Repeat above steps to add multiple radius server configuration
- Same procedure can be repeated to add Radius Accounting Server(s)
configuration using API
Below is the API and example blob with config, this will ensure that Mist Edge receives radius and keywrap related config and starts the Radius proxy service.
PUT /api/v1/sites/<SITE_ID>/setting
setting wlan affinity for radius server
There are some instances, when the customer deployment requires to use different Radius server based on the SSID name. For example, using a public radius server for eduroam SSID but the corporate radius server for all corporate SSIDs. Mist Edge allows this flexibility in the Radius proxy service, we will cover the configuration in following section.
wlan affinity for radius server using dashboard
Radius proxy service on Mist Edge can be configured to forward radius access (or accounting) request to specific NAC server based on SSID client is connected to.
Navigate to Mist Edges > Mist Edge Clusters and Select an existing cluster or create new cluster
All steps remain same for configuring the radius proxy, except below two additional configurations
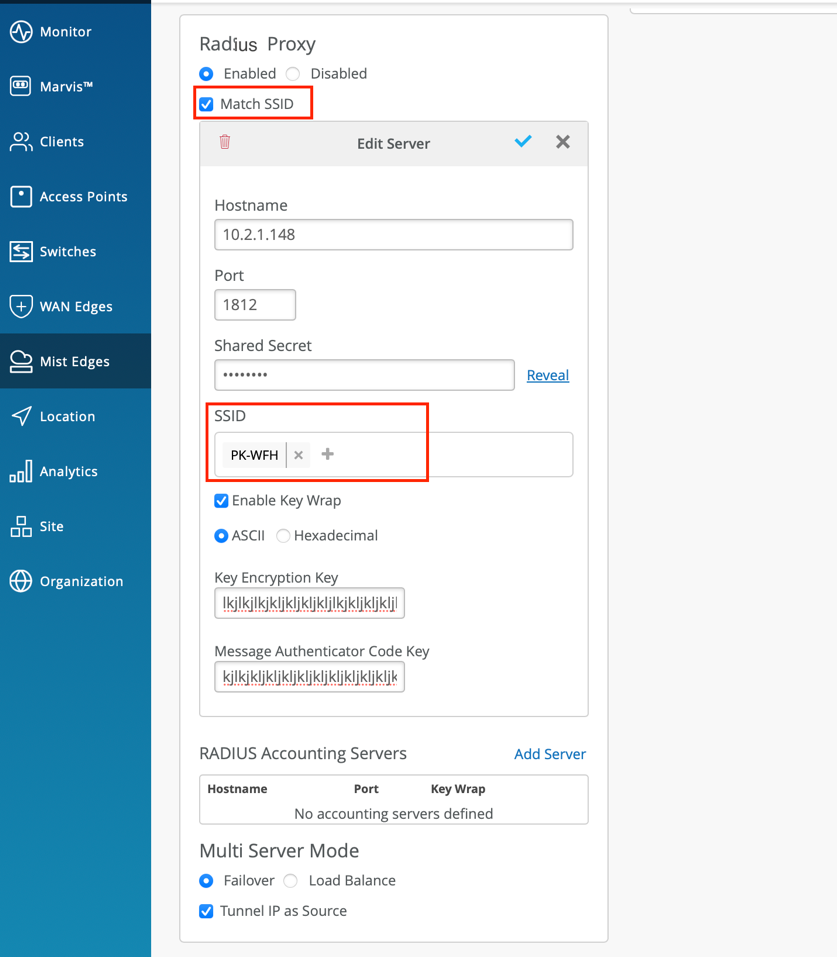
- Select the Match SSID and a new SSID dropdown box will appear for each Auth and Accounting server list
- Select one or more SSID for this radius server by clicking on + under SSID
- Click on blue check mark to save the server settings
- [Optional] Repeat #2 & #3 for any additional Authentication server in the list
- [Optional] Repeat the steps 2-4 for configuring WLAN affinity for Radius Accounting Servers
- To save the radius proxy settings to the Mist Edge cluster, select the save button
wlan affinity for radius server using API
Below is the API and example blob with config, this will ensure that Mist Edge receives radius related config and starts the Radius proxy service.
PUT /api/v1/orgs/<ORG-ID>/mxclusters/<CLUSTER-ID>
wlan affinity for radius server on site edge
All parameters are same as ORG-level Mist Edge Cluster, except in this case configuration will be present on the Site Configuration.
Navigate to Organization > Site Configuration and select/edit a site config
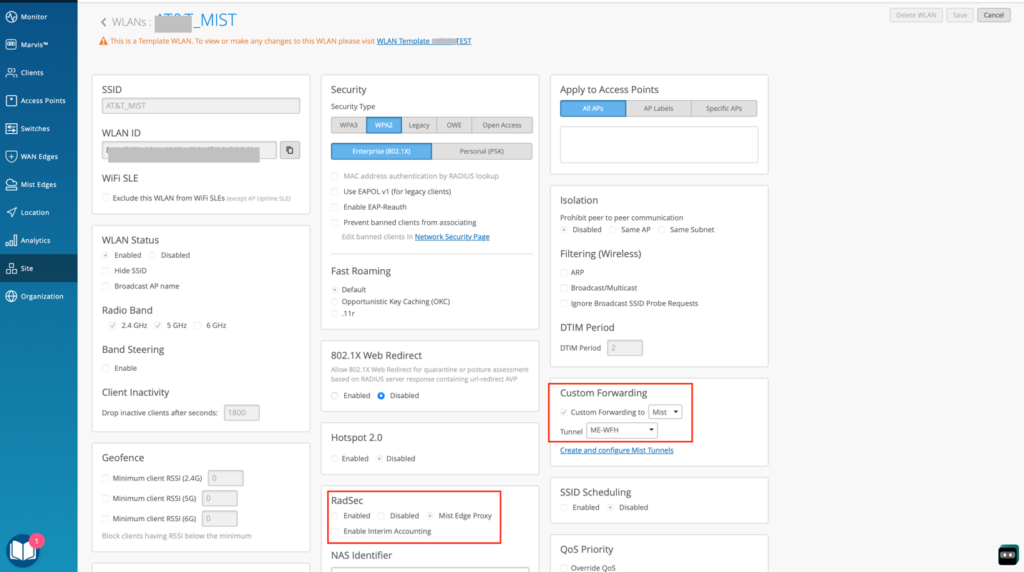
ENABLE radsec to Mist edge proxy on wlan
To complete the configuration, we need to enable 802.1x/MAB authentication on the tunneled wlan and select the Mist Edge Proxy as RadSec server within the wlan configuration.